What Is A Cipher? A Complete Overview
There are two kinds of cryptography in this world: cryptography which will stop your kid sister from reading your files, and cryptography which will stop major governments from reading your files. – Bruce Schneier
Overview
Ciphers are typically classified based on how they operate and how their key is utilized for encryption and decryption. Block ciphers aggregate symbols in a fixed-size message (the block), whereas stream ciphers use a continuous stream of symbols. A symmetric key algorithm or cipher employs the same key for encryption and decryption. For encryption and decryption, asymmetric key algorithms or ciphers employ a separate key.
Are you exploring Ciphers…! then you have landed at the right place. In this blog, we will explain Cipher’s working, its types, and its uses.
Are you excited to learn about CyberSecurity..! Here’s a video for you
Table of Contents:
- What do we mean by Cipher?
- How does a Cipher work?
- What is the Purpose of Ciphers?
- Types of Ciphers
- Examples of Cipher
- Conclusion
What do we mean by Cipher?
Here is our definition of the cipher. Cipher is a frequently used algorithm in cryptology, a subject concerned with the study of cryptographic algorithms. It is a method of encrypting and decrypting data.
- The adoption of a symmetrical cipher will determine the secret or symmetric key encryption.
- The symmetric algorithm applies the same encryption key and cipher to the data in the same way.
- The goal might be to transform plain text to ciphertext or vice versa.
- The cipher analyses the original and plaintext data to generate ciphertext that seems to be random data.
Symmetric key encryption, often known as secret key encryption, is based on the usage of symmetric ciphers. The same encryption key is applied to data, in the same way, using symmetric encryption methods, whether the goal is to convert plaintext to ciphertext or ciphertext to plaintext.
A cipher converts data by converting plaintext characters or other data into ciphertext. The ciphertext should be represented as random data. Ciphers have traditionally employed two basic forms of transformation:
- Transposition ciphers maintain all of the original bits of data in a byte but reverse their order.
- Substitution ciphers substitute specified data sequences with alternative data sequences. For example, one type of replacement would be to convert all bits with a value of 1 to bits with a value of 0, and vice versa.
The ciphertext is the data produced by any technique.
Modern cipher approaches employ private communication in various networking protocols such as TLS, or transport layer security, which enables network traffic encryption. Many communication systems, like digital televisions, phones, and ATMs, employ ciphers to provide privacy and security.
Learn more about the Cybersecurity tutorial!
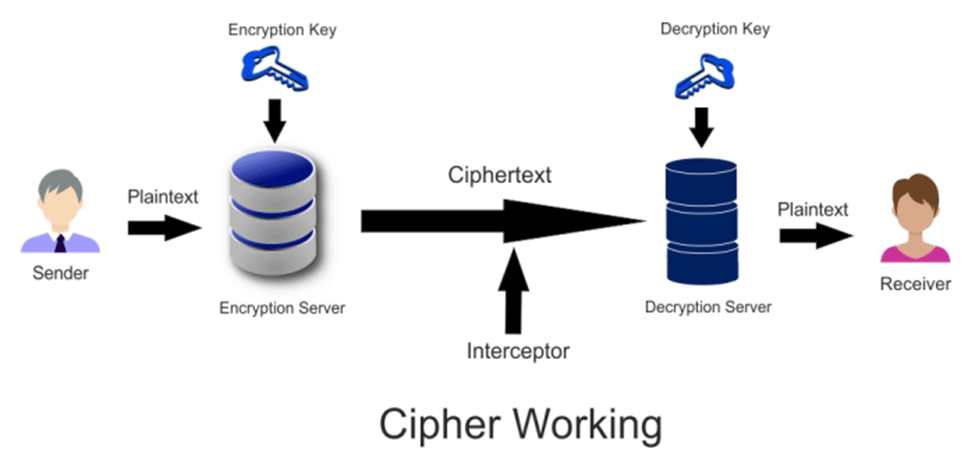
How does a Cipher Work?
The operation of a cipher is rather fascinating. It employs a predefined set of rules or methods to convert plaintext or a legible message into ciphertext, which is nothing more than a string of random letters. The stream ciphers might be constructed to encrypt or decode the bits. They can also process the ciphertext into uniform blocks of a specific amount of bits, which is known as a block cipher.
Modern cipher implementations rely on the algorithm and a secret key, which is utilized by the encryption algorithm to change data as it is encrypted. Ciphers with longer keys (measured in bits) are more resistant to brute-force assaults.
The longer the key, the more brute-force efforts are required to disclose the plaintext. While cipher strength is not necessarily reliant on key length, experts recommend that current ciphers be designed to employ keys of at least 128 bits or more, depending on the algorithm and use case.
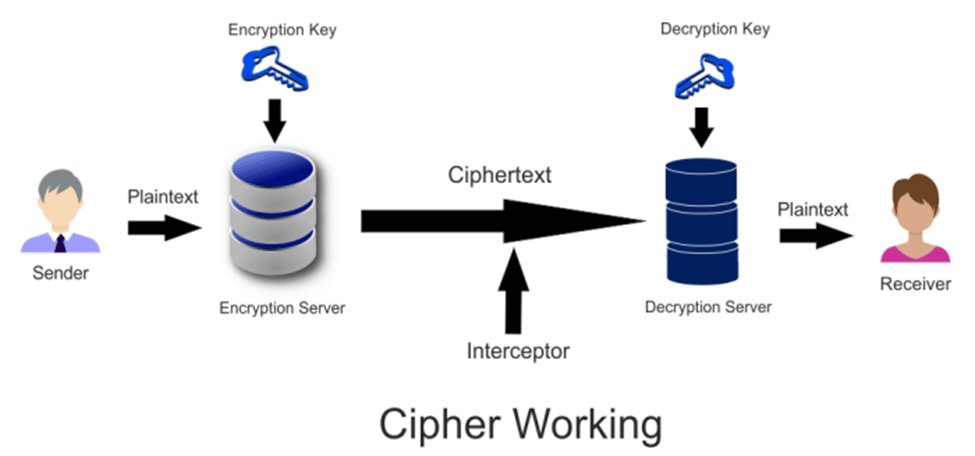
A key is such an important aspect of an encryption technique that, in real-world ciphering, the key is kept secret rather than the algorithm. Strong encryption methods are built in such a way that, even if someone understands the technique, interpreting ciphertext without the necessary key should be difficult. As a result, for a cipher to operate, both the sender and the receiver must have a key or a set of keys.
The same key is utilized for data encryption and decryption in symmetric key techniques. To encrypt and decode data, asymmetric key algorithms employ both public and private keys.
Asymmetric cryptography, often known as public key cryptography, uses huge integers that have been paired but are not identical (asymmetric). Here are some examples of key pairs:
- Everyone has access to the public key.
- The private key, often known as the secret key, is kept confidential.
Either key can be used to encrypt a message; the opposite key used to encrypt the message is used to decode it.
The owner of the key pair uses the private or secret key to decrypt or encrypt data, whilst the public key is used by anybody who wishes to encrypt a message that can only be deciphered by the holder of the private key.
So, have you decided to pursue a career in cyber security? For further information, please see our Intellipaat Cybersecurity Course.
Courses you may like
What is the Purpose of Ciphers?
Symmetric ciphers are the most often utilized for internet communication security. They are also included in a variety of network protocols for data sharing. Secure Sockets Layer and TLS, for example, employ ciphers to encrypt application layer data, particularly when used with HTTP Secure (HTTPS).
To safeguard data transmission, virtual private networks that connect remote workers or branches to corporate networks utilize protocols using symmetric key algorithms. Most Wi-Fi networks, online banking and e-commerce services, and mobile telephony use symmetric ciphers to ensure data privacy.
Asymmetric cryptography is used by several protocols to encrypt and authenticate endpoints. It is also used to safeguard the exchange of symmetric keys for the encryption of session data. Among these protocols are the following:
- HTTP
- TLS
- Secure Shell
- Secure/Multipurpose Internet Mail Extensions
- Open Pretty Good Privacy
Public key cryptography is more secure than symmetric encryption, but it is also more computationally demanding. Protocols frequently use symmetric key methods to encrypt session data for performance reasons.
Wanna Know about the CyberSecrity Tools..! Here’s a video for you
Types of Ciphers
Ciphers can be classified in a variety of ways, including the following:

- Block ciphers encrypt data in equally sized blocks.
- Stream ciphers can be used on data streams that are often received and transferred via a network.
Ciphers can rely on traditional keys that are directly used to key ciphertext or on elliptical curve cryptography (ECC). When employed with a 160-bit key, ECC may give the security of a classical cipher, such as that used in the RSA (Rivest-Shamir-Adleman) cryptosystem with a 1,024-bit key.
Modern encryption algorithms are built to survive assaults even when the attacker is aware of the cipher being employed. Ciphers have historically been less safe against attack since they were used to encrypt plaintext by hand and could be quickly examined and cracked with computer power.
Do you wanna crack the Next Interview of CyberSecurity with an ACE..! here’s an opportunity for you Top CyberSecurity Interview Questions!
Examples of Cipher
The following are some well-known historical ciphers:
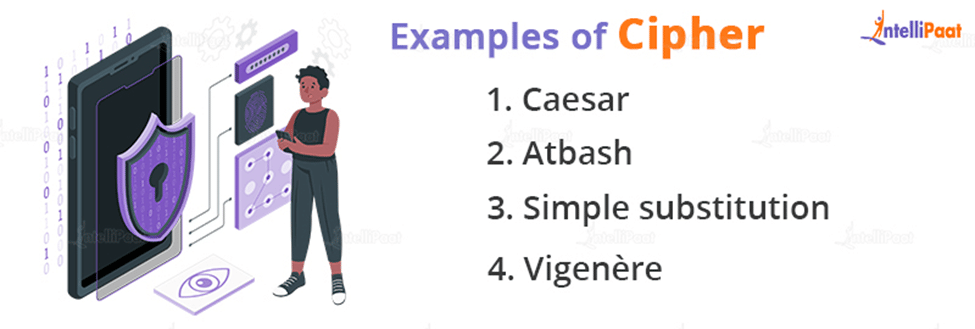
- Caesar: This cipher is supposed to have been employed by Julius Caesar to communicate securely with his generals. It is a straightforward substitution cipher in which each letter in the plaintext is moved a predetermined number of positions down the alphabet.
- Caesar is supposed to have worked three shifts.
- Substitution ciphers are frequently implemented by putting down the plaintext alphabet, followed by the ciphertext alphabet, shifted by the number agreed upon by those talking.
- A three-letter shift places the letter D over the plaintext A, E above B, and so on. A basic form of a key is the number of characters moved.
- Atbash: This cipher is a substitution cipher in which the plaintext alphabet is projected back onto itself. In other words, plaintext letter A is mapped to ciphertext Z, plaintext letter B is mapped to Y, plaintext letter C is mapped to X, and so on.
- Atbash is called after the Hebrew alphabet’s first and last letters. It is believed to have been used for hundreds of years.
- Simple substitution: This one has been used for hundreds of years as well. It replaces each plaintext letter with a new ciphertext character, resulting in a 26-character key.
- It varies from the Caesar cipher in that the enciphering alphabet is totally scrambled rather than just moved to a certain number of positions.
- Vigenère: This cipher is a polyalphabetic substitution cipher, which means it is based on substitution using many replacement alphabets. The Vigenère cipher employs a sequence of interwoven Caesar ciphers based on a keyword’s letters. The original text is encrypted with the Vigenère square or Vigenère table.
Career Transition
Conclusion
Therefore, The Cipher is a method of encrypting a communication. It translates a message by applying the cipher algorithm to transform the data that represents the message’s words and characters. Ciphers can be constructed quickly, and the cipher algorithm can be simply automated and programmed.
Do you have any queries related to cybersecurity..! You are just one click away from our Cyber Security Community Page!
The post What Is A Cipher? A Complete Overview appeared first on Intellipaat Blog.
Blog: Intellipaat - Blog
Leave a Comment
You must be logged in to post a comment.