What is Multi-Factor Authentication?
In this blog, we will delve into the world of MFA, exploring its definition, mechanisms, and advantages in combating the ever-evolving challenges of the digital age. So, let’s embark on this journey together and unlock the layers of multi-factor authentication.
Table of Contents:
- What is Multi-Factor Authentication (MFA)?
- How Does Multi-Factor Authentication Work?
- Types of Multi-Factor Authentication
- Top MFA Tools
- Advantages of Multi-Factor Authentication
- Examples of Multi-Factor Authentication
- Challenges of Multi-Factor Authentication
- Conclusion
Learn the Ethical Hacking course in-depth by watching the video below
{
“@context”: “https://schema.org”,
“@type”: “VideoObject”,
“name”: “Ethical Hacking Course | Ethical Hacking Tutorial Online | Learn Ethical Hacking | Intellipaat”,
“description”: “What is Multi-Factor Authentication?”,
“thumbnailUrl”: “https://img.youtube.com/vi/CyRj4yGiL9A/hqdefault.jpg”,
“uploadDate”: “2023-07-18T08:00:00+08:00”,
“publisher”: {
“@type”: “Organization”,
“name”: “Intellipaat Software Solutions Pvt Ltd”,
“logo”: {
“@type”: “ImageObject”,
“url”: “https://intellipaat.com/blog/wp-content/themes/intellipaat-blog-new/images/logo.png”,
“width”: 124,
“height”: 43
}
},
“embedUrl”: “https://www.youtube.com/embed/CyRj4yGiL9A”
}
What is Multi-Factor Authentication (MFA)?
Multi-factor authentication (MFA) is a security feature that requires users to submit several forms of authentication to access a system or application. This protocol is intended to supplement traditional username- and password-based authentication. MFA makes it more difficult for unauthorized users to access a system by demanding several forms of authentication.
MFA is intended to provide a more secure type of authentication by requiring several kinds of proof that the user is who they claim to be. It contributes to preventing unauthorized access to systems and applications by adding additional levels of security. MFA is a critical security measure that can be used to protect sensitive data such as financial records, medical records, and personal information.
How Does Multi-Factor Authentication Work?
Multi-factor authentication operates on the principle of requiring the user to provide multiple forms of authentication prior to being granted access to a system or application. The authentication process typically consists of three factors: something the user knows, something the user has, and something the user is. Each factor represents a different form of authentication and provides an extra layer of security.
- The first factor is something the user knows, such as a password, PIN (personal identification number), or response to a security question. This factor should be known only by the user and is usually used as the primary form of authentication.
- The second factor is something the user has, such as a mobile device, smart card, or security token. This factor provides an additional layer of protection by requiring the user to have access to a physical device in addition to a password or PIN.
- The third factor is something the user is, such as biometric data like fingerprints, facial recognition, or voice recognition. This factor is becoming increasingly popular due to the rise of smartphones with biometric sensors. Due to its uniqueness and the difficulty of replication, biometric authentication offers a high level of security.
The user must provide two or more means of authentication that are compliant with the requirements in order to access an MFA-enabled system or application. The user may need to provide a fingerprint scan and a password to access a system.
Interested to learn about Ethical Hacking? Enroll now in Ethical Hacking Training!
Types of Multi-Factor Authentication
Multi-factor authentication can be broken down into different types, depending on the number of factors required for authentication. The most common types of MFA include two-factor authentication (2FA), three-factor authentication (3FA), and four-factor authentication (4FA).
Two-Factor Authentication (2FA)
The most widely utilized form of MFA is two-factor authentication (2FA). It requires the user to provide two forms of authentication, typically a password and a second form of authentication, such as a fingerprint scan or a security token. 2FA provides an additional safeguard against unauthorized access to a system or application.
Example: Duo Security
Three-Factor Authentication (3FA)
The user must submit three different pieces of identification when using three-factor authentication (3FA). A password, a physical object, such as a security token, and a biometric component, like a fingerprint scan, are the common components. Three-factor authentication offers a greater level of security than two-factor authentication since it makes it more difficult for unauthorized users to access a system.
Example: Google Authenticator
Four-Factor Authentication (4FA)
Four-factor authentication (4FA) is the most secure form of MFA available. It requires the user to provide four forms of authentication, typically a password, a physical device, a biometric factor, and a location-based factor. The location-based factor requires the user to be in a specific location before gaining access to a system or application. Using four different forms of authentication (4FA) offers the maximum level of security. It makes it nearly impossible for unauthorized people to get access.
Example: Microsoft Azure Multi-Factor Authentication (MFA)
Read Ethical Hacking Interview Questions to crack your ethical hacking job interview.
Top MFA Tools
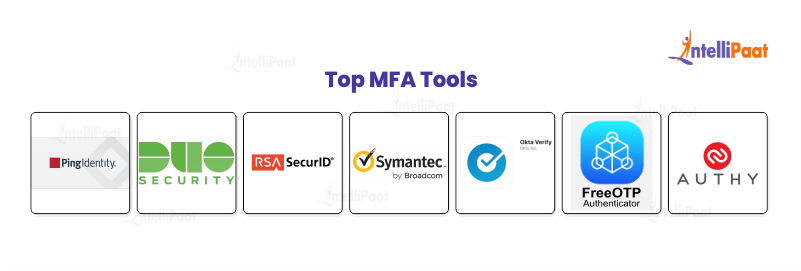
There are various Multi-Factor Authentication tools available, the most popular of which are:
PingIdentity
PingIdentity is a prominent industry provider specializing in robust identity and access management (IAM) solutions. Its platform empowers organizations to effectively oversee user identities, regulate access to diverse systems and applications, and fortify digital interactions across a multitude of environments, including cloud, on-premises, and hybrid setups.
Integration:
- Seamless integration with various applications and systems.
- Supports protocols such as SAML, OAuth, OpenID Connect, LDAP, RADIUS, and more.
- Provides APIs and SDKs for developers to integrate MFA capabilities into their applications.
Features:
- Multiple authentication factors (knowledge, possession, biometrics).
- Adaptive authentication based on risk factors.
- Self-service capabilities for users to manage MFA settings.
- Integration with single sign-on (SSO) solutions.
- Mobile push notifications for authentication requests.
- Offline authentication with one-time passcodes (OTP).
- Risk-based authentication for dynamic security levels.
- Reporting and analytics for monitoring and threat identification.
Compliance:
FIDO2, NIST 800-63-3, PCI DSS, GDPR, HIPAA, ISOC 2, and FedRAMP.
Duo Security
Duo Security provides multi-factor authentication (MFA) solutions for both personal and commercial use. Push notifications, SMS, phone calls, and hardware tokens are among the authentication methods supported.
Integrations: Duo Security seamlessly integrates with an extensive array of applications, platforms, VPN solutions, and remote access tools, ensuring comprehensive compatibility across various digital environments.
Features:
- Duo Security excels in providing diverse authentication methods, including push notifications, SMS, phone calls, and hardware tokens.
- The broad range of options allows users to choose the most convenient and secure authentication mechanism for their needs.
- Additionally, Duo Security offers granular policy controls, empowering organizations to customize and enforce specific security policies based on their unique requirements.
- With its versatility, Duo Security caters to both personal and enterprise users, addressing the security needs of individuals and organizations alike.
Compliance:
FIDO2, HIPAA, SOC 2, PCI DSS, GDPR, FedRAMP, and CJIS.
Career Transition
RSA SecurID
RSA SecurID is a widely adopted MFA system that combines the utilization of hardware and software tokens. Renowned for its effectiveness, it offers formidable authentication measures to safeguard sensitive information.
Integrations: Widely integrated with enterprise-level applications, VPNs, identity management solutions, and remote access tools.
Features:
- Utilizes a combination of hardware and software tokens to provide secure authentication.
- It generates time-based codes and offers advanced security features suitable for enterprise environments.
Compliance:
FIPS 140-2, PCI DSS, HIPAA, GDPR, NIST 800-53, SOC 2, and FedRAMP.
Symantec VIP
Symantec VIP is a cloud-based MFA service renowned for its versatility in authentication methods. It provides options such as mobile push notifications, SMS, voice calls, and biometrics to cater to different user preferences and security requirements.
Integrations: Symantec VIP offers extensive integration capabilities, encompassing a wide range of services and platforms, including cloud applications and VPNs. This enables users to employ Symantec VIP’s MFA functionality across various digital environments, ensuring comprehensive protection.
Features:
- Symantec VIP stands out by providing flexible authentication options tailored to individual preferences.
- These options include conventional methods such as mobile push notifications, SMS, voice calls, and biometrics.
- It empowers users to choose the most suitable authentication method for their needs.
- By offering a seamless and secure login experience, Symantec VIP enhances user convenience without compromising on security.
Compliance:
SEC, SOX, PCI DSS, GDPR, HIPAA
Okta Verify
Okta Verify is an MFA application specifically designed for integration with the Okta identity management platform. It offers a range of authentication factors, including push notifications, SMS, voice calls, and biometrics, ensuring a robust and customizable authentication experience.
Integrations: Okta Verify is purposefully designed to seamlessly integrate with the Okta identity management platform, ensuring a cohesive user experience within the Okta ecosystem. It harmoniously integrates with Okta-supported applications, enabling a streamlined MFA process.
Features:
- Okta Verify excels in providing a diverse range of authentication factors, including push notifications, SMS, voice calls, and biometrics.
- This versatility allows users to choose the most convenient and secure method for authenticating their identity.
- In addition to these authentication options, Okta Verify offers supplementary security features such as geolocation and device recognition.
Compliance:
PCI DSS, HIPAA, GDPR, SOX, and FIDO.
FreeOTP
FreeOTP is an open-source MFA application developed by Red Hat. Its notable features include TOTP generation and the ability to handle multiple accounts, making it a reliable and cost-effective choice for users seeking a secure MFA solution.
Integrations: FreeOTP is compatible with any service or platform that supports Time-Based One-Time Password (TOTP) authentication, ensuring its versatility and compatibility across various online services.
Features:
- FreeOTP distinguishes itself as an open-source application designed to generate TOTPs, enabling users to securely manage multiple accounts.
- By providing TOTPs, FreeOTP adds an additional layer of security to online accounts, effectively mitigating the risk of unauthorized access.
- This app enhances the overall security posture and reinforces the protection of sensitive information associated with the user’s online presence.
Compliance:
GDPR, PCI DSS, HIPAA, NIST, FIPS.
Authy
Authy is a popular MFA app that offers a user-friendly interface and supports multiple devices. It provides backup and sync functionality, making it easier to manage your MFA codes across different devices.
Integrations: Authy offers seamless integration with highly recognized services, including Dropbox, Amazon, Evernote, and other widely-used platforms, ensuring comprehensive coverage of popular online services.
Features:
- Authy distinguishes itself by providing robust multi-device support.
- Enable users to synchronize their MFA codes across multiple devices for enhanced convenience and accessibility.
- It offers an added layer of security through encrypted backup and recovery options.
- It safeguards MFA codes in case of device loss or failure.
- It ensures the continuity of secure access to accounts.
Compliance:
SOC 2, GDPR, HIPAA, ISO 27001, PSD2, and FFIEC.
Advantages of Multi-Factor Authentication
The benefits of using MFA include increased security, reduced risk of data breaches, and compliance with industry regulations. Now, let’s delve into each of them extensively:
- Enhanced Security
Multi-factor authentication provides an additional layer of security to protect against unauthorized access. By requiring users to provide more than one authentication factor, MFA ensures that only authorized personnel gain access to sensitive information. This security precaution makes it harder for cyber attackers to get access to a system, even if they have the login credentials of a user.
- Reduced Risk of Data Breaches
Data breaches can be devastating for businesses, resulting in loss of revenue, reputational damage, and legal repercussions. Multi-factor authentication can reduce the risk of data breaches by making it difficult for attackers to obtain sensitive information.
Read On: Ethical Hacking Tutorial to enhance your knowledge!
- Compliance with Regulations
Numerous sectors, including healthcare and finance, are bound by stringent regulations regarding data protection. Multi-factor authentication can help organizations meet compliance requirements by providing an extra layer of security to protect sensitive data. In some cases, MFA is required by law to ensure the protection of sensitive information.
- Improved User Experience
Multi-factor authentication can also improve the user experience by eliminating the need for complicated passwords. MFA allows users to access a system by combining authentication factors such as fingerprint scanning, facial recognition, or voice recognition. This can speed up and simplify the login process for users while still maintaining strong security.
Courses you may like
Examples of Multi-Factor Authentication
Here are the various examples of multi-factor authentication:
- Logging into Your Bank Account:
- Username and Password: This is the basic login method where you enter a username (unique identifier) and a password (something you know) to access your bank account.
- One-Time Password (OTP): In addition to the username and password, you receive a temporary code via SMS or email (something you have) that you need to enter as a second factor.
- Biometric Authentication: Along with the username and password, you use your fingerprint, face, or voice (something you are) to verify your identity.
- Hardware Token: In some cases, banks provide customers with physical tokens that generate unique codes (something you have) to be used as a second factor.
- Using an ATM:
- Bank card and PIN: When using an ATM, you insert your bank card (something you have) and enter a Personal Identification Number (PIN) (something you know) to authenticate the transaction.
- Using a Credit Card Online:
- Card details and CVV: When making an online purchase, you enter your credit card number (something you have), the expiration date, and the Card Verification Value (CVV) code (usually a three-digit number on the back of the card) (something you know) to authenticate the transaction.
- One-Time Password (OTP): Some credit card issuers provide an additional layer of security by sending an OTP to your registered mobile number or email address (something you have) that you need to enter during the online transaction.
- Work or Corporate Accounts:
- Username and Password: Employees log in to their work or corporate accounts using a username (something they know) and a password (something they know).
- Security Token or Smart Card: In some organizations, employees are provided with a physical security token or smart card (something they have) that generates a unique code or is used in conjunction with a card reader as a second factor of authentication.
Challenges of Multi-Factor Authentication
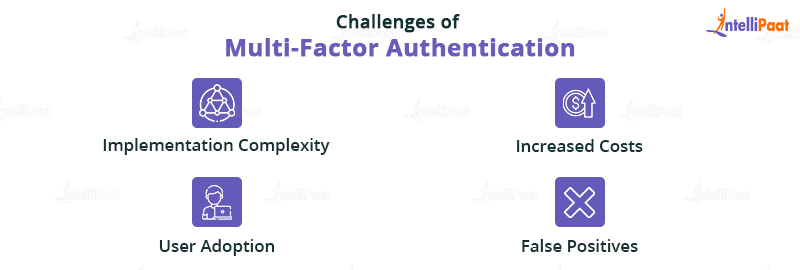
While multi-factor authentication provides increased security, it also presents challenges for organizations. Some of these challenges are the following:
Implementation Complexity
One of the most difficult aspects of multi-factor authentication is its implementation. MFA necessitates integration with existing systems, which can be difficult, particularly for organizations with legacy systems. Furthermore, deploying MFA takes time and requires thorough planning and testing to guarantee that it works properly.
Increased Costs
Implementing multi-factor authentication can be expensive, especially for small businesses. Implementing MFA incurs expenses due to the need for supplementary hardware and software. Additionally, maintaining and updating MFA systems can also add to the overall cost.
User Adoption
User adoption is another challenge of multi-factor authentication. Users may find the additional authentication steps tedious, and some may resist the change, leading to lower adoption rates. This can be especially true for users who are not tech-savvy or have limited access to technology.
False Positives
Multi-factor authentication can generate false positives, where legitimate users are denied access to a system due to authentication issues. This can be frustrating for users and result in low productivity.
Conclusion
Multi-factor authentication is an important security technique that helps protect businesses from cyberattacks and data leaks. It adds another layer of protection, minimizes the danger of data breaches, increases regulatory compliance, and enhances the user experience. However, establishing MFA can be difficult and expensive, and user uptake might be problematic. As the threat landscape evolves, organizations must consider multi-factor authentication as a critical component of their entire security strategy.
If you have any questions, drop them on Cyber Security Community.
The post What is Multi-Factor Authentication? appeared first on Intellipaat Blog.
Blog: Intellipaat - Blog
Leave a Comment
You must be logged in to post a comment.












