What is the DES Algorithm? Understanding Data Encryption Standard
Let us take a look at the topics that are going to be discussed in this blog:
- What is DES Algorithm?
- Triple DES Algorithm
- DES Algorithm Steps
- DES Modes of Operation
- DES Algorithm Implementation
- Applications of DES Algorithm
- Difference Between AES and DES Algorithms
- Advantages and Disadvantages of DES Algorithm
- Conclusion
Learn more about Cryptography from our YouTube video:
What is DES Algorithm?
The DES Algorithm is a block cipher. It uses symmetric keys to convert 64-bit plaintext blocks into 48-bit ciphertext blocks. The DES Algorithm was developed by the IBM team in the 1970s. It has since been accepted by the National Institute of Standards and Technology (NSIT).
The DES encryption algorithm uses symmetric keys, which means that the same key is used for encrypting and decrypting the data.
Triple DES Algorithm
Triple DES is a block cipher that applies the DES algorithm thrice. It usually uses three different keys—k1, k2, and k3. The first key, k1, is used to encrypt, the second key, k2, is used to decrypt, and the third key, k3, is used to encrypt again.
The triple DES also has a variant that uses only two keys, where k1 and k3 are the same.
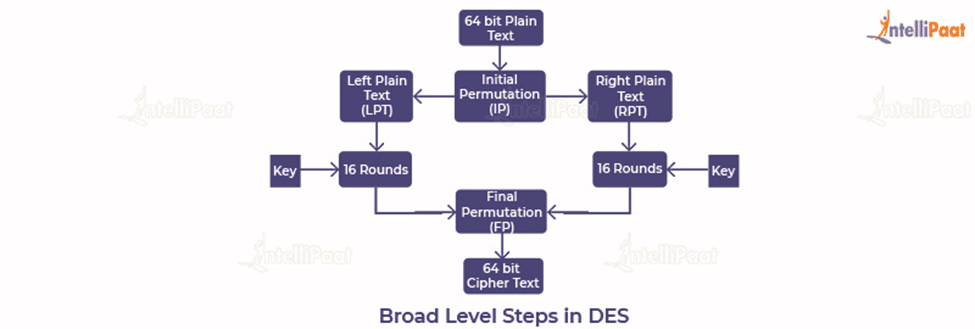
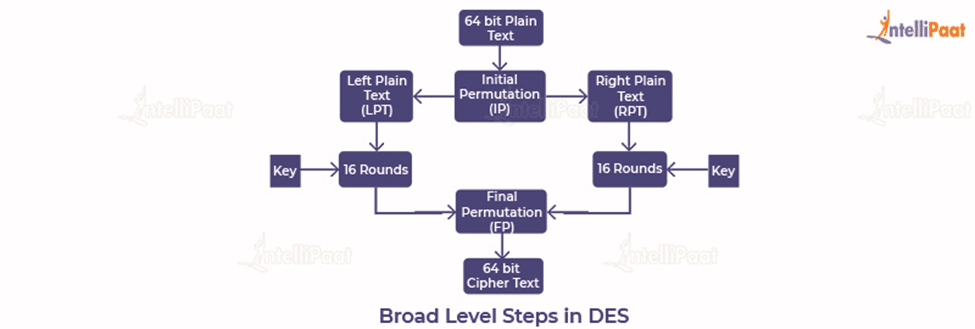
DES Algorithm Steps
Let us take a look at the steps involved in the DES algorithm:
- The initial permutation (IP) function receives the 64-bit plaintext block.
- The IP is performed on plaintext.
- The IP then makes two halves of the block that has been permutated. The two halves are known as left plan text (LPT) and right text (RPT).
- All LPTs and RPTs are encrypted 16 times.
- The LPT and RPT are joined, and then the final permutation (FP) is performed on this block.
- The 64-bit ciphertext is now ready.
In the encryption process (step 4), there are five stages:
- Key transformation
- Expansion permutation
- S-Box permutation
- P-Box permutation
- XOR, and swap
In the decryption process, the same algorithm is used with the order of the 16 keys reversed.
Check out this Cybersecurity Tutorial to learn Cybersecurity Essentials!
DES Modes of Operation
The following are the different DES modes of operation to choose from:
- Electronic Codebook (ECB): In this mode, each block of 64-bits is independently encrypted and decrypted.
- Cipher Block Chaining (CBC): In this mode, each block of 64-bits is dependent on the one before it. It uses an initialization vector (IV).
- Cipher Feedback (CFB): In this mode, the previous ciphertext is used as the input for the encryption algorithm. This produces a pseudorandom output. This output is then XORed along with the plaintext. This creates the next ciphertext unit.
- Output Feedback (OFB): This mode is like CFB, except for the fact that the input for the encryption algorithm is the output of the previous DES.
- Counter (CTR): In this mode, every block of plaintext gets XORed with a counter that has been encrypted. The counter is incremented for every next block.
Career Transition
DES Algorithm Implementation
You need a security provider to implement the DES algorithm. There are many providers that are available in the market, and it is crucial to select one as the first step of the implementation process. The provider you select will depend on the language being used by you. This can be MATLAB, C, Python, or Java.
Once you have selected the provider, you have to decide how the key is going to be generated. You can have the key randomly generated by the key generator or you can create a key on your own. You can use either plaintext or a byte array for this purpose.
It is crucial to test the encryption so you can be assured of its proper implementation.
Want to get an Advanced Certification in Cybersecurity? Enroll today!
Applications of DES Algorithm
The DES algorithm is used whenever a not-very-strong encryption is needed. It can be used in random number generators or even as a permutation generator. One of the most important practical applications of the DES algorithm is to create triple DES legacy systems with three keys.
Difference Between AES and DES Algorithms
AES and DES are both symmetric ciphers. So, what is the difference between them? Let us find out.
| Parameter | AES | DES |
| Meaning | AES stands for advanced encryption standard. | DES stands for data encryption standard. |
| Key Length | The key length can be 128 bits, 192 bits, or 256 bits. | The key length is 56 bits. |
| Rounds of Operations | The rounds of operations per key length are as follows: 128 bits: 10 192 bits: 12 256 bits: 14 | There are 16 identical rounds of operations. |
| Network | AES is based on a substitution and permutation network. | DES is based on the Feistel network. |
| Security | AES is considered the standard encryption algorithm in the world and is more secure than DES. | DES is considered to be a weak encryption algorithm; triple DES is a more secure encryption algorithm. |
| Rounds | Key Addition, Mix Column, Byte Substitution, and Shift Row. | Substitution, XOR Operation, Permutation, and Expansion. |
| Size | AES can encrypt plaintext of 128 bits. | DES can encrypt plaintext of 64 bits. |
| Derived from | AES was derived from the Square Cipher. | DES was derived from the Lucifer Cipher. |
| Designed by | AES was designed by Vincent Rijmen and Joan Daemen. | DES was designed by IBM. |
| Known Attacks | There are no known attacks for AES. | Brute force attacks, differential cryptanalysis, and linear cryptanalysis. |
Learn Ethical Hacking from MNIT faculty! Enroll today!
Advantages and Disadvantages of DES Algorithm
Let us take a look at the advantages and disadvantages of the DES Algorithm.
Advantages of DES Algorithm
The advantages are as follows:
- The algorithm has been in use since 1977. Technically, no weaknesses have been found in the algorithm. Brute force attacks are still the most efficient attacks against the DES algorithm.
- DES is the standard set by the US Government. The government recertifies DES every five years, and has to ask for its replacement if the need arises.
- The American National Standards Institute (ANSI) and International Organization for Standardization (ISO) have declared DES as a standard as well. This means that the algorithm is open to the public—to learn and implement.
- DES was designed for hardware; it is fast in hardware, but only relatively fast in software.
Disadvantages of DES Algorithm
The disadvantages are as follows:
- Probably the biggest disadvantage of the DES algorithm is the key size of 56-bit. There are chips available that can encrypt and decrypt a million DES operations in a second. A DES cracking machine that can search all the keys in about seven hours is available for $1 million.
- DES can be implemented quickly on hardware. But since it was not designed for software, it is relatively slow on it.
- It has become easier to break the encrypted code in DES as the technology is steadily improving. Nowadays, AES is preferred over DES.
- DES uses a single key for encryption as well as decryption as it is a type of symmetric encryption technique. In case that one key is lost, we will not be able to receive decipherable data at all.
Conclusion
DES is a symmetric block cipher that can be used to encrypt 64-bits of plaintext into 64-bits of ciphertext. The algorithm is the same for the process of encryption as well as decryption. The only difference is that the decryption procedure is the opposite of the encryption procedure. The algorithm goes through 16 rounds and makes it stronger. Now, even though there are much stronger encryption algorithms available, learning about DES is still important as it helped in the advancement of cryptography as we know it today.
Check out our Cyber Security interview question now and start preparing for your next job interview!
The post What is the DES Algorithm? Understanding Data Encryption Standard appeared first on Intellipaat Blog.
Blog: Intellipaat - Blog
Leave a Comment
You must be logged in to post a comment.