What is Vigenere Cipher?
Let us take a look at what is going to be discussed in this blog:
Watch this Cybersecurity Course video:
What is Vigenere Cipher?
Vigenere Cipher is an encryption and decryption algorithm. It is a type of polyalphabetic substitution cipher, which means that the cipher alphabet is changed regularly during the encryption process. Due to this, the cipher becomes less vulnerable to cryptanalysis.
The Vigenere Cipher was developed in 1585 by Blaise de Vigenere. He used a Vigenere table or square to encode messages. Let us now take a look at what the Vigenere table is.
Vigenere Cipher Table
It table consists of all the alphabets written 26 times in different rows. Each alphabet in every subsequent row and column is shifted cyclically to the left. This generates 26 Caesar Ciphers.
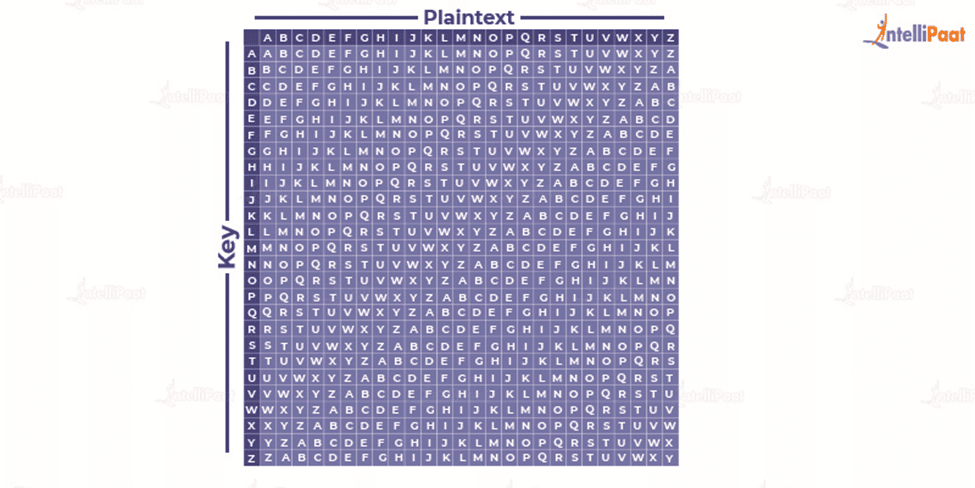
Different alphabets from different rows are used at different points in the encryption process. The alphabet chosen depends on the method used for encryption.
Vigenere Cipher Methods
There are three main Vigenere Cipher Methods:
- Autokey Method
- Keyword Method
- Vigenere Cipher Calculator
Let’s talk about each of these in detail.
Autokey Method
The Autokey Method makes use of the Vigenere Cipher table to encrypt and decrypt the plaintext. In this method, the priming key is just one letter.
Vigenere Cipher Encoder
The first step in the autokey method is to decide on a priming key. Both sender and receiver have to agree on this key. The priming key is the single alphabet that is added to the beginning of messages to help make the key. The sender encrypts the message starting with writing the first letter of the plaintext on one line and the priming key under it. The rest of the plaintext is written as is, shifted one place to the right.
| Plaintext | I | N | T | E | L | L | I | P | A | A | T |
| Key | R | I | N | T | E | L | L | I | P | A | A |
The steps involved are as follows:
- Write the plaintext.
- Use the plaintext and the key letter to select a row and a column in the Vigenere table.
- The first letter of the plaintext is the first row and the key is the first column. For example, if the plaintext is INTELLIPAAT and the key is R, then the first row will be the one that starts with I, and the column will be the one that starts with R.
- The first letter of the ciphertext will be the letter where the first row and column intersect. In the case of our example that will be the letter Z.
- Now, this process is continued till the entire plaintext is turned into a ciphertext. For INTELLIPAAT, that will be ZVGXPWTXPAT.
| Plaintext | I | N | T | E | L | L | I | P | A | A | T |
| Key | R | I | N | T | E | L | L | I | P | A | A |
| Ciphertext | Z | V | G | X | P | W | T | X | P | A | T |
Vigenere Cipher Decoder
The below-mentioned steps are followed to decipher the ciphertext:
- The first letter is selected using the priming key.
- The first letter of the ciphertext is located in this row.
- The first letter of the plaintext will be the letter where the first row and column intersect.
- This process is followed until the entire ciphertext is deciphered.
| Key | R | I | N | T | E | L | L | I | P | A | A |
| Ciphertext | Z | V | G | X | P | W | T | X | P | A | T |
| Plaintext | I | N | T | E | L | L | I | P | A | A | T |
Security
The autokey method for Vigenere Cipher is not very secure. We can only use 26 keys, which makes breaking the code fairly easy. Anyone who wants to break the code needs to only try each alphabet as the priming key before they make a sensible message out of it. This can be done manually in a short time.
Check out this Cybersecurity Tutorial to learn Cybersecurity Essentials!
Keyword Method
The Keyword Method also uses the Vigenere Cipher table to encrypt and decrypt the plaintext. In this method, the key is usually more than one letter.
Vigenere Cipher Encoder
The Vigenere Cipher encoder is similar to the autokey method. The difference is that instead of using just one priming key, the Vigenere Cipher encoder uses a keyword that is more than one letter. So, there are endless possibilities of a possible keyword. The steps involved are as follows:
- The sender will write the keyword repeatedly under the plaintext to form the key.
- This will then be encoded, just like the autokey method, until an entire ciphertext is formed.
For this example, let us use the phrase ALL IS WELL and the keyword as CAKE.
| Plaintext | A | L | L | I | S | W | E | L | L |
| Key | C | A | K | E | C | A | K | E | C |
| Ciphertext | C | L | V | M | U | W | P | P | N |
Vigenere Cipher Decoder
To decode this, the following steps can be followed:
- Start by writing the keyword repeatedly till the length of the ciphertext.
- Write the ciphertext under it and decode it just as is done in the autokey method.
| Key | C | A | K | E | C | A | K | E | C |
| Ciphertext | C | L | V | M | U | W | P | P | N |
| Plaintext | A | L | L | I | S | W | E | L | L |
Security
This method is much more secure than the autokey method, but that does not mean it is not vulnerable. The cipher is more secure with longer keywords.
Vigenere Cipher Calculator
If the Vigenere table is not available or accessible, for whatever reason, then encryption and decryption processes can be carried out using the Vigenere algebraic formula. For this method to work, the alphabets have to be converted into numbers (0-25).
The encryption formula is:
Ei = (Pi + Ki) mod 26
The decryption formula is:
Di = (Ei – Ki) mod 26
Where E is the encipher, D is the decipher, P is the plaintext, and K is the key.
If the value of Di is ever negative, 26 is added to that value.
For example, let us take our plaintext to be CYBER SECURITY.
So,

The key can be BEST.
Encryption: Ei = (Pi + Ki) mod 26

Decryption: Di = (Ei – Ki) mod 26
Remember, if the value of Di is ever negative, 26 is added to that value.

Vigenere Cipher Python Code
Let us take a look at what the Vigenere Cipher calculator will look like as Python code.
#Python code to implement
# Vigenere Cipher
# This function generates the
# key in a cyclic manner until
# it's length isn't equal to
# the length of original text
def generateKey(string, key):
key = list(key)
if len(string) == len(key):
return(key)
else:
for i in range(len(string) -
len(key)):
key.append(key[i % len(key)])
return("" . join(key))
# This function returns the
# encrypted text generated
# with the help of the key
def cipherText(string, key):
cipher_text = []
for i in range(len(string)):
x = (ord(string[i]) +
ord(key[i])) % 26
x += ord('A')
cipher_text.append(chr(x))
return("" . join(cipher_text))
# This function decrypts the
# encrypted text and returns
# the original text
def originalText(cipher_text, key):
orig_text = []
for i in range(len(cipher_text)):
x = (ord(cipher_text[i]) -
ord(key[i]) + 26) % 26
x += ord('A')
orig_text.append(chr(x))
return("" . join(orig_text))
# Driver code
if __name__ == "__main__":
string = "CYBERSECURITY"
keyword = "BEST"
key = generateKey(string, keyword)
cipher_text = cipherText(string,key)
print("Ciphertext :", cipher_text)
print("Original/Decrypted Text :",
originalText(cipher_text, key))
Output
Ciphertext: DCTXSWWVVVAMZ Original or Decrypted Text: CYBERSECURITY
Conclusion
Vigenere Cipher is a simple polyalphabetic substitution method that goes from a simple to advanced method. The Vigenere Square or Table is an important tool used in this Cipher. You can use this cipher in three different ways as per your needs. All the three methods involve different steps. The autokey method is the least secure method. Even though the keyword method has its vulnerabilities, it is more secure than the autokey method. The Python Code method is relatively the most secure method.
The post What is Vigenere Cipher? appeared first on Intellipaat Blog.
Blog: Intellipaat - Blog
Leave a Comment
You must be logged in to post a comment.








