What is Enumeration? Definition, Types
This blog on Enumeration intends to help you understand what is Enumeration, the types of Enumeration and its tools, SMB enumeration, SNMP enumeration, NetBIOS enumeration, and enumeration technique, etc, and make you well-versed in cyber security. Go ALONG the blog to get an in-depth understanding of the enumeration.
The subjects we’ll be talking about are listed below:
- What is Enumeration?
- Types of Enumeration and its tools
- Techniques used for Enumeration
- Advantages of Enumeration
- Disadvantages of Enumeration
- Conclusion
Check out the Video for Ethical Hacking Course
Let’s start with Enumeration and get deeper insights through this blog:
What is Enumeration?
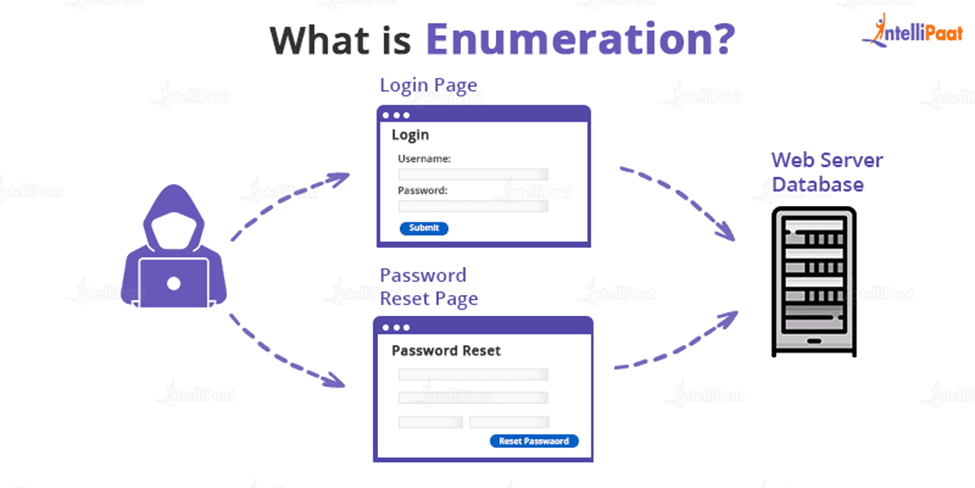
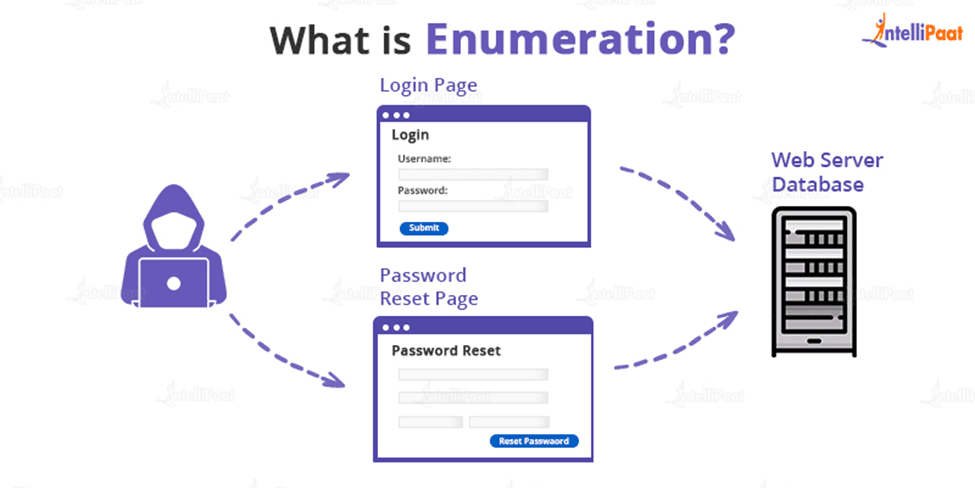
Enumeration is the process of obtaining information from a system, such as user identities, machine names, network resources, shares, and services. The attacker establishes an active connection to the system at this point and launches directed queries to learn more about the target. The information acquired is then utilized to pinpoint any weaknesses in system security that can be exploited during the system acquiring phase.
Enumeration is also called as Information Gathering Phase which is the first phase where hackers try to gather information and try to establish an active connection with the devices or systems. Attackers often evaluate attack vectors by using the output of the enumeration to exploit the system further. Additionally, malicious actors utilize penetration testing tools to gather data on network services and shares, IP routing tables, hostnames, DNS details, SNMP information, and users on database records.
To collect usernames, hostnames, IP addresses, passwords, configurations, and other information, enumeration is used. Hackers control the objective framework once a working connection has been established with the objective host. At that time, they steal personal information and data. Additionally, aggressors have occasionally been found to modify how the objective frameworks are set up. The information or data that the attacker will have access to depends on how the connection is set up to the host.
Are you interested? Check out Intellipaat’s Ethical Hacking Training Certification Course and enroll now!
Types of Enumeration and its tools
- Enumeration in SNMP: To maintain and control routers, hubs, switches, and other network devices on an IP network, SNMP (Simple Network Management Protocol) is an application layer protocol that makes use of the UDP protocol. A wide range of operating systems, including Windows Server, Linux, and UNIX servers, as well as network devices like routers, switches, etc., all have SNMP enabled by default.
- Tools: Tools required for SNMP are OpUtils, SolarWinds, SNScan, SNMP Scanner, NS Auditor
- Enumeration in DNS: Finding every DNS server and its accompanying entries for an organization is known as DNS enumeration. A map or an address book is analogous to DNS.
The process of translating an IP address (192.111.1.120) to the name www.example.com and back is actually similar to that of a distributed database.
Before launching an attack, DNS enumeration is performed to learn as much as possible about your target.DNS servers can provide details about prospective target systems, like usernames, machine names, and IP addresses. To find a lot of data, DNS enumeration is performed. Numerous sorts of data related to a domain are frequently stored in the DNS system.
- Tools: Tools required for Enumeration in DNS are nslookup, DNS Dumpster, and DNS recon.
- Enumeration in NetBIOS: NetBIOS uses 15 characters which are used for the device name, and the last character is reserved for the service or name record type in the 16-character NetBIOS name, which is a distinctive string of ASCII characters used to identify network devices over TCP/IP.
- Tools: Tools required for Enumeration in NetBIOS are hyena, NetBIOS Enumerator, nbtstat, and MegaPing.
- Enumeration in SMB: What was formerly known as Common Internet File System has been updated as SMB or Server Message Block. As an application layer network protocol, it functions. It is made to function as a file-sharing protocol. On a system, many applications can request services from a server inside a network while simultaneously reading and writing to files. The ability to run on top of the TCP/IP protocol or other network protocols is one of the intriguing features of SMB. A user or any authorized application or piece of software can access files or other resources on a remote server with the aid of SMB.
- Tools: Tools required for Enumeration in SMB are nmblookup, smbclient, nmap, and rpcclient.
- Enumeration in PCIe: A point-to-point interconnect is used by PCI Express (PCIe), and switches are used to fan out and increase the number of PCIe connections in a system. The process of discovering or enumerating every device in the PCIe tree during system startup is essential so that the system software can allocate resources to each one. The system software finds every switch and endpoint device connected to the system during the enumeration procedure, ascertains the amount of memory needed, and then configures the PCIe devices. Since they are configured differently from PCIe endpoints, PCIe switch devices constitute a specific situation in this process. Only their setting is necessary for the simulated testbench environment, though.
- Tools: Tools required for Enumeration in PCIe is pci-tool -i [-M]
Go through these Ethical Hacking Interview Questions and Answers to excel in your interview.
Techniques used for Enumeration
- User names can be extracted using email IDs
- Information can be retrieved using the default password.
- Active Directory using brute force
- Using SNMP, extract user names.
- Windows user groups can be extracted
- Utilizing DNS Zone transfer, more data
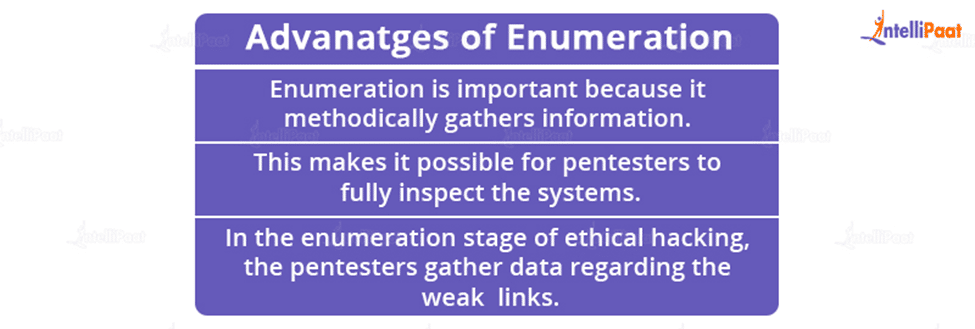
Advantages of Enumeration
- The most important element of ethical hacking is an enumeration. In the subsequent stages of penetration testing, the metrics, outcomes, and results are immediately applied to testing the system.
- Hostnames, IP tables, SNMP and DNS, applications, banners, audit setups, and service settings are all examples of detailed information that enumeration aids in deciphering.
- Enumeration is important because it methodically gathers information.
- This makes it possible for pentesters to fully inspect the systems.
- In the enumeration stage of ethical hacking, the pentesters gather data regarding the weak links.
This Ethical Hacking Tutorial will help you learn Ethical Hacking from scratch.
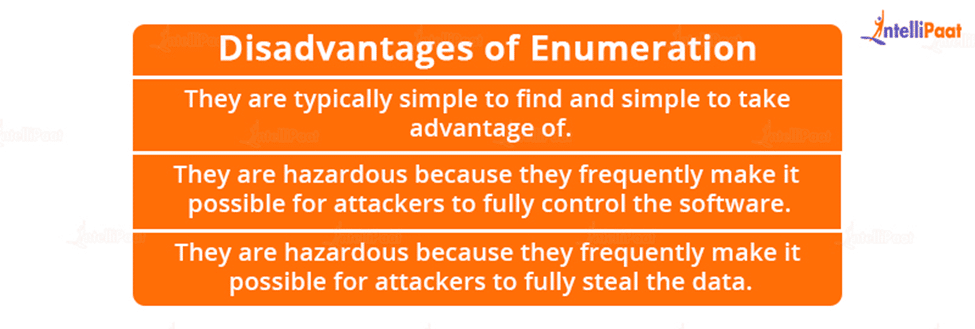
Disadvantages of Enumeration
- The tools and techniques used in this attack and how their malicious code might be easily loaded into an already-running computer to take advantage of a driver with an overflow.
- They are typically simple to find and simple to take advantage of.
- They are hazardous because they frequently make it possible for attackers to fully control the software.
- They are hazardous because they frequently make it possible for attackers to fully steal the data.
- Enumeration stops the software from functioning at all.
Conclusion
We have discussed In-depth the role of enumeration in Ethical Hacking which has gained a lot of popularity in the past decade. We hope this blog provides some tips for beginners to be able to better utilize their skills and make them understand the enumeration in ethical hacking, what are its types, the techniques used for enumeration, its advantages, disadvantages, and all other details enabling them to use in the real world situations.
Career Transition
For more information on Ethical hacking, visit our Ethical Hacking Community
The post What is Enumeration? Definition, Types appeared first on Intellipaat Blog.
Blog: Intellipaat - Blog
Leave a Comment
You must be logged in to post a comment.