What is Session Hijacking?
You will be learning the following topics through this blog –
- What is a Session?
- What is Session Hijacking?
- Difference Between Session Hijacking And Spoofing
- Session Hijacking Techniques
- How can an Attacker take Advantage of a Successful Session Hijack?
- Session Hijacking Example
- Why is Encryption Important?
- How to Prevent Session Hijacking?
- Tools to Reduce the Risk of Session Hijacking Attack
- Conclusion
What is a Session?
A session is a series of interactions that take place within a single connection between two communication endpoints. A web application does not require authentication for every click since, HTTP is stateless, which means designers need to automate tracking the state of multiple connections from the same user.
When a user logs into an application, a session is created on the server to ensure subsequent requests are synchronized.
Check out tutorial videos on Cyber Security on YouTube by Intellipaat
The application uses sessions to keep track of parameters that are unique to the user. As long as the logged-in user remains, the session is kept “alive” on the server. After a certain period of inactivity, a session is destroyed immediately upon the user logging out of the system. Data belonging to the user should be deleted from the allocated memory space whenever a session terminates.
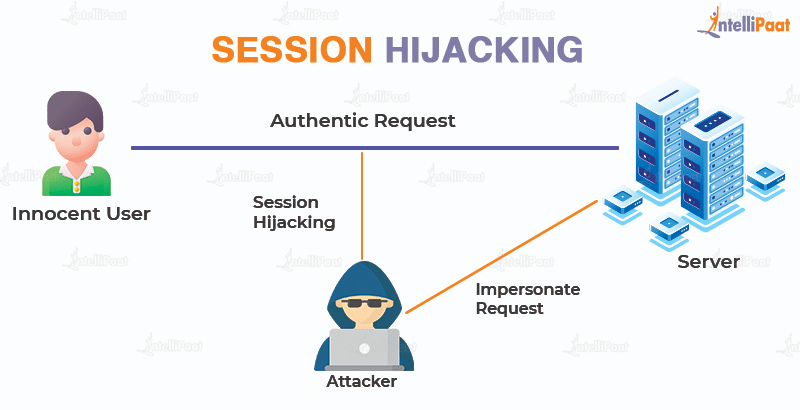
What is Session Hijacking?
An attacker hijacks a user session to gain control over it. A session starts when you log in and out of a service, like your bank’s application. A cookie hijack or cookie side-jacking is an attack that relies on an attacker knowing your session cookie. Session hijacking is commonly associated with web browsers and web applications, yet it can happen with any application.
Sign up for Intellipaat’s Cyber Security Course to become an expert in the field.
Difference Between Session Hijacking And Spoofing
Session hijacking and spoofing are closely related, but the timing of their attacks differs. Session hijacking occurs when an attacker hijacks a user’s login and authentication credentials. And from the victim’s point of view, it often results in unpredictability or crashes of the targeted application.
When spoofing occurs, attackers use stolen or counterfeit tokens to initiate a new session that appears to be set by the original user.
Session Hijacking Techniques
To hijack a user’s session, an attacker can use several techniques, depending on the attacker’s position. Examples of session hijack attacks include:
Cross-site scripting session hijacking (XSS):
- When an attacker exploits vulnerabilities within a server or application, he injects Java scripts into a user’s web page, causing the browser to run arbitrary code.
- Moreover, injected scripts will be able to access your session key if the server does not set HTTP. Only in session cookies, thus, giving attackers the information required for session hijacking.
Session Side Jacking:
- An attacker can intercept the session cookies of a user after he or she authenticates them by using packet sniffing. By using SSL/TLS only for its login pages, the website takes the easy route and the attacker can steal the session key and impersonate the user to operate the web application.
- Generally, this happens with an unsecured WiFi Hotspot, as the attacker can access the network, monitor the traffic, and then set up their access points to conduct the attack.
Session Fixing:
- Using a session key, attackers gain access to the server by spoofing the user’s credentials.
- Due to stateless protocols, there is a threat of session hijacking. It is these limitations that make the protocols vulnerable to attacks.
- An SSL connection uses Secure Sockets Layers, which protect any personal information required to pass between the two systems. Thus, it reduces the risk of criminals reading and modifying the messages sent over the internet.
- Transport Layer Security (TLS) is simply an updated, more secure version of SSL.
Learn more about Cyber Security in this Cyber Security course in Bangalore to get ahead in your career!
How can an Attacker take Advantage of a Successful Session Hijack?
After the attacker has gained access, they can perform any actions authorized by the original user while the session is active. If the targeted application involves financial theft, the attacker may demand ransom to release data from the encrypted form, steal the users’ sensitive personal information from company systems, or steal money directly from their bank account.
In large organizations, cookies may be used to identify authenticated users within Single Sign-on (SSO) Systems. An attacker who successfully hijacks a session can gain access to various web applications, from financial databases and customer records to line-of-business applications containing valuable intellectual property.
When you log in using your Facebook account, or Google account, there are more safeguards in place, meaning that hijacking a session cookie won’t be enough to hijack your session.
Session Hijacking Example
Sessions are attacks that exploit data leaks in TLS request compression ratios. The attackers could then use the login cookies to hijack the user’s session. An organization known as CRIME used session hijackers to breach an organization’s website in September 2012.
After hijacking the website’s session by decrypting HTTPS cookies and logging in as users with brute force, CRIME was able to siphon off an enormous amount of data.
Job interviews coming up? Read our blog about Cyber Security Interview Questions and win your job interview!
Why is Encryption Important?
An organization can implement certain encryptions to prevent the hijacking of a user’s session. Your consumers’ sessions are protected by these encryptions, which take the form of certificates.
How to Prevent Session Hijacking?
A session hijacking threat is present because of limitations in the stateless HTTP protocol. It is possible to circumvent these restrictions by using session cookies, which allow web applications to identify individual computers and store their sessions, such as your shopping history on an online store.
There is no single method of protection that is guaranteed to block session hijacking, as it exploits fundamental mechanisms used by virtually all web applications. While following some simple online safety rules can help reduce risk, there is no guarantee that all the browsers will protect you from session hijacking.
Developers and administrators can minimize the risk of attackers obtaining valid session tokens by hardening multiple aspects of communication and session management:
- Secure all sessions using HTTPS to ensure SSL and TLS encryption. Even if they are monitoring the victim traffic, this will prevent attackers from intercepting plaintext session IDs. To encrypt all communications, use HSTS (HTTP Strict Transport Security).
- Using the Set-Cookie HTTP header, set the HttpOnly attribute to prevent client-side scripts from accessing cookies. As a result, XSS attacks and other threats involving JavaScript in the browser cannot occur. Aside from specifying Secure and SameSite, you can also increase security by specifying these directives.
- Session ID generation and management mechanisms in web frameworks are highly secure and well-tested. You need not develop a session management system from scratch.
- After initial authentication, re-generate the session key. After authentication, the session key changes immediately, nullifying session fixation attacks. The session ID becomes useless before it can be used – no matter how the attacker obtains it.
- The session key should not be the only method of proving the identity of the user. You must check more than just the IP address of the user. You need to examine the application’s usage patterns too.
- Using this approach can have the disadvantage of false alarms causing problems for legitimate users. An additional safety measure is to set a timeout after the user has been inactive for a set amount of time to close the session.
Tools to Reduce the Risk of Session Hijacking Attack
To prevent hijacking, you should strengthen the mechanisms employed by web applications. Communicating and managing sessions is one of the session hijacking countermeasures. The following are a few tools to reduce the risk of session hijacking:
- Burp Suite – This tool is widely used as an application security checker to conduct penetration testing on web applications. Burp is used to assess the security of web applications and to conduct on-the-spot testing.
- Ettercap – Ettercap is a network security tool that guards local area networks against malicious network attacks. It is used for analyzing computer network protocols and conducting security audits. It is available for Linux, Mac OS X, BSD, Solaris, and Microsoft Windows.
- OWASP ZAP – The OWASP Zed Attack Proxy (ZAP) is a free, open-source security tool actively maintained by volunteers around the world. During the development and testing of your web applications, it can help you automatically identify security vulnerabilities.
- BetterCAP – BetterCAP is a powerful, flexible, and portable tool developed to perform a variety of different MITM attacks against a network, manipulate HTTP, HTTPS, and TCP traffic in real-time, sniff credentials, and much more.
- WebSploit Framework – This open-source framework is used to test web applications and networks. This program uses Python modules to conduct many types of actions, including directory scanning, man-in-the-middle attacks, and wireless attacks.
- Cookie Cadger – Cookie Cadger is designed to help detect information leakage from applications that use insecure HTTP GET request methods. Cookies Cadger runs on Mac and Windows, and Java 7 must be installed. It is necessary to install “tshark” – part of the Wireshark suite, to use Cookie Cadger.
Conclusion
Session hijacking is a real threat to users, and they are always at risk of being compromised. An administrator of a website can mitigate these risks by implementing security protocols in several ways. Generally, these types of security protocols do not restrict the use of deep encryption within web applications but instead close out all points of entry for attacks on the user session.
It is of paramount importance for organizations to make their websites secure as the amount of data online and the number of web users continually increase. Global privacy regulations could lead to heavy fines if data privacy violations aren’t adhered to.
Feel free to ask your questions in our Cyber Security Community.
The post What is Session Hijacking? appeared first on Intellipaat Blog.
Blog: Intellipaat - Blog
Leave a Comment
You must be logged in to post a comment.








