What is Digital Signature in Cryptography?
Here’s what we’ll be discussing in this blog:
- What is Digital Signature?
- Digital Signature Algorithms
- How to Create a Digital Signature?
- Importance of Digital Signature
- Digital Signature Encryption
- Digital Signature Example
- Types of Digital Signature
- Conclusion
You can watch this Cyber Security video course:
What is Digital Signature?
We have been using handwritten signatures to authenticate handwritten or typed messages in the physical world for a long time. Their main use is to bind the signatory with a particular message. Digital Signature accomplishes the same thing with digital messages. The signatory, a person or an entity, is bound to digital data. This binding is verifiable by the receiver or a third party, if necessary.
Digital Signature in Cryptography is a value calculated from the data along with a secret key that only the signer is aware of. The receiver needs to be assured that the message belongs to the sender. This is crucial in businesses as the chances of disputes over data exchange are high.
Check out this Cyber Security Tutorial to learn Cyber Security Essentials!
Digital Signature Algorithms
There are three algorithms at work in Digital Signatures. They are as follows:
- Key Generation Algorithms – Key Generation Algorithms help ensure authenticity and integrity or it would be very easy to tamper with the data. They also prevent anyone from pretending to be the sender.
- Signing Algorithms – Signing Algorithms make one-way hashes of the data that has to be signed. Then they encrypt the hash value using the signature key. The encrypted hash along with the other information is the Digital Signature.
- Signature Verification Algorithms – Signature Verification Algorithms help process the Digital Signature and the verification key to generate some values. The algorithm also processes the same hash function on the data received and creates a hash value.
How to Create a Digital Signature?
Digital Signature is based on Public Key Cryptography. Let’s look at how a Digital Signature is created:
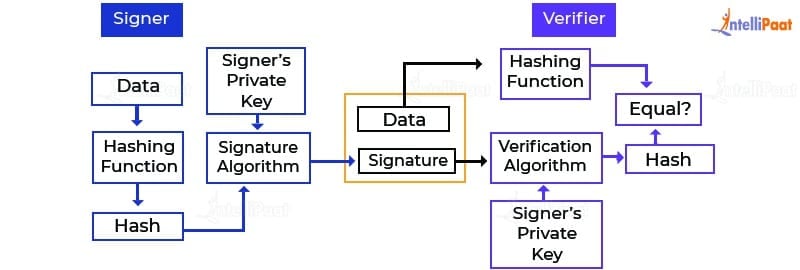
- People who adopt the Digital Signature scheme have a public-private key pair.
- The pairs for encryption/decryption and signing/verifying are usually different. The signature key is the private key that is used for signing and the verification key is the private key.
- The signer feeds all data to the hashing function and in turn, generates a hash of data.
- The signature key and hash value are fed into the signature algorithm to help produce a Digital Signature on the given hash. Once the signature is appended to the data, both are sent forward to the verifier.
- The verifier will then feed the Digital Signature and the verification key into the verification algorithm. The verification algorithm will generate an output value.
- Verifier is also responsible for running some hashing functions on the data received so it can generate a hash value.
- Verification is processed by comparing the hash value generated by the verifier and the output of the verification algorithm. The result of this comparison helps the verifier decide if the Digital Signature is valid or not.
- Nobody else has access to the private key of the signer and the Digital Signature is created using this key, so the signer cannot reject signing the document in the future.
Learn Cyber Security with this PG Program in Cyber Security!
Importance of Digital Signature
Digital Signatures are a very important tool in cryptography. Let’s find out why that is –
- Message Authentication – The private key is only known to the sender. The verifier can use the public key of the sender to validate that the Digital Signature was created by the sender.
- Data Integrity – If at any time the data is attacked, there will be a discrepancy in the hash value and the verification algorithm as they won’t match. Due to this, the receiver will end up rejecting the message and declaring a data breach.
- Non-repudiation – The signer is the only one who is aware of the signature key so, naturally, they are the only ones who can create a specific signature. Whenever there is a dispute, the data along with the Digital Signature can be presented as evidence.
Privacy, Integrity, Non-Repudiation, and Authentication can be provided as part of a cryptosystem if public-key encryption is added to the Digital Signature Scheme.
Preparing for a Job Interview? Check out our blog on Cyber Security Interview Questions!
Digital Signature Encryption
Sending an encrypted message is a safer choice than sending plaintexts. In public-key encryption, the sender’s public key is openly available and anyone can spoof their identity to send encrypted messages. The best way out of this is to use a Digital Signature along with encrypted messages.
Now, this can be done in one of two ways – sign-then-encrypt or encrypt-then-sign. The sign-then-encrypt system is prone to exploitation as the receiver could spoof the sender’s identity and send it to a third party. The encrypt-then-sign system happens to be more reliable and hence, widely accepted. We can illustrate this system with the following diagram –
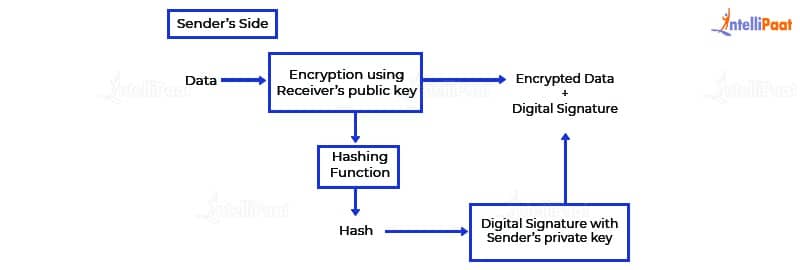
When the receiver receives the encrypted data, they first verify the signature with the help of the sender’s public key. Once the signature is verified, the verifier can decrypt the data using their private key.
Want to get an Advanced Certification in Cyber Security? Enroll today!
Digital Signature Example
To get a better understanding of the process, let’s look at a Digital Signature example step-by-step.
Let’s suppose you have to send a message to someone in ABC Office.

- The first step would be for you to type out the message or ready the file you want to send. Your private key would work as the stamp for this file. It could be a code or a password. Then you press send and the email reaches ABC Office via the internet.
- In the second step, the ABC Office would receive your file and verify your signature using your public key. They will then be able to access the encrypted file.
- The final step would require the ABC Office to use the private key that you’ve shared, to reveal whatever file you’ve mailed them. If the recipient doesn’t have your private key, they won’t be able to access the information in the document.
Learn Cyber Security and Ethical Hacking from MNIT faculty! Enroll today!
Types of Digital Signature
There are three types of Digital Signatures based on the technology they use:
- Simple
- Basic
- Advanced & Qualified
Simple Digital Signature
Simple Digital Signatures aren’t protected by any encryption methods. The email signature we add at the end of our emails is an example of Simple Digital Signatures. Since there is no encryption involved, the signer’s identity cannot be traced nor the changes made in the document after being signed. Simple Digital Signatures are very easy to replicate and don’t hold any legal power.
Career Transition
Basic Digital Signature
Basic Digital Signatures are not much different than Simple Digital Signatures. What makes Basic Digital Signatures different, is the fact that they can show the changes in the document after it was signed. This signature cannot refer to a verified identity and hence, it cannot guarantee identity security. The documents with Basic Digital Signatures do not hold any legal power.
Advanced & Qualified Digital Signature
Advanced & Qualified Digital Signatures are the safest Digital Signatures. They hold as much legal power as a signature on paper. These are created with asymmetric cryptography and public key infrastructure. Advanced and Qualified Digital Signatures can show where, when, and what devices should be used during the signing process. They also show all the changes made to the document post-signing.
Advanced & Qualified Digital Signatures are required to impose a two-factor authentication before the signing. These could be OTPs, biometric scans using mobiles, etc. The signatories have a unique electronic certificate attached to their identities.
Have any more queries? Ask away in the Intellipaat Community Forum!
Conclusion
Digital Signatures are an important tool in cryptography. They have become a regular thing in the day-to-day of businesses. Digital Signatures help bind the signatory to a digital message and keep it safe from attackers. What type of Digital Signature you need depends on what exactly do you need out of it.
Want to become an expert in Cyber Security? Enroll in our Cyber Security Master’s Program today!
The post What is Digital Signature in Cryptography? appeared first on Intellipaat Blog.
Blog: Intellipaat - Blog
Leave a Comment
You must be logged in to post a comment.













