What is a DNS Hijacking?
What is DNS?
The Domain Name System (DNS) is a directory system that associates an IP address with a website’s name. The Universal Resource Locator (URL) is sent to the DNS when you type a website’s name into your browser. This is referred to as a DNS request.
In response to the request, your browser receives the website’s IP address, which is its precise numerical location on the internet. You can access and communicate with the site once your device has an IP address.
Before exploring the world of DNS Hijacking, let us quickly have a look at the topics to be discussed in this blog:
Points at a Glance:
- What is DNS Hijacking?
- How is DNS Hijacked?
- Why are DNS servers being hacked?
- DNS Hijacking Attack Types
- How to Prevent DNS Hijacking?
- Tools used for DNS Hijacking
- Conclusion
Watch this youtube video, to get a better understanding of the topics we will be discussing.
So, let’s begin our learning!!
What is DNS Hijacking?
DNS hijacking is a type of attack that redirects users to malicious websites or pop-ups by using DNS queries. DNS is used by people who are not cyber criminals. ISPs may also hijack your DNS in order to redirect your traffic for their own purposes.
DNS hijacking was thought to be extinct not long ago. DNS hijacking has targeted many companies and organizations, including Gmail, Netflix, and PayPal.
Although all DNS hijacking functions work on the same fundamental principle – DNS exploitation – there are minor differences in how these attacks are carried out. These various types of attacks will be discussed further below.
A fully qualified domain name is the full URL that we enter into our browser (FQDN). This name can be broken down into three parts: a top-level domain (TLD), sub-domain, and host. Each of these elements represents a DNS server involved in the DNS request process.
Initially, your browser asks the DNS resolver for the whereabouts of the domain. This query is then forwarded by the resolver to the TLD’s DNS server, which queries the website’s DNS server, and can hijack any point along this “chain”.
Presently, your ISP (or Google) will automatically set up and configure your DNS settings.
These companies can use these settings to not only collect data but also to redirect you to websites and content that will benefit them.
The more malicious forms of DNS hijacking involve compromising DNS servers and inserting bogus IP addresses to redirect users to incorrect locations. Because DNS requests are frequently overlooked, these attacks can be difficult to detect and prevent.
Furthermore, because DNS requests are handled in such a way that each server involved seeks help from one “further along in the chain” to resolve the address, widespread DNS hijacking can spread quickly, affecting a large number of users and servers.
How is DNS Hijacked?
Cybercriminals recognize that your website’s domain name system is a distinct, trusted protocol and that many businesses fail to monitor their domains for malicious activity. As a result, they may be able to launch a variety of attacks against the organization’s Domain Name System with success.
DNS (Domain Name System) is a service that converts human-readable URLs into machine-readable Internet Protocol (IP) addresses. As a result, it can be used by internet users to match search queries to relevant websites. Every device that connects to the internet is given a numerical IP address. The NDS is required to synchronize domain names with IP addresses, allowing website owners and users to select memorable domain names.
Are you willing to find out more about cyber security?
What could be better than getting an overview with the click of a button? Visit our Cyber Security Tutorial!
Courses you may like
Why are DNS servers being hacked?
A DNS server can be hacked for a variety of reasons. The hijacker may use it for pharming (displaying advertisements to users in order to generate revenue) or phishing (redirecting users to a bogus version of your website in order to steal data or login information).
Domain redirection is also used by ISPs to control users’ DNS queries in order to collect user data. Domain hijacking is also used by other organizations to censor users or redirect them to other websites.
DNS Hijacking Attack Types
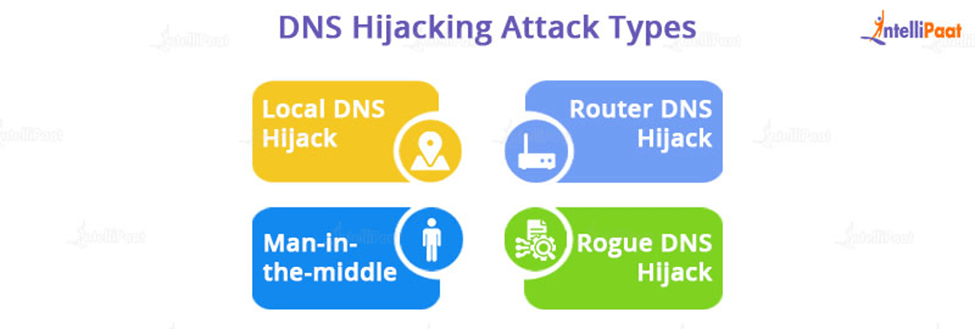
DNS hijacking can be accomplished in four ways by cyber criminals:
- Local DNS Hijack: This DNS hijacking method is used when a cybercriminal installs Trojan malware on the computer of a website user. This malware masquerades as legitimate software. When activated, it grants hackers access to network systems, allowing them to steal data and change DNS settings to redirect users to fraudulent websites.
- Router DNS Hijack: In this DNS hijacking method, hackers launch a DNS attack by overriding and reconfiguring a vulnerable DNS router (a hardware device used by domain service providers to link their domain names to equivalent IP addresses). Following that, the attackers will flood the website with traffic and redirect it to another malicious website, rendering the website inaccessible to users.
If you want to pursue a career in cyber security, the Cyber Security Course is a great place to start!
- Man-in-the-middle: DNS Hijacking occurs when hackers obstruct communication between a network user and a DNS server, eventually redirecting the user to an unknown destination IP address leading to malicious websites. Another term for it is DNS spoofing.
- Rogue DNS Hijack: An attacker compromises the DNS server, modifies its saved records, and redirects subsequent DNS queries to malicious websites that they usually own.
How to Prevent DNS Hijacking?
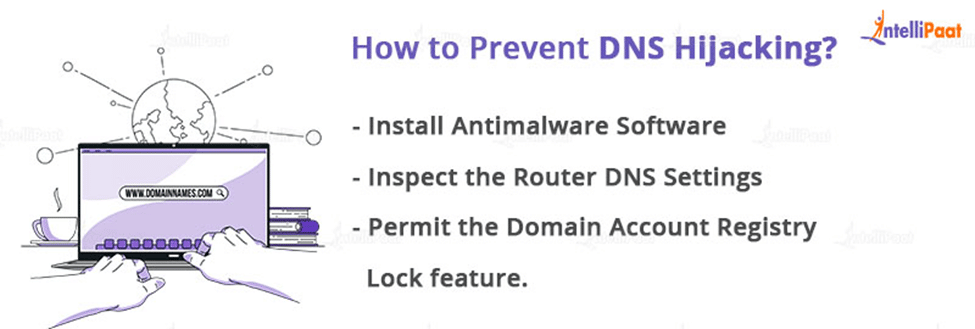
- Install Antimalware Software
DNS hijackers also attempt to steal users’ login credentials. Install antivirus software on your computer to detect any malicious attempts to expose your credentials by cyber criminals. To reduce the chances of your data being exposed, only use secure virtual private networks.
Create difficult-to-guess passwords and change them on a regular basis to further secure your credentials.
- Inspect the Router DNS Settings
Routers are vulnerable to attacks, and hijackers use this vulnerability to exploit victims. Check and double-check your router’s DNS settings for safety. Its passwords should be kept up to date as well.
- Permit the Domain Account Registry Lock feature.
Another method for preventing DNS hijacking is to use a registry lock against cyber threats.
A registry lock is a service provided by a domain name registry to detect unauthorized domain updates, transfers, and deletions. If your hosting company does not provide this service, look for one that does. As an added layer of security, enable two-factor authentication on your domain account.
Top 50 Cyber Security Interview Questions are intended for those who are preparing for interviews.
Tools used for DNS Hijacking

- ZoneWatcher
The goal of ZoneWatcher is to automate DNS system monitoring, reporting, and backup. You will always have a backup copy of your DNS records with this tool in case you need to recover from an unwanted update or if something goes wrong. It has a comprehensive changelog that allows you to review the entire history of changes for the whole zone. ZoneWatcher, primarily intended for professional use, allows you to monitor domains from multiple providers if you work with many clients. It also allows you to form teams to divide the monitoring staff according to the managed entity. The alerts can be sent via email, and the data can be exported as zone files or notified using a REST API.
- StatusCake
When it is time to renew your domain, the StatusCake domain monitoring tool notifies you so that squatters do not take over your domain and cause a loss in your business if you fail to renew your domain before the deadline. You can also monitor changes to your DNS records.
StatusCake offers three plans, the first of which is free with limited features and a 5-minute testing interval. Paid plans with extra features like SMS alerts, 30-second testing intervals, and team tools are also available for a free trial.
- AppNeta
Although AppNeta’s DNS monitoring approach is adaptable to any network architecture, it is particularly suited to organizations in the process of cloud migration. It employs a comprehensive monitoring engine that monitors both internal and external servers and collaborates with a number of ISPs and DNS providers.
AppNeta stores the data it collects for free for one year. Analyzing that data allows you to visualize the impact of DNS resolution on the user experience of your application. Patterns in performance spikes can also be detected, as can degrading trends in performance. To assist IT staff, in identifying DNS resolution issues related to application problems, the application context is added to the monitoring service’s reports.
Career Transition
Conclusion
Since the inception of the internet, hackers and scammers have devised numerous methods to obtain user information, including DNS hijacking. Numerous techniques are only applicable to DNS-related vulnerabilities.
We hope that this blog helped you understand the concept of DNS and DNS Hijacking.
If you face any challenges, feel free to contact our Community Page. Till then keep learning!
The post What is a DNS Hijacking? appeared first on Intellipaat Blog.
Blog: Intellipaat - Blog
Leave a Comment
You must be logged in to post a comment.













