What is a Man-in-the-Middle Attack (MITM Attack) ?
- What is Man in the Middle attack?
- Common types of MITM attacks
- Types of MITM attacks
- Man in the Middle Attack Tools
- Man in the Middle Attack Prevention
- Conclusion
Check out our YouTube video to know about Cyber Security
What is a Man in the Middle attack?
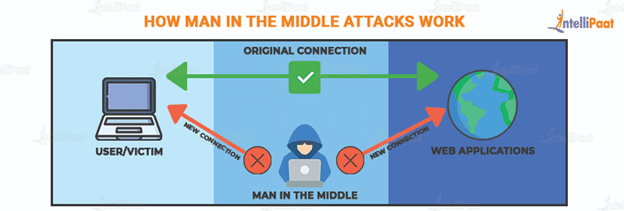
Man in the Middle attack (MITM attack) is a type of attack where a site or person collects your or your organization’s data for malicious reasons. Usually, such malicious reasons are inclined toward finance fraud.
With the growth of cyberthreat technologies, other parties impersonate popular sites to gain your trust. After gaining your trust, they eventually access your data.
In this attack, usually, your login credentials and card details, majorly credit card details, are targeted.
The attack is initiated by manipulating network traffic. Network traffic is manipulated by placing attack tools between interactions. Man in the Middle attack tools create a deceivingly similar network. In another methodology, the original interaction network is compromised. By hijacking the network, any existing authentication is removed to access your data.
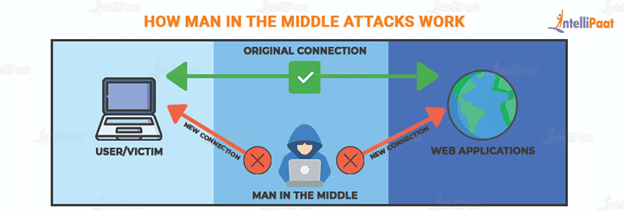
Generally, the attack happens on e-commerce sites where providing confidential data, such as residential address and social media login information, is a norm and requirement. Currently, data extraction methodologies in the attacks are automated; by typing any confidential data, the information is automatically reflected in the database of the third party.
As per a recent research done at the Technical University of Berlin, it was found that the authentication and key agreements in wireless technologies have flaws, which could be one of the major reasons why attacks happen more easily.
Enroll in our Cyber Security course now to learn from experts and get certified!
Following are common types of MITM attacks.
Common Types of MITM Attacks
- Interception of data: Interception of data happens by redirecting or directing you to a site that is deceivingly similar to the type of site that you initially clicked or searched; your data will be collected by a third party on the similar site. This is achieved by installing a packet sniffer in your network.
- Attack on bank account: One of the most common types of attack these days is the attack on bank accounts. This is initiated by contacting you over the phone or message. The other party poses as a representative of your bank. Usually, during the conversation, the only things that the other party knows is your name and the name of the bank.
The conversation usually hovers around your bank details being compromised by some third party. The conversation is followed by a promissory note that by providing your login information, you can protect your bank account immediately. When you provide your login information to the other party, they will contact your bank, usually impersonating you, stating that they would like to access your account.
Following are the different types of attacks being used at the current time.
Waiting and Preparing for the Interview. Check out Top 50 Cyber Security Interview questions!
Types of MITM attacks
- Cache poisoning: In this type of attack, your network system is compromised by manipulating your machine address. By converting your machine address into a local IP network, your computer proceeds with the connection to the address fixed by the other party.
This means that you might think that the connection is established to the site you chose, but in reality, the other party would have diverted the connection to a place where information can be collected easily. Since the new connection is deceivingly similar to the one chosen by you, it might take a while to find the difference.
- HTTPS spoofing: This Man in the Middle attack is almost similar to the one mentioned above. The difference is that the site usually has a minor change of syllable, phonetic alteration of syllables, or both. Though there might not be redirection, as in the previous case, the deceivingly similar site usually gets your attention while you are in search of a particular site. This happens because of the strategic marketing of the site by the other party. As a result of such marketing practices, the similar site is usually on the same page as the original site in the search engine results page (SERP.) On clicking on the third-party site, you will be provided with an authentication certification. On downloading the authentication certificate, the third party will be able to access your data.
- Eavesdropping of Wi-Fi: Have you ever come across free Wi-Fi in public? If yes, then this section might be of importance to you.
For the welfare of the general public, cybersecurity experts generally advise you to avoid free Wi-Fi networks.
But, why?
This is because open Wi-Fi networks are usually traps set by third parties. By connecting to an unsecured Wi-Fi network, your data and credentials can be accessed by third parties more easily.
The above-mentioned are a few of the common types of Man in the Middle attacks that are prevalent in the current times.
Career Transition
Check out Cyber Security Tutorial to learn more!
Man in the Middle Attack Tools
Following are the common tools that are used in Man in the Middle attacks.
- PacketCreator, Ettercap, dSniff, and Cain and Abel are usually used to intercept communication between hosts. The mentioned tools are more effective and efficient when used in LAN network environments.
- Proxy tools are used to manipulate HTTP protocol. The Man in the Middle attack proxy tools include OWASP, WebScarab, Paros, Burp Proxy, ProxyFuzz, and Odysseus.
Man in the Middle Attack Prevention
The following section will help you understand different ways to protect your data from MITM attacks.
- Enable VPN connectivity for all your devices.
- Employ an awareness campaign or any program of such nature where your employees can understand various mandatory concepts including common cyberattacks and cyberthreats.
- Enable additional cybersecurity measures by implementing PGP/GPG encryption system for your personal and work mail ids.
- Update your cybersecurity system frequently.
You can prevent your data from Man in the Middle attacks to a great extent by implementing the above-mentioned cybersecurity measures. It is to be noted that the above-mentioned are common measures and in case of doubt, it is always advisable to contact cybersecurity experts!
Conclusion
Man in the Middle attack is a common cyberthreat. By understanding what is Man in the Middle attack from the blog, you, by now, know that such attacks happen for malicious reasons only.
The attackers pry on data from those who possess credit cards and shop online regularly. You can protect your data by implementing adequate countermeasures. Since the prevention of Man in the Middle attacks is better than the cure, it is advisable to always be updated on the latest cyberthreats occurring in the industry or organizations around you. In this way, you can mitigate Man in the Middle attacks and protect your data effectively.
Courses you may like
Having any doubt and wanting to clear it. Check out this link and get your doubts clear on our Cyber Security Community!
The post What is a Man-in-the-Middle Attack (MITM Attack) ? appeared first on Intellipaat Blog.
Blog: Intellipaat - Blog
Leave a Comment
You must be logged in to post a comment.