What is Steganography? A Complete Tutorial
Apart from covering the Steganography definition, this tutorial will also run through its types, working, applications, and also how it can be detected in the first place.
- What is Steganography?
- Who uses Steganography?
- How does Steganography work?
- Types of Steganography
- Detecting Steganography
- Difference between Steganography and Cryptography
- Steganography Tools
- Steganography Applications Today
- Conclusion
Most of us are familiar with a large number of steganographic methods such as microdots, invisible ink, and many more. Let us dive into more details on this subject matter.
Watch this tutorial by Intellipaat that covers Steganography in detail.
What is Steganography?
Steganography refers to the practice of hiding a secret message inside or camouflaging it on top of something that is in plain sight. More recently, Steganography has started to involve embedding hidden texts in images or plating secret messages or scripts in a Word document or an Excel sheet.
Steganography can make use of any medium to hide messages. If you are thinking of cryptography, let me stop you right here. Steganography, unlike cryptography, does not involve scrambling of data, which involves a key. This form of hiding information can be cleverly executed in several ways.
Cryptography enables privacy, while Steganography involves secrecy as well as deceit.
Now that we know what Steganography is, let us understand what its purpose is. As is quite apparent, the purpose is primarily to conceal or deceive. It is, after all, a form of covert communication.
Steganography Examples
Steganography uses careful techniques to hide the fact that a certain content exists. There are several creative ways to execute it, and it can be used with a variety of latest technologies. Here are a few examples:
- A hidden message that can be revealed by playing a video at a faster frame rate
- Content that can be unveiled by playing an audio track backward
- Embedding a message into an RGB image by hiding it in the red, green, or blue channel
- Adding noise or sound to encrypt a message within a photo
- Hiding content within the file header or metadata
A simpler example is a message in plain text. For example, in the following sentence, the first letter of each word reveals the word hidden:
Harriette is definitely done entertaining nonsense.
Take a Cyber Security Course and learn how you can secure your systems and network.
Who uses Steganography?
Steganography is typically used by hackers who want to embed malicious code. They do so by altering an ordinary bit of a file and inserting malicious code in it. Once a user unintentionally downloads the code by opening a file or image, the malware is activated and the hacker gains control of the user’s network or the malware corrupts the content. The steganographic file is so subtly different from the original that it cannot be immediately detected.
Steganography is used by malicious attackers to execute a wide range of tasks such as hiding malicious payloads and script files. Malware developers use Least Significant Bit (LSB) Steganography for hiding code for their malware in images of famous people or famous songs. These codes are, then, executed with another program after the file is downloaded to the target computer system.
Cybercriminals are not the only ones who use Steganography. Spies use it to covertly communicate with their command center without arousing suspicion among their hosts. Some human rights activists and nonconformists also tend to utilize this method to share sensitive information.
How does Steganography work?
The way that Steganography works is that it hides information so that it does not arouse suspicion. One of the most popular techniques is the LSB Steganography that we talked about earlier. In this type of Steganography, secret information is embedded in the least significant parts of a media file.
For instance, each pixel of an image file is made up of three bytes of data that correspond to the colors red, green, and blue; some image formats allocate an additional fourth byte to transparency or alpha. What LSB Steganography does is change the last bit of each of those bytes to hide one bit of data. So, in order to conceal 1 MB of data, an 8 MB image file is required.
Modifying the last bit of pixel value does not visually change the picture as the viewer will not be able to tell the difference. In the same way, data can be hidden in different parts of audio files and videos without changing the audible or visual output.
A less popular form of Steganography is through letter or word substitution. The sender hides the text by distributing it inside a longer text and placing the text at specific intervals, thus forming a pattern that needs to be decoded. It is a fairly simple technique.
One can also hide an entire partition on a hard drive or insert data in a file’s or network packet’s header section.
The effectiveness of these techniques is based on how much data can be hidden and the difficulty level of detection.
Steganography Techniques
Steganography techniques conceal messages to the best possible extent and reveal them only at the desired destination. Below are a few concealing techniques used in Steganography:
- LSB: We have already discussed this technique above. The least significant bits of data are identified in the original file and replaced with secret information or, in most cases, malicious code. The user who downloads the file will have the malware introduced in their system allowing the attacker to access the device.
Sandboxes are capable of detecting such corrupt files. However, hackers always find new means, such as sleep patching, to bypass detection measures. - Palette-based technique: In this technique, digital images are used as malware carriers and attackers encrypt and conceal a message in a wide palette of the cover image. Despite its limited data capacity, palette-based technique can still be a headache for cybersecurity professionals as it takes time to decrypt the data.
- Secure cover selection: Secure cover selection is quite a complex technique of Steganography that is used by cybercriminals. They have to compare blocks of the original image to specific blocks of a specific malware. An exact match is required to carry the malware. The identical match is fitted into the original image, which makes it extremely difficult to detect the malware with cybersecurity software or software applications.
Enroll in Intellipaat’s Ethical Hacking Course today! and build a career in Cybersecurity.
Types of Steganography
Some bytes in files or images are not required. These can be replaced with a message without damaging the original file. Secret messages are hidden in this way. Let us explore some of the most common types of Steganography.
Image Steganography
Nowadays, digital images are widely used and in various formats. Different formats use different algorithms altogether. Listed below are some common ones are:
- Masking and filtering: Masking and filtering operations are carried out to mark the carrier image, somewhat like a watermark
- Redundant pattern encoding (RPE): It uses more than one graphic or visual structure, such as color + position, to encode one variable of data
- LSB insertion: It replaces the least significant bit of a media file with hidden content
- Encrypt and scatter: It hides the message as white noise
- Algorithms and transformations: It makes use of algorithms to conceal information in an image
Audio Steganography
Embedding a secret message within an audio file is the most difficult task as the human brain has a wide range of auditory capacity. A few audio Steganography methods that are used are:
- Spread Spectrum: In this type of Steganography, a signal that is generated with a particular bandwidth is spread in the frequency domain to get a wider bandwidth than the carrier message.
The wider bandwidth, however, maintains the same signal power, and the signal is extremely difficult to distinguish from the noise due to the unclear peak in the spectrum. Hence, it makes for secure communication. - Parity Coding: In this type of Steganography, the carrier audio signal is split into separate samples and the secret message is concealed in the parity bit of each sample area. If the parity bit does not match with the hidden message bit, then the LSB of the sample area is inverted.
- Phase Coding: In this type of Steganography, the phase of the carrier file is replaced with a reference phase that represents the concealed data.
- LSB Coding: This type of Steganography involves substituting the LSB of each sampling point with a binary message, thus allowing the encoding of a large amount of data. The ideal data transmission rate is 1 Kbps per 1 kHz.
- Echo Hiding: This type of Steganography allows the embedding of data into the host audio through the introduction of a short echo. The echo is in the form of resonance added to the host signal. After the echo is introduced, the stego signal retains the statistical and perceptual characteristics of the carrier audio.
The data can be hidden by manipulating the three parameters of the echo signal, the initial amplitude, the offset delay, and the decay rate so that the echo is not audible. Thus, data is hidden in this manner without being perceptible.
Video Steganography
In video Steganography, supplementary data is embedded into the carrier video file that will hide the secret message. This is executed through LSB insertion or real-time video Steganography.
Career Transition
Steganography in Documents
Steganography in documents focuses on modifying the characteristics of a document. A few ways to achieve this are:
- Adding white space and tabs toward the end of the lines and hiding information in plain text
- Using the same background and font color for writing and using the extremely small size of fonts in Microsoft Word documents
- Using a broadly available cover source, a newspaper or book, and using a code that contains a combination of letters, numbers, or line numbers. The only way to decode the information inside the cover source is by having access to the key.
Detecting Steganography
Security analysts are professionals who attempt to identify the tactics, techniques, and procedures (TTPs) of attackers and pen testers. Security analysts are well-learned in the typical signatures of steganographic applications used over the years. Antivirus applications are a good example of how security analysts can detect typical activities of steganographic applications.
Attackers and pen testers alter and modify their strategies to avoid detection, turning the entire process into a game of cat and mouse. Attackers constantly change their techniques and tools, while security analysts keep looking for new methods and signatures.
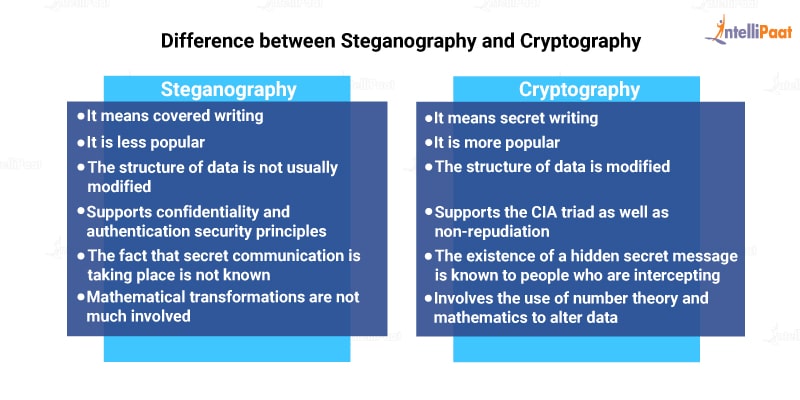
Difference between Steganography and Cryptography
Steganography is often confused and compared with cryptography. Steganography is used for concealing information, while cryptography is more focused on rendering content unreadable for everyone unless it is the intended recipient. Encrypted data is only accessible with the help of a decryption key.
Now, you must be wondering why use Steganography if cryptography provides better data protection. Well, the presence of cryptography itself reveals that something hidden exists. As a matter of fact, in most cases, the sender raises suspicion and gets into trouble. Cryptographic files are detectable.
Even the most secure crypto is worthless if the key is in hand. When it comes to matters of national security especially, robbing the key for sensitive information is not unheard of.
So, you can guess which technique is more feasible.
Steganography in Cryptography
Sometimes, both Steganography and cryptography are used together. While the concept of both is quite different, they are mutually inclusive. In Steganography, data within a carrier file does not necessarily have to be in clear text. It is possible to conceal encrypted data with steganography as well. Even if the hidden data is discovered, it will still need to be decrypted to uncover its content.
Steganography Tools
Steganography software tools allow a user to hide information in a carrier file. Many tools are available that offer Steganography. While some offer normal Steganography, others provide encryption before hiding the data. A few tools can only hide the data behind an image, but others are able to use any type of file.
Courses you may like
Listed below are a few Steganography software that are available for free:
- Xiao Steganography
- Image Steganography
- Steghide
- Crypture
- SteganographX Plus
- Camouflage
- OpenStego
- SteganPEG
- Hide’N’Send
- rSteg
- SSuite Picsel
- Our Secret
Prepare for your upcoming job interview with us! Go through this blog on Cyber Security Interview Questions and excel your hiring journey!
Steganography Applications Today
A few of the applications of Steganography are:
- Covert communication and data storing: In practice, the first thing to do is to select a vessel data that can accommodate the size of the data to be embedded. The vessel should have an ordinary and innocuous feel. Using an embedding program, the confidential data is embedded with a key. To extract the data, an extracting program and key are used. A key negotiation should be settled with the party before starting this form of confidential communication.
Private journal writing is one of the simplest application examples. A steganographic file is attached to an email message. However, this method of sending and receiving is not discreet.
Some communication methods are much more confidential where there is also a method where there is no requirement for key negotiation. Such communication methods use web pages. This method is especially effective if you want to avoid detection.
The embedding process of secrecy-based applications leaves traces of evidence. In those scenarios, either a larger vessel is chosen or the original vessel is entirely discarded after embedding.
- Protecting data modifications: In this area of application, advantage is taken of the fragility of the embedded data. In most Steganography programs, the embedded data is fragile. Tools such as Qtech Hide & View do fragile embedding of data. However, in an unexpected way, this very disadvantage introduced an information-alteration protective system, digital certificate document system.
Digital certificate data can be sent anywhere in the world through the internet and no one will be able to forge, alter, or tamper with it. If modified in any way, it is easily detectable by the extraction program.
- Access control system in content distribution: In this application of Steganography, the embedded data is hidden, but the content is publicized and access is controlled. Today, everything is digitized and distributed over the internet. While email is a simple option, it is not feasible in the case of content distribution scenarios such as music album releases.
Emailing each and everyone can be an arduous task. A steganographic scheme can overcome this through access control. To extract the content, one only needs to have the access key.
- Media database systems: In this application of Steganography, secrecy is not given much importance. The focus is rather on the process of unifying two types of data into one. Generally, media files have associated data with them such as the title of the media, information on the physical object, date, time, camera model, photographer information, etc.
Consider a digital camera; it’s cheap, easy-to-use, and quick to shoot. Eventually, people lost the drive to annotate each and every picture due to large amounts. It is extremely difficult if you are looking for a specific shot. In most photo album software or media database systems, a problem arises with the metadata of images as it is separated from the media or photo data.
Steganography solves this problem and unifies the two types of data into one with the embedding operation. This results in the easy transfer of metadata from one system to another without any issues.
Conclusion
Steganography is more of a concept than a method of data delivery by secretive methods. This makes the application of Steganography easier in more than one clever way. Steganography is significantly more sophisticated than before. It is often paired with cryptography for double protection.
Hung up with doubts? Ask them out in our Cyber Security community right away!
The post What is Steganography? A Complete Tutorial appeared first on Intellipaat Blog.
Blog: Intellipaat - Blog
Leave a Comment
You must be logged in to post a comment.














