What is Ransomware? A Complete Overview
Let us look at the topics addressed in this article:
- What is Ransomware?
- History of Ransomware Attacks
- How does Ransomware Attacks Work?
- Types of Ransomware Attacks
- Ransomware Examples
- Popular Ransomware Attacks
- Ransomware Removal Techniques
- Ransomware Protection Tips
- Conclusion
Before going any further, look at this video in which our cybersecurity specialists explain the various cyber threats.
What is Ransomware?
Ransomware is a type of malware. Ransomware means that the attacker may lock up your computer, usually via an infected mail link or a Trojan Horse assault, and demand payment in exchange for giving control of your system back to you.
Some of the variants of ransomware will make you think that something is wrong with your computer and make you pay for it.
One of the prevalent tactics is claiming that something has infected your computer in banner advertising. Often, you will at least have rudimentary system management, so the only real problem is that you have to manage these frequent pop-ups until you find a means to get rid of the malware.
A much more aggravating type of ransomware would completely lock your computer and prevent you from logging into your operating system unless you pay.
The worst type of ransomware is the one that not only locks your device but also encrypts your files and does not provide you with the keys to decrypt them unless you pay.
Another unsurprising issue with cybercriminals is that they are not very trustworthy, and many people have reported not receiving their files back even after paying the ransom.
The ransomware decrypt tool is a decryption key provided by the hacker after the payment of the ransom.
Have a look at our blog on Cyber Security tutorial to learn more about this hot domain!
History of Ransomware Attacks
Malware has been around since the dawn of the internet; in short, malware is software created for malicious purposes. Malware spreads to computers via spam emails, misleading links, fake software updates, and through exploiting vulnerabilities in the web browser and popular software.
About a decade ago, a new and particularly sinister type of malware called ransomware emerged. In 2005, Russian criminals created the first ransomware, detected as Trojan Crysis.
It was a rudimentary parasite that zipped and password-protected a user’s files, and the ransom note would be found on the user’s desktop.
In 2012, ransomware attacks spread across Europe and North America, masquerading as government enforcement warnings accusing victims of piracy and terrorism. The victims were then encouraged to pay a $200 fee or face criminal prosecution.
In 2013, ransomware creators were already extorting more than three million dollars from their victims each year.
Then CryptoLocker was introduced, and the stakes quickly doubled. CryptoLocker represents a new kind of malware that encrypts user photographs, papers, and other personal information using a secret key that is unique to each user. The decryption key is restored only after paying the ransom to the criminals.
On January 10, 2015, the FBI issued an official statement stating that ransomware attacks are on the rise, highlighting that a new ransomware strain, CryptoWall, is encrypting user data and demanding between $200 and $5,000 in Bitcoin to restore the data.
Have a look at Intellipaat’s Cyber Security courses and sign up today!
How does Ransomware Attacks Work?
Now that we know what a ransomware attack is. Let us dive further to know how ransomware attacks work. There are many vectors through which ransomware would get access to a computer. One of which is phishing:
- The attacker sends the victim an email that seems to be from a reputable website. If the user clicks on the mail, the program will get downloaded. Malware can perform a variety of functions once it gets access to the machine. The virus remains undetected for a specified amount of time while exploiting the system.
- The ransomware takes control of the computer. It uses asymmetric key cryptography. Both public and private key pairs are generated by the attacker. After a successful exploit, ransomware drops and executes a malicious binary on the infected system. This binary then searches and encrypts valuable files such as Microsoft Word documents, images, and databases.
The ransomware may also exploit the system and network vulnerabilities to spread to other systems and possibly across entire organizations.
- The attacker warns the victim that if the ransom is not paid, the data will be published publicly or permanently erased.
- If the user accepts the ransom and pays it, the attacker will supply the user with a decryption key, allowing the user to regain access to the system.
- Getting the decryption key from the hacker is not guaranteed. Victims have reported that they did not get access to the system or were not provided with the decryption key even after paying the ransom.
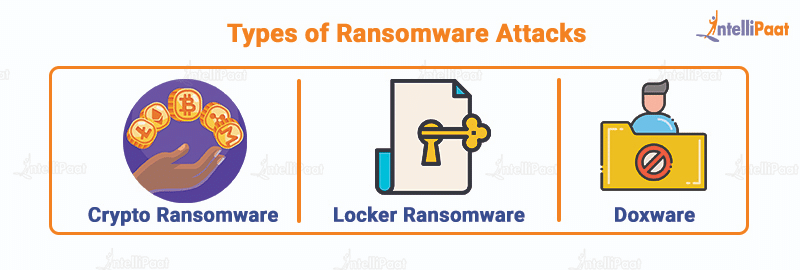
Types of Ransomware Attacks
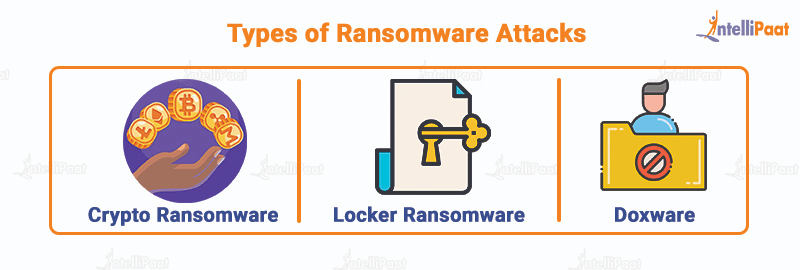
There are primarily three different types of ransomware that have held victims hostage and forced them to oblige to the ransom demands. The types of ransomware are listed below:
- Crypto ransomware: This type of ransomware encrypts files and documents on a computer so that the user cannot access them. The attacker demands the victim to pay the ransom to get the files back in their original form.
This ransomware is the form of malware that attacks a computer and restricts the user’s access to files stored on the computer by encrypting them.
For example, Locky, Wannacry, Bad Rabbit, Ryuk, SamSam, Petya, and TeslaCrypt
- Locker ransomware: Locker ransomware locks the victim out of their devices, preventing them from using the computer. It demands the victim to pay ransom to unlock the device, commonly known as screen-locker ransomware.
This type of ransomware locks the user or victim out of their device. The ransomware pops up the window with the demand for ransom to unlock the device.
For example, MrLocker, Metropolitan Police scam, and FBI MoneyPak scam
- Doxware: Doxware threatens to release sensitive information if the ransom is not paid. Dox means documents and doxing is the act of publishing someone’s personal information online. Doxing is the internet-based practice of researching and publicly broadcasting private, identifiable information about an individual or organization.
For example, the Dark Overlord and Leaker Loker
Preparing for an ethical hacking job interview? Have a look at our blog on ethical hacking interview questions and start preparing!
Ransomware Examples
Here are some ransomware examples listed:
- Locky: Locky is a kind of ransomware attack. A gang of hackers published Locky in 2016. Locky, which can encrypt over 160 file types, spreads by fooling users into installing it via phishing emails with malicious attachments. This technique of transmission is known as phishing and it is a type of social engineering.
- Bad Rabbit: The Bad Rabbit ransomware assault spreads using a technique known as drive-by downloads. Insecure websites are chosen and utilized to launch an assault. In a drive-by ransomware attack, a person accesses a genuine website unaware that it has been hijacked by a hacker. When a person installs malware from a website, they get infected. Bad Rabbit is also termed a malware dropper.
- Ryuk: Ryuk ransomware first appeared in August 2018; it blocked Windows System Restore, making it critical to restore encrypted information without a backup. Many of the organizations targeted in the United States paid the requested ransoms. According to sources, the attack raised more than $640,000.
- LockerGoga: LockerGoga is the newest, targeted, and most destructive type of ransomware. It appears to have both ransomware and wiper capabilities. Later versions of this type of ransomware virus forcibly logged victims off the infected device. That is a very different approach from typical ransomware. Only a handful of anti-malware products were able to detect and neutralize LockerGoga.
Popular Ransomware Attacks
Let us talk about the ransomware virus attack that caused data breach on a large scale.
- WannaCry ransomware: WannaCry, an enormous hacking attack that triggered widespread computer devastation, attacked computers all over the world. On May 14, 2017, over 200,000 machines in over 150 countries were compromised. The attack did not appear to create significant long-term damage, and the hackers only made around $100,000 in total. The world witnessed one of the most massive and bizarre computer attacks in history.
WannaCry ransomware is an example of a ransomware assault in which data is infected. There are many other types of ransomware, but WannaCry ransomware spread swiftly by exploiting a tool that security experts suspect was built by the NSA. To be clear, the NSA was not interested in ransom, just in snooping!; but it created a tool that took advantage of a security weakness in Microsoft software. The hackers set up their ransom payment system in a way that did not keep track of who paid the ransom, and it was set up so they would have to decrypt each victim’s files manually.
Career Transition
- Petya: Petya and NotPetya are two malware strains that infected thousands of computers throughout the world in 2016 and 2017. Both Petya and NotPetya seek to encrypt the hard drives of the infected machines. The two malware have enough similarities that NotPetya was first dismissed as a variation on a theme.
NotPetya, on the other hand, has many more potential tools to help it spread and infect computers, and unlike Petya, which is a standard piece of ransomware designed to extract a few quick Bitcoins from victims, NotPetya is widely regarded as a state-sponsored Russian cyberattack disguised as ransomware.
Enroll in the Ethical Hacking course offered by Intellipaat and train under experts.
Ransomware Removal Techniques
If you believe you have been the victim of a ransomware assault, you must act fast. Nevertheless, there are many actions you can take to offer yourself the best chance of reducing harm and swiftly resuming normal operations.
- Detach the infected device: Malware that impacts only one device is a minor annoyance. Allowing ransomware to infect all your devices is a big disaster that may take you out of the company forever. The distinction is frequently determined by the response speed.
- Examine the damage: To identify which machines have been compromised, search for newly encrypted data with unusual executable file names as well as reports of unusual file names or people having difficulty accessing files. If you find any equipment that is not properly encrypted, isolate and switch them off to help contain the assault and avoid additional harm and data loss.
Your aim is to compile a complete inventory of all impacted systems—data storage, cloud services, portable hard disk drive processing, particularly USB memory sticks, workstations, cellphones, and just about any other potential vectors.
- Diagnose the ransomware: Before proceeding, it is critical to determine the version of ransomware that you are dealing with.
- Notify the ransomware to the police: For numerous reasons, you should inform the police as soon as the malware has been controlled. First and foremost, ransomware is illegal and, as with any similar offense, should be brought to the notice of the authorities.
Secondly, as per the FBI, law enforcement may be able to employ legal authority and capabilities that most organizations do not have. Partnerships with foreign law enforcement can be used to assist in the recovery of stolen or encrypted data and the prosecution of offenders.
- Examine your backups: It is time to start the response procedure. The most straightforward method is to restore your systems from a backup so that you have undamaged and useful data to restore for later use.[3] [4] If this is the case, the next step is to use a virus protection solution to guarantee that all affected systems and devices are clean of ransomware; otherwise, it will continue to lock your computer and data, potentially ruining your backup.
- Investigate your decryption options: If you do not have a backup, there is still a chance that you can recover your data, if a decryption key for the type of ransomware you are dealing with is available.
Enroll in our Cyber Security course and get certified from experts.
Ransomware Protection Tips
Ransomware protection is the first step to defend an attack. There are actions that you can take to help safeguard your computer and devices from ransomware infiltration. Here is a list of things to keep in mind:
- Always have a backup of your data. If you have an additional backup of personal information, then you should be able to view it even if an attempt has been made to lock it.
- Set up a dependable ransomware defense software.
- Maintain the most recent versions of your operating system, apps, and security software. This aids to safeguard you against the most recent malware by utilizing the most recent security patches.
- Never open email attachments or click on links from unknown sources as they could be infected with malware.
- Be cautious when using the internet; malicious websites and pop-up advertising are eagerly awaiting your click.
- Surf the internet on unsecured Wi-Fi networks at your own risk.
- Using a virtual private network (VPN) may allow you to keep your information secret.
- Never utilize USB sticks from untrustworthy sources. You should not provide attackers an easy path.
Conclusion
Ransomware, in all of its forms and permutations, is a huge danger to both ordinary users and businesses. This emphasizes the importance of keeping an eye on the threat and being prepared for any eventuality. As a result, it is critical to educate yourself about ransomware, be mindful of how you use gadgets, and install the finest protection software.
Having doubts? Shoot them right away to our Cyber Security community!
The post What is Ransomware? A Complete Overview appeared first on Intellipaat Blog.
Blog: Intellipaat - Blog
Leave a Comment
You must be logged in to post a comment.