What is ACL (Access Control List)?
What is Access?
In Simple terms, access means being able to get to what you require. The ability to obtain entry for specific data on a computer is referred to as data access. Web access is the ability to connect to the World Wide Web through an internet link or an online service provider.
The points to be discussed in this blog are:
- What is Access Control List?
- Functions of Access Control List
- Components of ACL
- Access Control List Types
- Access control List in Network Security
- Access Control List Examples
- Access Control List Rules and Regulations
- Conclusion
Refer to this YouTube video to understand the concepts of Cyber Security!
What is Access Control List?
Access Control List (ACL) refers to the process of monitoring and comparing data packets that flow in and out of a network. This allows administrators to ensure that the device cannot gain access unless the proper credentials are presented. A network access control list (ACL) is a set of rules that either allow or deny access to a computer environment. An ACL is similar to a guest list at a private club. Only those on the list are authorized entries.
Functions in Access Control List

As the definition implies, the primary function of an ACL is Security
-
Controlling network traffic flow
It regulates the control of flow. It is in control of every packet that leaves or enters the network. It ensures that no unnecessary or irrelevant packets are floating around the network. This can also protect the host from DDOS (Denial of Service Attacks), which occur when hackers flood the host network with a large number of data packets.
-
Better network performance
Because only local traffic is authorized by the Network Engineers, it leads to the overall network performance improvement.
-
Allocation of an adequate standard of security
The main goal of ACL is to provide security to your network, as the admin can grant and deny access to anyone. You can restrict users, packets from specific networks, or packets that follow a specific protocol, and you can also grant permission to packets.
Previously, ACL was the only way to implement Firewalls, but there are now many other options. Companies continue to use ACLs in connection with other technologies such as VPNs.
Learn more about cyber security check out cyber security tutorial!
Components of Access Control List
Most routing platforms implement ACLs in a similar manner, with general guidelines for configuring them.
Keep in mind that an ACL is a collection of rules or entries. An ACL can have a single or multiple entries, each of which is supposed to do something, such as permit everything or block everything.
When creating an ACL entry, you’ll need some information
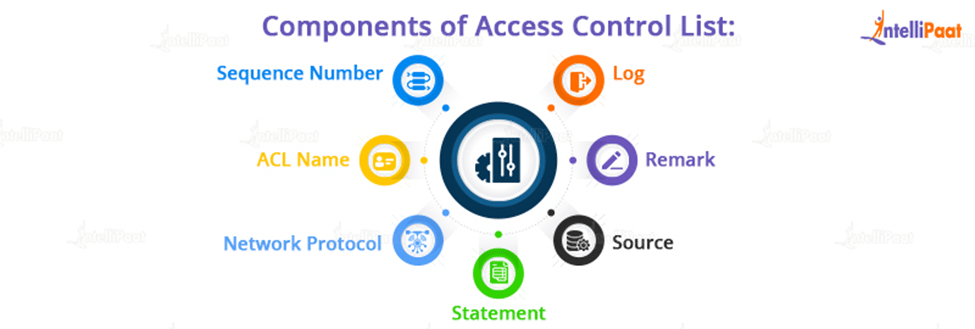
-
Sequence Number
Using a number, deny an ACL entry
-
ACL Name
Use a name to identify an ACL entry. Some routers allow a combination of letters and numbers instead of a sequence of numbers.
-
Network Protocol
Deny/allow IP, IPX, ICMP, TCP, UDP, NetBIOS, and other protocols.
Career Transition
-
Statement
Based on the address and wildcard mask, deny or allow a specific source. By default, some routing devices, such as Cisco, include an implicit deny statement at the end of each ACL.
-
Source
Define a single IP address, an address range (CIDR), or all addresses as the Source or Destination target.
-
Remark
Some Access points allow you to add comments to an ACL, which is useful for adding explicit details.
-
Log
When ACL fixtures are found, some devices can keep logs.
Want to Ace your interviews, then check out our cybersecurity interview questions!
Access Control List Types
There are four types of ACLs that can be used for various purposes,. Those are standard, extended, dynamic, and reflexive

-
Standard ACL
These are the Access-lists specifically developed with the source IP address. These ACLs either permit or prevent access to the whole protocol suite. They make no distinction between IP traffic types such as TCP, UDP, HTTPS, and so on. The router will recognize numbers 1-99 or 1300-1999 as a standard ACL and the specified address as the source IP address.
-
Extended ACL
These are the ACLs that make use of the source IP, the destination IP, the source port, and the destination port. We can specify which IP traffic should be allowed or denied using these types of ACLs. These ranges are 100-199 and 2000-2699.
-
Dynamic ACL
Extensive ACLs, Telnet, and authentication are used in dynamic ACLs. This type of ACL is also known as “Lock and Key” and can be used for specific timeframes.
These lists only allow a user to access a source or destination if the user authenticates to the device via Telnet.
-
Reflexive ACL
IP session ACLs are another name for reflexive ACLs. These ACLs filter traffic using upper-layer session information.
They respond to sessions initiated within the router by allowing or restricting outbound traffic. The router detects outbound ACL traffic and creates a new ACL entry for inbound traffic.
Access Control List in Network Security
The main goal of using an ACL is to secure your network. Without it, any traffic can enter or exit, leaving it vulnerable to unwanted and dangerous traffic.
An ACL can be used to improve security by denying specific routing updates or providing traffic flow control.
An ACL allows you to filter packets for a single or group of IP addresses, as well as different protocols such as TCP or UDP.
As an example, Instead of restricting only one host in the engineering team, you may limit access to the entire network and only allow one. You might also limit access to host C.
You can only allow port 80 and block everything else if the Engineer from host C wants to contact a web server in the Financial network.
Access Control List Examples
The most common examples of Access Control List include web servers, DNS servers, and remote access or VPN systems. The internal router of a DMZ contains stricter ACLs to protect the internal network from more specific attacks.
Web Access Control (WAC) is a cross-domain independent access control system that allows Linked Data systems to impose permission requirements on HTTP resources using the Access Control List (ACL) model.
An access control list listing clients permitted to receive an IP address matching a domain name of a target host is used to manage access to information from a DNS server. Receiving a client request for an IP address of a domain name at the DNS server and checking up the domain name in an access control list is part of the procedure. If the client is approved in the access control list to receive the IP address, the client receives a response containing the IP address of the domain name. The request is refused if the client is not allowed to receive the IP address.
Access Control Lists (ACLs) are used to control whether clients may connect to Message VPNs, which topics they can publish to, and which topics and share names they can subscribe to in that Message VPN.
If you want to get a certification in cybersecurity, don’t miss the opportunity to enroll in Intellipaat Cybersecurity Course!
Courses you may like
Access Control List Rules and Regulations
- The standard Access-list is frequently used near the endpoint (but not always).
- The extended Access-List is frequently used near the source (but not always).
- The names of standard and extended access lists cannot be the same.
- We can only assign one ACL per interface per protocol per direction, i.e., one internal and one outgoing ACL per interface
- We can only assign one ACL per interface per protocol per direction, i.e., one internal and one outgoing ACL per interface
- As there is an ambiguous deny at the conclusion of every access list, we need to include at least a permit statement in our Access-list, else all traffic will be refused
Conclusion
ACLs are package channels in an organization. They may regulate, allow, or prohibit traffic, which is critical for security. An ACL can be used to govern packet flow for a single or a group of IP addresses, as well as for other protocols such as TCP, UDP, and ICMP, among others.
However a stateful firewall provides significantly greater security, it might decrease network speed. However, an ACL is put directly on the interface, and the router processes it using its hardware capabilities, making it significantly quicker while still providing a high level of security.
For further queries and doubts, feel free to contact us at Cyber Security Community page!
The post What is ACL (Access Control List)? appeared first on Intellipaat Blog.
Blog: Intellipaat - Blog
Leave a Comment
You must be logged in to post a comment.













