What is Supply Chain Attack?
With supply chain attacks, attackers can gain access to sensitive data, steal intellectual property, or even take control of entire systems. However, there are ways to protect your business from these types of attacks! By implementing strong security measures, such as network segmentation. Let’s know more about access control and regular software updates, which can reduce the risk of a supply chain attack and keep your systems and data safe.
- Introduction to Supply Chain Attacks
- How Supply Chain Attacks Work?
- How Do You Detect Supply Chain Attacks?
- How to Prevent Supply Chain Attacks?
- Examples of Supply Chain Attacks
- Conclusion
Watch this youtube video before reading ahead, to get a clear understanding of the topics to be covered next.
{
“@context”: “https://schema.org”,
“@type”: “VideoObject”,
“name”: “video”,
“description”: “What is Supply Chain Attack?”,
“thumbnailUrl”: “https://img.youtube.com/vi/4RE4d23tDFw/hqdefault.jpg”,
“uploadDate”: “2023-06-06T08:00:00+08:00”,
“publisher”: {
“@type”: “Organization”,
“name”: “Intellipaat Software Solutions Pvt Ltd”,
“logo”: {
“@type”: “ImageObject”,
“url”: “https://intellipaat.com/blog/wp-content/themes/intellipaat-blog-new/images/logo.png”,
“width”: 124,
“height”: 43
}
},
“contentUrl”: “https://www.youtube.com/watch?v=4RE4d23tDFw”,
“embedUrl”: “https://www.youtube.com/embed/4RE4d23tDFw”
}
Introduction to Supply Chain Attacks
A supply chain attack is a type of cyberattack that targets the software supply chain, which is the network of vendors and suppliers that provide the software and hardware components that make up modern technology products.
- A supply chain attack targets the software supply chain, which is the network of vendors and suppliers that provide the software and hardware components that make up modern technology products.
- The attacker infiltrates an upstream supplier or vendor in the supply chain and inserts malicious code or a backdoor into the software or hardware that they provide.
- The attack can then spread downstream to infect the products of all the suppliers and vendors that rely on the compromised component.
- Supply chain attacks can have devastating consequences, compromising the security of large numbers of organizations and individuals.
- Supply chain attacks can be difficult to detect and mitigate, as the initial point of compromise may be far removed from the ultimate target of the attack.
- High-profile examples of supply chain attacks include the SolarWinds attack in 2020 and the NotPetya attack in 2017.
- As technology products become more complex and interconnected, the risk of supply chain attacks is likely to continue to grow.
Become a CyberSecurity Expert. Enroll today in this Cyber Security Course and gain the knowledge you need.
How Supply Chain Attacks Work?
Supply chain attacks work by exploiting the trust that organizations place in their suppliers and vendors. Here’s a more detailed explanation of how these attacks can be carried out:
- Initial compromise – The attacker gains access to an upstream supplier or vendor in the software supply chain, often by exploiting a vulnerability in their systems or through social engineering techniques.
- Malicious code insertion – Once inside the supplier’s systems, the attacker inserts a malicious code or backdoor into the software or hardware components that they provide.
- Distribution – The compromised component is distributed downstream to all the suppliers and vendors that rely on it. The malicious code or backdoor may be hidden within legitimate-looking software updates or other components.
- Activation – Once the attacker activates the malicious code or backdoor, it helps them get access to every detail. This eventually allows them to gain access to the systems of all the organizations that are connected to the targeted system or use the compromised component.
- Data theft or other malicious activities – After gaining access to the target systems, the attacker can perform diversified malicious activities, including stealing sensitive data, launching ransomware attacks, or conducting espionage.
- Difficult detection – These attacks can be difficult to detect, as the initial point of compromise may be far removed from the ultimate target of the attack. Additionally, the malicious code or backdoor may be designed to evade detection by security software.
Supply chain assaults can have major ramifications, jeopardizing the security of countless organizations and individuals. To detect and avoid these types of attacks, organizations must properly assess their suppliers and vendors and establish strong security measures.
Master the essentials of CyberSecurity with our comprehensive Cyber Security Tutorial. Start learning now and protect digital assets!
How Do You Detect Supply Chain Attacks?
Detecting supply chain attacks can be difficult, as they often involve sophisticated tactics and techniques. However, there are several indicators that organizations can look for that may indicate a supply chain attack, including
- Unusual Network Traffic – A spike in network traffic or unexpected network activity could indicate that an attacker has acquired network access.
- Unexpected Software Changes – Unexpected changes to software or hardware may signal that an attacker has installed malware or made unauthorized changes to the system.
- Unusual Login Activity – Unusual login behavior or attempts to access sensitive data could signal that an attacker has gained network access.
How to Prevent Supply Chain Attacks?
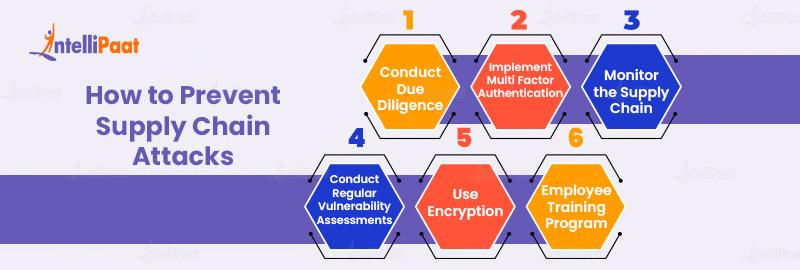
Preventing supply chain attacks requires a multi-pronged approach that involves both proactive measures and ongoing monitoring. Here are some steps that organizations can take to prevent supply chain attacks:
- Conduct Due Diligence – It is critical to undertake due diligence before dealing with a new supplier or vendor to ensure that they have solid security policies in place. This may entail examining their security rules, doing vulnerability assessments, and completing background checks.
- Monitor the Supply Chain – Continuous supply chain monitoring is required to detect and respond to supply chain assaults. This can include keeping an eye out for unusual activities, conducting frequent vulnerability assessments, and putting in place a solid incident response strategy.
- Implement Multi-Factor Authentication – Multi-factor authentication can help prevent unauthorized access to the network by requiring users to provide additional verification before accessing sensitive data.
- Use Encryption – Encryption can help protect sensitive data from being intercepted or compromised by attackers.
- Conduct Regular Vulnerability Assessments – Regular vulnerability assessments can help identify and address vulnerabilities in the supply chain before they can be exploited by attackers.
- Employee Training Program – Employee training is mandatory to prevent any kind of supply chain attack. Employees should be experts in such cases and be aware of how to identify and report suspicious activity.
Prepare for your CyberSecurity interview with our comprehensive Cyber Security Interview Questions bank. Get started now!
Examples of Supply Chain Attacks
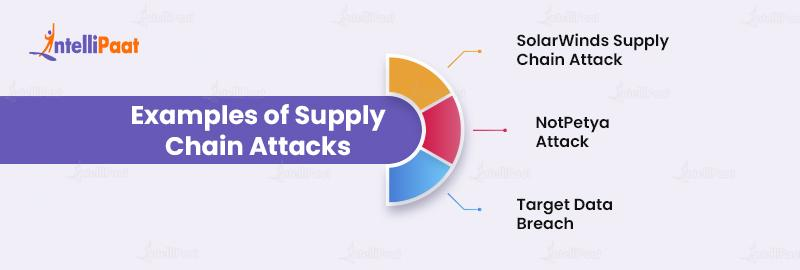
Supply chain attacks have become increasingly prevalent in recent years, and there have been several high-profile examples of these attacks. Some of the most well-known supply chain attacks are elaborated further:
- SolarWinds Supply Chain Attack – The referred attack compromised the security of SolarWinds, a software company that provides IT management software to government agencies and Fortune 500 companies. The attackers were able to infiltrate SolarWinds’ software and install a backdoor that allowed them to access the networks of SolarWinds’ customers.
- NotPetya Attack – This attack targeted a Ukrainian accounting software company’s supply chain, which was used by various multinational corporations. The attackers were successful in installing malware that quickly propagated across the supply chain, incurring billions of dollars in damage.
- Target Data Breach – Target Corporation, a prominent US retailer, was the target of this attack via its supply chain. The attackers gained access to Target’s network by breaching one of its suppliers’ security and planting malware on Target’s point-of-sale systems.
Level up your CyberSecurity skills with our Ethical Hacking course. Enroll now and become a Certified Ethical Hacker!
Conclusion
Attacks on supply chains can pose a substantial risk to networks and have major ramifications for everyone involved. But don’t worry, there are ways to protect against them! By adopting a proactive approach to security and employing best practices to prevent and identify supply chain risks, organizations can preserve the security of their networks and safeguard the safety of sensitive data. Protect your network from supply chain attacks with a proactive approach to security and stay up-to-date with the latest cybersecurity trends and best practices!
If you have any additional questions, please post them on our Community page, and we will do our best to answer them.
The post What is Supply Chain Attack? appeared first on Intellipaat Blog.
Blog: Intellipaat - Blog
Leave a Comment
You must be logged in to post a comment.







