What is Reconnaissance in Cyber Security?
Let us get through the contents of this comprehensive blog:
- What is Reconnaissance?
- Types of Reconnaissance
- 7 Fundamentals of Reconnaissance
- How to Prevent a Reconnaissance Attack
- Usage in Penetration Testing
- Conclusion
What is Reconnaissance?
Ethical hacking begins with gathering information and becoming familiar with the target system. Reconnaissance refers to a set of processes and techniques, such as footprinting and scanning and enumeration, that are used to gather and covertly discover as much information as possible about a target system.
Reconnaissance is an essential step in locating and stealing confidential information. In a proper recon, attackers would have access to detailed information. In this way, reconnaissance, in information security, is used for penetration testing.
To gain information without actively engaging with the network, an attacker uses recon to interact with the network’s open ports, running services, etc. The information it provides can help gain access to networks beyond the internet. In short, recon is a treasure trove of valuable information that is susceptible to attacks.
Unexpectedly, it is unknown how long a recon can take to get into networks; it may take weeks or months. Moreover, a recon may not access any information system but still result in data breach, collecting all sensitive data at once, exploiting networks.
An ethical hacker takes the following seven steps during reconnaissance to gather as much information about a target system as possible:
- Collecting initial information
- Determining the network’s range
- Identifying active machines
- Discovering available access points and ports
- Identifying the operating system by its fingerprint
- Locating services on ports
- Creating a network map
In order to gain information about a network, an attacker will use the following steps:
- File permissions
- Running network services
- OS platform
- Trust relationships
- User account information
Train under experts by enrolling in the Ethical Hacking course offered by Intellipaat.
Types of Reconnaissance
There are two main types of reconnaissance, active reconnaissance and passive reconnaissance. Let us understand the difference between active reconnaissance and passive reconnaissance.
Active Reconnaissance
Cybercriminals, who use active reconnaissance, try to obtain information about computer systems using tools such as automated scanning and manual testing, ping, and netcat. Since active reconnaissance creates more noise within the system and has a higher chance of detection, it is generally faster and more accurate.
Port Scanning
Port scanning is an example of active reconnaissance. Port scanning is the process of scanning computer ports to identify open ports to a computer since the entire information is going in and out through these ports.
Using port scanning, attackers determine what services are visible and where an attack can be conducted. As part of port scanning, data is retrieved from opened ports and analyzed.
Tools and Techniques Used
Here are a few examples of active reconnaissance tools.
Nmap
The most well-known tool for active network reconnaissance is probably Nmap. Using Nmap, we can find out information about a system and its programs. It is accomplished by using a series of different scan types that take advantage of the details of how a system or service works. An attacker can learn a great deal about a network by scanning a system or range of IP addresses under a target’s control.
Metasploit
Metasploit is designed primarily as an exploitation toolkit. Several modules in it contain multiple prepackaged exploits for various vulnerabilities. Metasploit provides a window into a wide range of vulnerable machines, even for novice hackers.
Although Metasploit is designed as an exploit toolkit, it can also be used for reconnaissance. Using the auto pawn feature in Metasploit allows a hacker to use any means necessary to attempt to exploit a target. A hacker can use Metasploit for more subtle reconnaissance with more targeted analysis.
Register for Intellipaat’s Cyber Security course online and learn concepts related to reconnaissance.
Passive Reconnaissance
In passive reconnaissance, methods such as Wireshark and Shodan are used to gather information without interacting directly with systems, while OS fingerprinting is used to harvest information.
By employing passive reconnaissance, we can gather data without interacting with the framework or application we are trying to comprehend. Data is collected through web searches and free reports. The framework is unlikely to know the IP address when we use passive reconnaissance.
We can also conduct passive recon without directly interacting with the target. By doing so, no request is sent to the target and, therefore, they have no idea that information is being gathered about them. In most cases, passive information gathering utilizes public resources that hold information on the target.
Open-source intelligence (OSINT) involves gathering information from public resources. Among the things that can be gathered using OSINT are IP addresses, domain names, email addresses, names, host names, DNS records, and even what software is running on a website and its associated CVEs.
Tools and Techniques Used
Here are a few recon tools that are for passive attacks.
Wireshark
Wireshark is best known for its network traffic analysis capabilities, but it is invaluable for passive network reconnaissance. A hacker who gains access to a company’s Wi-Fi network or otherwise eavesdrops on employee network traffic, can then analyze that traffic in Wireshark to gain valuable insights about that network.
Shodan
Shodan is an internet-connected device search engine. With the Internet of things growing, increasingly insecure devices are being connected to the internet.
Shodan allows hackers to find devices within the IP address range of a company. Identifying one or more vulnerable IoT devices on a network may give a hacker a good starting point for a future attack since many IoT devices are vulnerable by default.
To get to know more about Ethical Hacking tools and software, take a look at our blog.
OS Fingerprinting
OS fingerprinting determines what operating system is run by a remote computer. Most exploitable vulnerabilities are operating system-specific, so OS fingerprinting is primarily used for cyber reconnaissance.
Another way by which reconnaissance can be performed is by using search engines.
When it comes to passive reconnaissance tools, search engines are on top of the list. Many remarkable pursuits can be accomplished with Google and other search engines. Programmers and attackers may use search engines to perform Google hacking. Innovative hacking strategies coupled with fundamental investigation techniques can cause great damage.
Career Transition
Nessus
Nessus is a software program that scans for vulnerabilities in companies. Specifically, it is intended to identify weak applications running in a network and provide some insights into possible exploitable weaknesses. Even though Nessus is a paid scanner, the data it offers is extensive, making it an advantageous venture for hackers.
OpenVAS
As a result of the commercialization of Nessus, OpenVAS was created to scan for vulnerabilities. OpenVAS was made out of the last open-source form of Nessus’s weakness scanner, which became closed-source, to continue giving a free alternative. Thus, OpenVAS provides a similar functionality as Nessus. However, OpenVAS might fall short on a few features that have been added since Nessus was released.
Getting ready for an ethical hacking interview? Visit our blog to learn how to prepare for Ethical Hacking interviews!
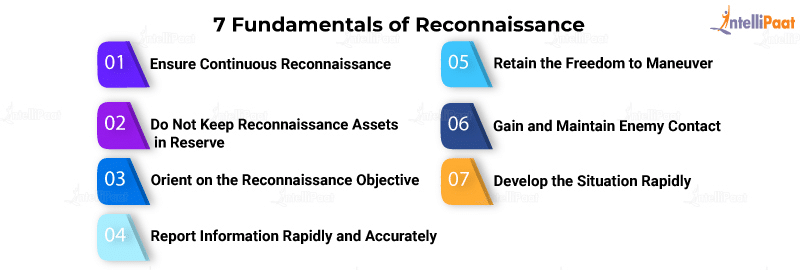
7 Fundamentals of Reconnaissance
Reconnaissance operations are characterized by the following seven fundamentals:
- Maintain a continuous reconnaissance system
- Do not reserve reconnaissance assets
- Orient yourself toward the reconnaissance objective
- Provide accurate and timely information
- Make sure to have room to maneuver
- Contact and maintain enemy forces
- Develop the situation quickly
Visit our tutorial on Cyber Security to learn more about this domain!
How to Prevent a Reconnaissance Attack
Penetration testing can be used by companies to discover what their network would reveal in the event of a reconnaissance attack. Companies can deploy passive scanning tools, which scan large networks and find out which hosts are online, and vulnerability scanners, which identify any and all vulnerabilities within a network.
Additionally, SIEM solutions can detect source IP addresses that are running passive scanning tools in the network.
One of the best ways to secure a network perimeter is with a stateful firewall, the best prevention measures against any intrusion. Multiple connection attempts from the same source IP address should be logged by the firewall so that only necessary traffic is allowed.
Take a moment to watch this video to learn about cyberthreats.
Usage in Penetration Testing
Cyber reconnaissance is an integral part of penetration testing. It is this step that dictates what is going to be done in the subsequent steps of the test. As part of the reconnaissance, we can use passive information gathering techniques to gather information about a company, its employees, and the technology it uses.
Information can also be gathered by using active information gathering techniques about specific systems of the target, such as operating system, services run on the machine, and open ports. An effective penetration tester will utilize both types of information gathering to find the best method of breaching a company.
Conclusion
It is impossible to provide 100 percent security, but we can mitigate the impact by ensuring the maximum level of security possible so that recon is unable to learn information about the systems.
Hacking activities involve reconnaissance in a significant way. Programmers can determine potential attack vectors and pinpoint possible weaknesses by gathering any data about the target.
Feeling uncertain? Get in touch with our Cyber Security community right away!
The post What is Reconnaissance in Cyber Security? appeared first on Intellipaat Blog.
Blog: Intellipaat - Blog
Leave a Comment
You must be logged in to post a comment.













