The Future of Cloud Security: Evolving Strategies for Protecting Critical Digital Assets
Blog: Comidor Blog
Over the past decade, cloud security has consistently been at the forefront of technological discussions. Despite countless debates and dialogues, concerns are still present. The digital age has brought with it a plethora of advantages, but it has also ushered in new challenges. People seek clarity and transparency, not just about the technical aspects of where their data resides, but also about the processes safeguarding it.
Cloud security has been so hot to debate about, that even after a decade or so, we started to rethink how to use common terms such as “web application”, “internet of things” etc. in a politically correct manner…As a consequence, politically correct vendors have taken all the necessary measures to assure and reassure customers about their security mechanisms implemented on top of SaaS, PaaS, etc.
– And why are we STILL talking about cloud security?
– It’s because people have a mental disorder about their stuff!
Let me explain. It is OK for someone to have his stuff “somewhere” stored securely, as long as he knows (or at least he thinks he knows) where his stuff is. The problem starts when you tell him: “Listen, to have the requested service, I have to transfer a bit of your stuff here, process it, and then store it temporarily over there… Don’t worry. It will be all secure and you won’t notice anything”.
Nop. No way! No matter the Service-Level Agreement (SLA) or the fancy security you implement there will always be a prejudice towards your service. It’s not about your service. It’s about knowing where my stuff is at any given time! So, what can you do as an honest SaaS vendor for your security “aware” customers? A lot! Basically, you have to alleviate their concerns over multi-tenancy, virtualization, and unauthorized information flow.
 The Changing Landscape of Cloud Security
The Changing Landscape of Cloud Security
Technological advancements and their impact
The realm of cloud security is in constant flux, largely due to rapid technological advancements. New technologies emerge, bringing both opportunities and challenges. The rise of edge computing, for instance, decentralizes data processing, offering faster response times but also introducing new security concerns. Blockchain technology promises enhanced security through decentralized ledgers, but it also introduces challenges and learning curves that businesses must face.
Businesses must stay updated, ensuring they harness the benefits of new technologies while mitigating potential risks. A proactive approach to understanding and implementing these advancements can set businesses apart, offering a competitive edge in the digital landscape.
Adapting to evolving threats
Threats in the digital world are not static. Cybercriminals continually devise new methods to breach defenses, exploiting system vulnerabilities. Ransomware attacks have seen a significant rise, targeting both large corporations and small businesses. Such threats underscore the importance of robust and adaptable security measures.
Beyond immediate threats lies the challenge of future-proofing. Technology’s rapid evolution means that the methods of those with malicious intent also evolve. Vigilance is key: anticipate potential vulnerabilities to ensure defenses are not just current but also prepared for future challenges.
The Human Element: Knowing Where Data Resides
The psychological aspect of data security
Many concerns about cloud security stem from a fundamental human need: the desire to know and control. The vastness of the digital realm can feel overwhelming, leading to apprehension about data misplacement or misuse. Aside from the tangible security measures, service providers must address this psychological dimension.
Building trust and providing reassurance are as crucial as the technical defenses in place. Addressing human concerns can pave the way for a more secure and trusting digital environment. When users feel their data is not just protected but also respected, they are more likely to engage with digital services confidently.
Building trust in the digital age
Trust is a critical component of any business relationship, especially in the realm of cloud security. Service providers must go beyond mere technical assurances. Transparent communication, clear data handling policies, and regular updates can bridge the trust gap, fostering stronger relationships.
Engaging with customers, addressing concerns proactively, and demonstrating a consistent track record of security is essential. The digital age demands both technical proficiency and emotional intelligence. Trust, once earned, must be continuously reinforced through actions, transparency, and open communication.
Data Access Management: The Heart of Cloud Security
The role of intelligent systems
Effective data access management goes beyond setting up barriers. Businesses require intelligent systems that adapt to evolving threats. Machine learning and AI-driven security protocols can predict potential breaches based on patterns. Such proactive approaches to security are becoming increasingly essential in a dynamic digital landscape.
Business growth and diversification complicate data access needs. Intelligent systems streamline access, ensuring the right individuals access the right data at the right time. Enhanced security, combined with efficiency, can drive business growth, ensuring data remains both accessible and secure.
Governance guides the way
Governance plays a crucial role in cloud security. It’s about setting rules and aligning those rules with broader business objectives and compliance requirements. A robust governance framework provides direction, ensuring security measures are cohesive and in line with organizational goals.
Regular reviews and updates to governance policies are crucial. The digital landscape is always changing, and governance strategies must adapt as well. A proactive approach to governance, combined with a commitment to continuous improvement, can ensure that businesses remain at the forefront of cloud security.
Innovations Shaping Tomorrow’s Cloud Security
The novel protective measures
The cloud security landscape continually evolves, introducing groundbreaking protective measures. Quantum encryption methods offer a level of data protection that seems almost magical: using the principles of quantum mechanics, these methods secure data in ways that leave unauthorized parties baffled.
On another front, AI-driven threat detection systems redefine the game. These proactive systems identify and neutralize threats, often spotting them before they wreak havoc. Analyzing and processing vast amounts of data in real time, they detect patterns and anomalies, setting a new standard for security.
Adapting to a decentralized security model
Decentralization marks a significant trend in today’s cloud security. With blockchain and distributed ledger technologies on the rise, security models are shifting towards a decentralized paradigm. Distributing data across multiple nodes means that a compromise in one node doesn’t spell disaster for the entire system.
Edge computing is on the rise, too, and it also challenges traditional notions of cloud security. Processing data closer to its source minimizes the need for long-distance data transfers. While this enhances processing speed, it also presents fresh security challenges. Security measures must now evolve, guarding data at every potential point of vulnerability.
 An Essential List for Cloud Security
An Essential List for Cloud Security
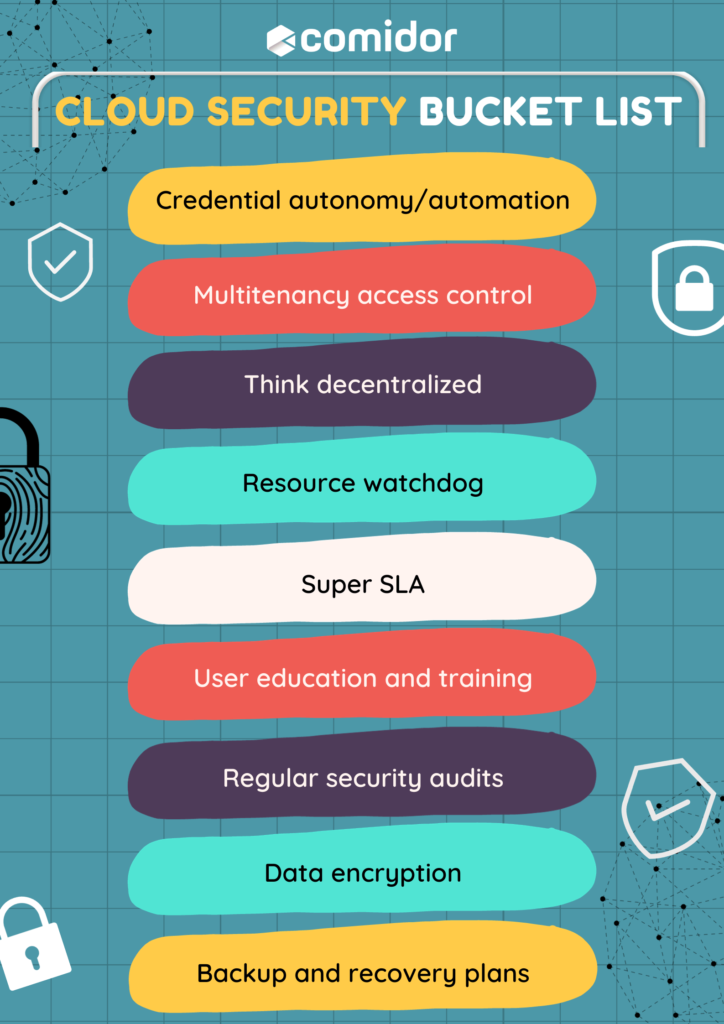
Cloud security is more than just a technical challenge. It’s a set of measures that ensure peace of mind for users. Here’s an essential list every SaaS vendor should consider:
- Credential autonomy/automation: As cloud users invoke services across multiple clouds, it’s vital to provide levels of data access control that support the transfer of customer credentials across different layers of services and resources. Imagine this as the user’s global cloud Single-Sign-On, ensuring persistent authorization of their identity across multiple clouds. This not only streamlines access but also enhances security, ensuring that user credentials are consistently and securely managed.
- Multitenancy access control: When allowing access to multiple domains, interference among tenants can arise due to flawed access control mechanisms. Regular evaluations of access policies prevent unauthorized information flow that could lead to side-channel attacks. With the digital landscape’s complexity, ensuring that each tenant’s data remains isolated and secure is of utmost importance.
- Think decentralized: Predicting the granularity of your services’ access control over their resources can be challenging. Adopting a decentralized approach allows each service to retain administrative control over its resources. This flexibility is invaluable when dealing with multiple independent clouds, each with its unique set of authorization rules.
- Resource watchdog: Managing multiple and diverse cloud environments necessitates a vigilant eye on virtual resources. Implementing a Resource Watchdog ensures continuous monitoring of deployed resources, guaranteeing their availability. Beyond just availability, this tool is instrumental in addressing scalability issues, ensuring that both users and resources can adapt to changing demands.
- Super SLA: Different policy models are often implemented for resources and services. Crafting a robust SLA that enforces secure collaboration between domains is essential. This SLA ensures that the services offered align with the agreed-upon access control rules, providing a consistent and secure experience for users.
Additional considerations for cloud security
- User education and training: While technical measures are vital, educating users about best practices can significantly enhance security. Regular training sessions can equip users to recognize potential threats, making them an active participant in the security process.
- Regular security audits: Periodic security audits can identify potential vulnerabilities and ensure that all security measures are up-to-date. These audits provide an opportunity to reassess and refine security strategies, ensuring they remain effective in an ever-evolving landscape.
- Data encryption: Encrypting data, both at rest and in transit, adds a layer of security. Advanced encryption methods can ensure that even if data is accessed by unauthorized parties, it remains unintelligible and useless.
- Backup and recovery plans: Having robust backup and recovery plans in place ensures that, in the event of a breach or system failure, data can be restored quickly — minimizing downtime and potential data loss.
 Conclusion
Conclusion
The digital age, with its myriad opportunities and challenges, demands a proactive approach to cloud security. Understanding the human elements, adapting to technological changes, and investing in continuous learning are the essential steps of this approach. To navigate the complex landscape of cloud security with confidence and foresight — stay informed, vigilant, and adaptive.
Author bio:
 Lisa Levy
Lisa Levy
Lisa works as a content specialist at Satori, the Data Security Platform. She has published several books, white papers, and articles across a diverse collection of topics.
The post The Future of Cloud Security: Evolving Strategies for Protecting Critical Digital Assets appeared first on Comidor Low-code Automation Platform.
Leave a Comment
You must be logged in to post a comment.









