What is SIEM?
We are going to be discussing the following topics in this blog:
- What is SIEM (Security Information and Event Management)?
- SIEM Process
- SIEM Architecture
- How Does SIEM Work?
- SIEM Capabilities
- Top SIEM Tools
- Benefits of SIEM
- Limitations of SIEM
- How to Choose a SIEM Solution?
- SIEM Vendors
- Steps for Planning a SIEM Project
- Conclusion
Watch this Cyber Security course video:
What is SIEM (Security Information and Event Management)?
SIEM combines security event management (SEM) with security information management (SIM). SEM analyzes logs and events data and helps in providing threat monitoring, incident response, and event correlation. SIM, on the other hand, reports, collects, and analyzes log data.
SIEM Definition
SIEM is a software solution that helps monitor, detect, and alert security events. It presents a centralized view of the IT infrastructure of a company. It also helps cyber security professionals to gain insights into the ongoing activities in their IT environments.
Enroll in our Cyber Security course and master SIEM now!
SIEM Process
Four steps are involved in the SIEM process:
- Collect data from various sources—network devices, servers, domain controllers, etc.
- Normalize and aggregate collected data
- Analyze the data to detect and discover threats
- Pinpoint security breaches and enable companies to investigate alerts
SIEM Architecture
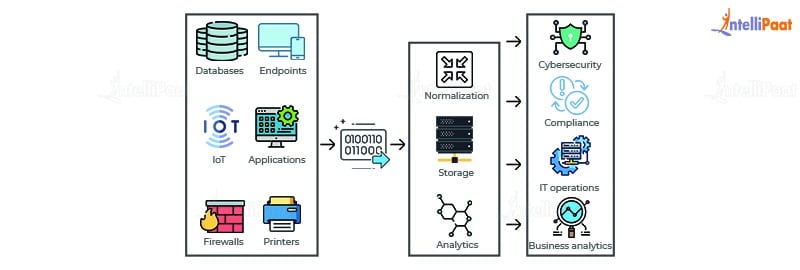
SIEM architecture is concerned with building SIEM systems and its core components. SIEM architecture includes the following components:
- Management of logs
- Normalization of logs
- Sources of logs
- Hosting choices for SIEM network
- Reporting of SIEM products
- Real-time SIEM monitoring of SIEM security
Check out this Cyber Security Tutorial to learn Cyber Security Essentials!
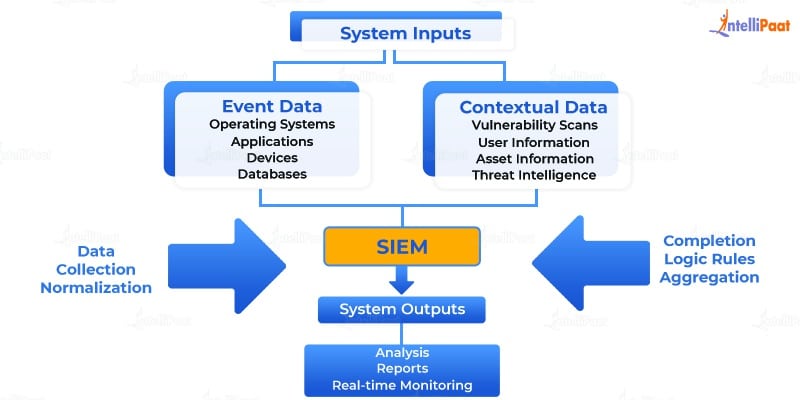
How Does SIEM Work?
SIEM software is responsible for collecting and aggregating log data that is created by companies. This comes from network and security devices, host systems, etc.
After that, the SIEM software works at identifying, analyzing, and categorizing all events and incidents. The SIEM software usually has two main goals:
- To create reports on all security events and incidents
- To alert if an activity is running against a predetermined set of rules, indicating a possible security issue
The need for better compliance management and greater security measures have been the major driving force behind the adoption of SIEM solutions. These days, large companies base their security operations center on SIEM.
SIEM Capabilities
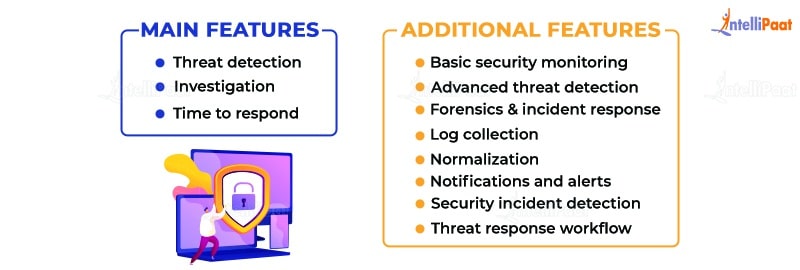
There are three critical SIEM capabilities:
- Threat detection
- Investigation
- Time to respond
There are a few additional features that are available in the SIEM security market:
- Basic security monitoring
- Advanced threat detection
- Forensics and incident response
- Log collection
- Normalization
- Notifications and alerts
- Security incident detection
- Threat response workflow
Looking for various courses in Cyber Security? Have a look at our Cyber security course catalog now!
Career Transition
Top SIEM Tools
The following are some of the top SIEM tools in the market:
- Splunk
Splunk is an on-premises SIEM tool that helps with monitoring security and detecting advanced threats. - IBM QRadar
IBM QRadar is an SIEM solution that can be used as a virtual, software, or hardware appliance. - LogRhythm
LogRhythm is an SIEM tool that is suitable for small companies. It helps with threat detection and response.
Benefits of SIEM
We cannot have a capable cybersecurity team without SIEM solutions. There are seven crucial benefits of a modern SIEM solution:
- Collects and analyzes data from all sources in real time
There is a lot of data being generated every day. To keep up with it, SIEM tools have to take in data from every source, so they can detect, monitor, and respond to threats effectively. Modern SIEM tools can provide better analytics with more data. More data tends to make SIEM tools more effective. - Utilizes machine learning to add context and situational awareness to help increase efficiency
Attacks have become more sophisticated these days. This means that companies trying to defend themselves need advanced tools. Compromised credentials are often used by attackers to harm companies. SIEM tools are now equipped with machine learning capabilities. This helps in identifying threats quickly and enables threat monitoring from internal as well as external threats. - Flexible and scalable architecture improves time to value
With the amount of data coming in, companies need to have big data architecture that is both scalable and flexible. This will help companies to adapt and grow their business as it changes over time. SIEM solutions can handle complex implementation and are capable of being deployed in the virtual environment, in the cloud, or on premises. - Provides enhanced investigation and incident response tools
SIEM solutions are capable of providing clear analytics that help improve decision-making and response time. Data visualization and business context can help analysts interpret and respond to data in a better manner. As analytics get better, teams will be able to manage incidents better and improve forensic investigations. - Makes security analysts more productive
SIEM solutions provide use cases after the log is collected. This helps the security team to detect and respond to threats quickly. This helps security analysts become more productive. - Reduces cybersecurity staff requirements
Security teams these days are time-constrained. Analysts can save time with the help of enhanced automated tasks. Top SIEM tools can provide unsupervised machine learning that helps ease the burden of overworked security analysts. Threat detection is automated, contexts are enhanced, and user behavior is utilized to gain better insights. - Comes with predictable pricing
Modern SIEM pricing models are based on how many devices send logs. This means that companies do not have to worry about how much data they are using. Some SIEM vendors have additional costs for increasing hardware capacity or how many users are accessing the device.
Enroll in our Cyber Security course in Bangalore now to learn Cyber security if you are living nearby Bangalore!
Limitations of SIEM
The following are some of the limitations of SIEM tools:
- SIEM security applications do not provide a lot of contextual information about the native needs.
- SIEM has a blind spot for unstructured data.
- SIEM applications fail to distinguish between sensitive and non-sensitive data. This means that they are unable to tell the difference between sanctioned file activities and suspicious activities. This could cost customer data, company security, or intellectual property.
- In SIEM, it can be very difficult to research and diagnose security events.
How to Choose a SIEM Solution?
Before companies choose a SIEM solution, they need to define the scope and timeline of the project. This can be done by organizing workshops, either internally or externally, in collaboration with a SIEM partner. The first step toward identifying the scope and timeline is to identify a list of use cases. This will indicate the necessary log sources. Deciding on a timeline is also necessary to make sure that the SIEM security aligns with a company’s objectives.
There are four questions that companies need to consider while choosing a SIEM solution:
- What applications should you focus on?
- How should you respond when threats are detected?
- Where are the most critical threats located in your environment?
- Why are these threats the most critical and what impact would a breach have?
Have a look at our Ethical Hacking course online now to learn ethical hacking from experts!
Courses you may like
SIEM Vendors
The SIEM market has some dominant vendors worldwide, namely IBM, Splunk, and HPE. There are some other big names in the market as well such as Intel, Alert Logic, ManageEngine, LogRhythm, Solar Winds, Trustwave, and Micro Focus.
When choosing a SIEM vendor, companies need to examine the vendors based on the organizational goals as this would help the companies figure out which vendor would suit them the best. If a company wants SIEM technology primarily for compliance purposes, then it would look for capabilities such as reporting; on the other hand, if a company wants SIEM technology to help with setting up a security operations center, then the company would look for other capabilities such as security monitoring and threat detection.
Steps for Planning a SIEM Project

There are three steps for planning a SIEM project:
- Determine critical data sources for your business
After you have decided the scope of your projects, it becomes easier to identify log sources within the scope. This can help you determine how you can obtain the required relevant data. - Identify all high priority events and alerts
The list of security events is growing every day with the need of analyzing them and acting on them. SIEM is used to generate more insights from events and data. Companies have to first determine their high priority events and how they can be derived from the devices and applications within the infrastructure. This helps SIEM security teams to spend more time on critical alerts and incidents. - Determine your key success metrics
SIEM integration should align with your business objectives. You need to determine the key success metrics to ensure you can maximize the return on investment (ROI). Companies need to figure out what success is for them and how they can use SIEM use cases to achieve it.
Conclusion
SIEM is an important software solution for companies. We have seen how the SIEM process works and what are the important architectural components. There are some dominant SIEM tools around the world. Every SIEM system has benefits and drawbacks of its own. Companies can choose a SIEM platform according to their needs.
Preparing for job interviews? Go through our Cyber Security interview questions and excel your next job interview!
The post What is SIEM? appeared first on Intellipaat Blog.
Blog: Intellipaat - Blog
Leave a Comment
You must be logged in to post a comment.













