What is Secret Key Cryptography?
What is Cryptography?
The process of concealing or coding information so that only the intended recipient can read it is known as cryptography. Cryptography has been used to encode messages for thousands of years and is still used in bank cards, computer passwords, and e-commerce.
Before jumping right away into the secrecy of Secret Key Cryptography, let’s have a look at the topics that are to be covered.
Points at a Glance:
- What is “Secret Key Cryptography”?
- Secret Key Cryptography Examples
- Uses: Secret Key Cryptography
- What is the difference between public-key and private-key cryptography?
Want to learn Cyber Security from Scratch, then do watch:
What is “Secret Key Cryptography”?
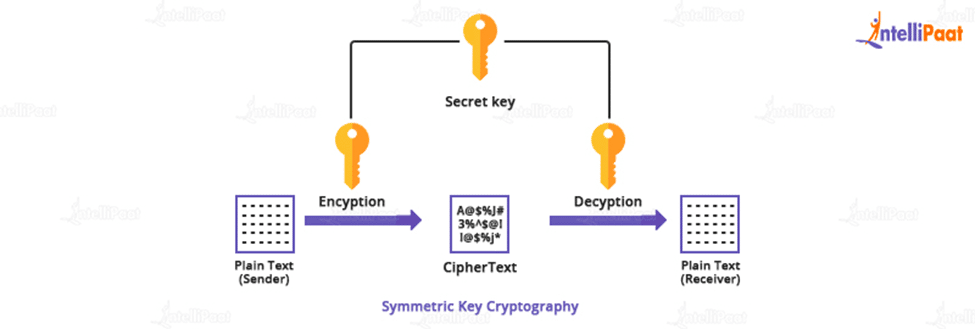
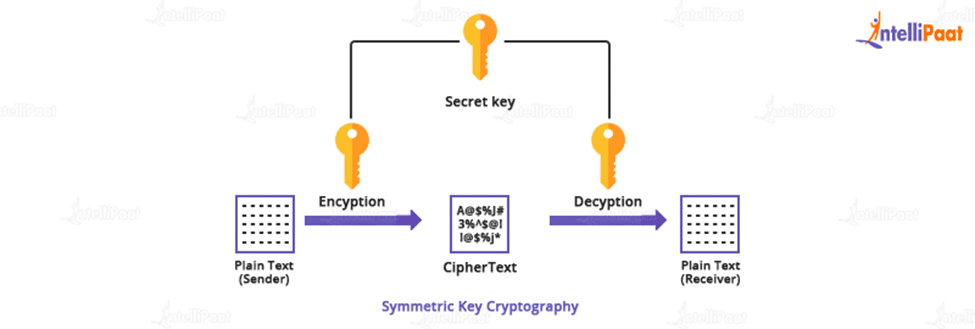
- Secret key cryptography uses a series of bits known as the secret key to encrypt the plaintext message. A secret key is also known as a symmetric key because it frequently uses the same key to decipher the corresponding ciphertext message and retrieve the initial plain text.
- The secret key is also an input for the encryption algorithm in cryptography because it is the first intelligible message or data fed into the algorithm as input. The main is an algorithm value that has nothing to do with the plaintext. Depending on the key, the algorithm produces a different result. The algorithm employs the key to exact substitution and transformation.
- Two different keys can produce two different ciphertexts for the same letter. The ciphertext is currently a nearly random stream of data. A decryption algorithm is a reverse-run encryption algorithm. Using the ciphertext and the secret key, it generates the original plain text.
- It goes without saying that in this type of cryptography, both the sender and the receiver must be aware of the key that serves as the password. Of course, the most difficult aspect of this method is the main distribution.
Do you want to learn about cyber security? What could be better than getting an overview with just a click? Check out our Cyber Security Tutorial!
Secret Key Cryptography Examples
- A simple method for encrypting messages is to replace each letter in the message with one from a different letter of the alphabet. The key is the number of locations. For example, in the encrypted message “Uijt jt bo fybnqmf,” the message “This is an example” can be encrypted using the key “1 position.” Taking a letter one position higher in the alphabet would result in the original message being repeated.
- This device is not particularly stable. There are only twenty-six possible keys. Eve should only try each key to see which one produces a readable message. Furthermore, it is well understood that certain letters appear more frequently in communications than others.
- For example, the letter “e” is the most commonly used letter in the English language. Eve can simply count the number of times the letter “e” appears in the encrypted message and replace it with it using this reality. And she knows how many times she has to rotate to get from “e” to the encrypted version of “e,” so she knows the secret automatically.
If you want to pursue a career in cyber security, Cyber Security Course is a great place to start.
Uses: Secret Key Cryptography
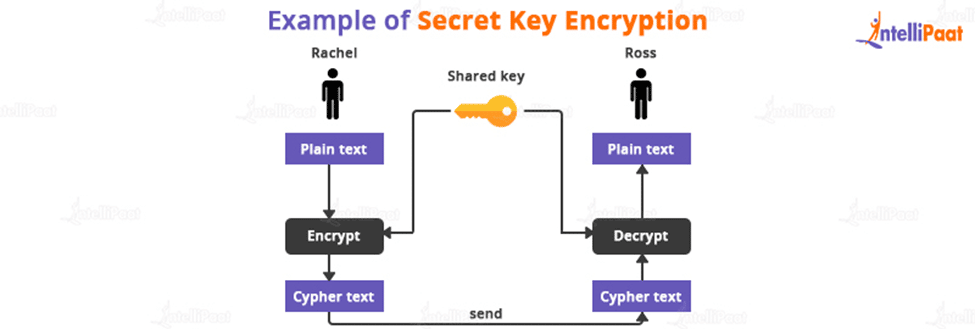
- When using secret key encryption, both Rachel and Ross communicators use the same key to encrypt and decode texts. Rachel and Ross must both have the key and agree on the cryptographic protocol to be used for encryption and decryption before any encrypted data can be sent across the network.
- The logistical challenge of getting the key from one party to the other without giving the attacker access is one of the major issues with secret key cryptography. If Rachel and Ross use secret-key cryptography to protect their data and Charlie has access to their key, Charlie will comprehend any secret messages intercepted by Rachel and Ross.
- Charlie can not only decrypt Rachel and Ross’s messages, but he can also impersonate Rachel and send encrypted data to Ross. Ross won’t notice that the letter was written by Charlie rather than Rachel.
- Once the issue of secret key dissemination is resolved, secret key cryptography could be a powerful method. Algorithms are extremely secure and can easily encrypt data. A secret key is used to encrypt the majority of confidential data transmitted during an SSL session.
- Secret key cryptography is also known as symmetric cryptography because the same key is used to encrypt and decrypt data. Well-known hidden key
cryptographic algorithms include Data Encryption Standard (DES), triple-strong DES (3DES), Rivest Cipher 2 (RC2), and Rivest Cipher 4. (RC4).
Top 50 Cyber Security Interview Questions is designed for people who are preparing for interviews!
What is the difference between public-key and secret key cryptography?
| Parameters | Public Key Cryptography | Secret Key Cryptography |
| Algorithm | The public key is used to encrypt data, and the private key is used and shared to decrypt data. | A Secret Key is used to encrypt and decrypt the data, and the data is shared between the receiver and sender of encrypted data. |
| Effectiveness | Performance has decreased. | The performance of the mechanism has improved. |
| Secret | The use of the public key is completely free. | The secret is known to both the sender and the receiver. |
| Form | The public key mechanism is referred to as asymmetric because its two keys are used for different purposes. | Because it uses a single key between two parties, the secret key mechanism is known as symmetric. |
| Access | The public key is available to everyone. | Two people share the secret key. |
Career Transition
Conclusion
A predefined cryptographic key or pair of keys is used in both secret-key and public-key cryptography. A key is a collection of bits that is used by a cryptographic algorithm or algorithms to encrypt and decrypt data. A cryptographic key is analogous to a lock key in that only the correct key will open the lock.
Don’t be afraid to ask your questions in our Cyber Security Community.
Our team will assist you in resolving them. Until then, keep learning!
The post What is Secret Key Cryptography? appeared first on Intellipaat Blog.
Blog: Intellipaat - Blog
Leave a Comment
You must be logged in to post a comment.