SAML vs. OAuth: Key Differences Between SAML & OAuth
What do you mean by SAML and OAuth?
SAML:
An authentication method is security assertion markup language (SAML). When you log into your work computer in the morning, you’ve almost certainly used SAML.
OAuth:
A type of authorization process is an open authorization (OAuth). You can switch between services without entering a new username and password. You’ve used OAuth if you’re logged into Google and used those credentials for Yahoo.
This is just the overview, the topics to be covered in this blog are:
Table of Content
- What is SAML?
- Working of SAML.
- What is OAuth?
- Working of OAuth
- Differences between SAML and OAuth
- Similarities between SAML and OAuth
- When Should You Use SAML or OAuth?
- Conclusion
Check out the overview of the topic here:
What is SAML?
The name, first and foremost: Security Assertion Markup Language. SAML, like most “X Markup Language” applications, is built on XML. The other half of the name accurately describes the purpose of SAML, which is to enable one system to assert a user’s identity to another after first verifying that user’s identity.
You’ll notice that the name does not include the words “web,” “internet,” or “SSO.” Although these are the most common SAML applications, they are far from the only ones. SAML is, at its core, a general framework that is not specific to any use case or technology, and it has both advantages and disadvantages.
It can be used in a variety of scenarios because it is general; however, because of its flexibility, the configuration can be complicated because different implementations make different assumptions. It also implies that the raw configuration includes a significant amount of boilerplate for configuring SAML for Web SSO.
Working of SAML
- SAML is an open standard for identity verification and authentication. To gain access to any of the company’s internal functions in a typical office setting, an employee must log on.
- Following successful SAML authentication, the user may have access to a comprehensive set of tools, such as a corporate intranet, Microsoft Office, and a browser. SAML grants the user access to all of these resources with a single digital signature.
- In more secure organizations, SAML only allows the user to open a door or unlock a computer screen. Before the user can do anything else, including access files, they must be authorized.
- SAML allows network administrators to manage users from a centralized location.
Become an expert in cyber security and build a successful career through Intellipaat’s Cyber Security online course.
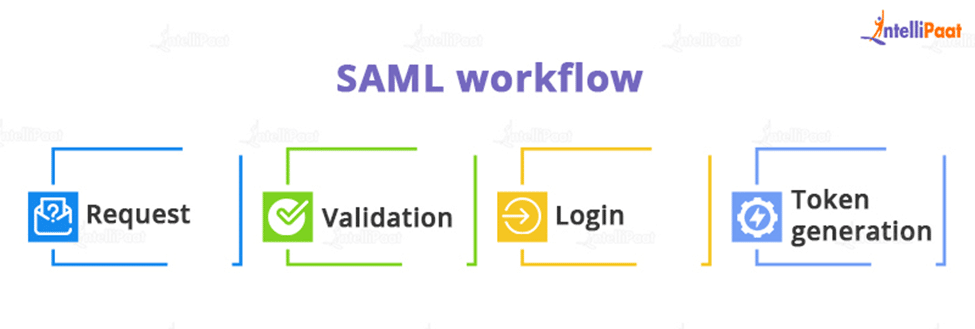
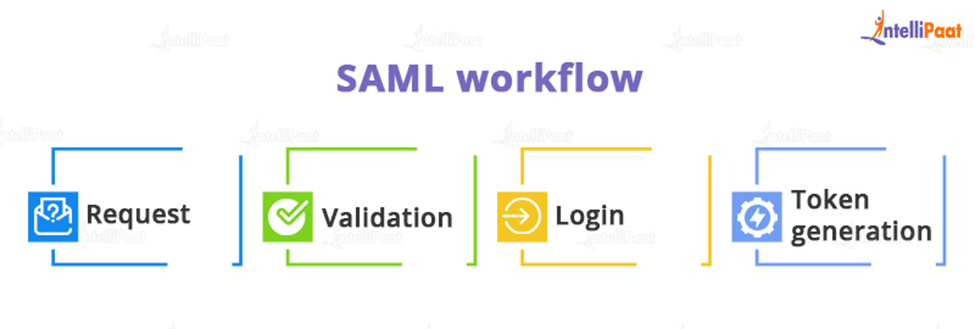
A typical SAML workflow is as follows:
- Request: To make a request, a user clicks the “Log in” button.
- Validation: For authentication, the SAML and the identity provider connect.
- Login: A screen appears in which the user’s username and password are requested.
- Token generation: If the user enters valid information, a SAML token is generated and sent to the service provider, allowing the user to log in to the server.
This workflow allows a service provider, a browser, and an identity provider to exchange data in real-time. The user may be unaware of the delay because this process is usually completed in seconds.
What is OAuth?
OAuth is an open-standard authorization protocol or framework that provides “secure designated access” to applications. You can, for example, tell Facebook that ESPN.com is allowed to access your profile or post updates to your timeline without giving ESPN your Facebook password. This significantly reduces risk: even if ESPN is compromised, your Facebook password will remain secure.
OAuth does not share password information and instead relies on authorization tokens to connect consumers and service providers. OAuth is a protocol for authorizing one application to interact with another on your behalf while keeping your password private.
Become a qualified professional, check out Cyber Security Courses.
Working of OAuth
While “auth” can refer to either authentication or authorization, we use it specifically for authorization in the OAuth protocol. This protocol is used to transfer authorization from one service to another while protecting the username and password of the user.
In an environment where the average employee switches job-critical applications 1,100 times per day, consider OAuth to be a lifesaver. Employees occasionally want to be able to switch from one app to another without logging in again. OAuth makes this possible.
Consider the case of a worker who has a Google account. That person could use the same credentials to access data on:
- HotJar
- Microsoft 365
- Hootsuite
- Marketo
- SurveyMonkey
- Box
- Salesforce
All of these web-based programs are required for the employee to do the job correctly. The prospect of creating (and remembering) five different sets of usernames and passwords, on the other hand, may make the same person cringe.
Duplicating usernames and passwords are dangerous. If one site fails, the user’s sensitive data becomes exposed and vulnerable across all platforms. However, logging into another site using the first’s validation is a completely different story.
Some customers are concerned about data mining and believe that using such a tool gives companies such as Facebook too much power. Every time a user chooses a Facebook login for other apps and sites, Facebook gains more customer insight. Furthermore, if a person’s Facebook data is compromised, their additional logins may fail as well.
Crack Cyber Security jobs with the help of Cyber Security interview questions!
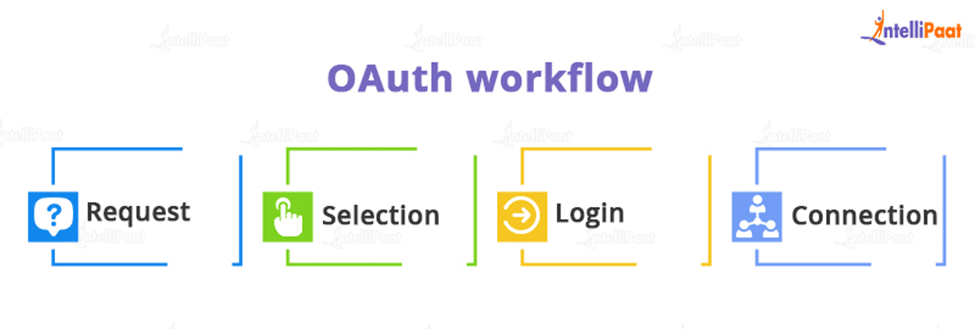
A typical OAuth workflow is as follows:
- Request: On a web page, a user clicks the “Log in” button.
- Selection: The client selects the third-party authorization credentials.
- Login: When you log in, the authorization server generates an access token, which is then sent to the resource server.
- Connection: The resource server grants access after validating the token.
Throughout this process, information is passed back and forth between the two servers. OAuth typically uses JWT for tokens, but it can also use JavaScript Object Notation.
Tokens, regardless of how they are generated, are always encoded, usually signed, but rarely encrypted as they travel from server to server.
Career Transition
Differences between SAML and OAuth
When comparing SAML vs OAuth, the following two tools are used for different tasks:
Authentication: This procedure entails identifying the user. SAML functions similarly to a home key. It gives you access to the facility.
Authorization: It is a procedure that involves the permissions of a user. OAuth is analogous to home rules, which govern what a person can and cannot do at home.
SAML Use Case: For Single Sign-On, SAML is widely used in government and corporate applications where XML processing is prevalent (identity management). SAML is used in many government citizen ID programs (for example, UK Verify).
This protocol allows users to be managed from a central location. This is how you connect to your company’s computer and network. To gain network access, users only need to enter their credentials once.
OAuth Use Case:
OAuth 2.0 is widely used in user and corporate applications for authorization and authentication. It is most commonly used to authorize access to RESTful APIs, where the use of access tokens facilitates the process.
This protocol is also used to switch between services without having to enter your login information again. This is achieved by enabling you to transfer your credentials from one service to another.
The most common use case for OAuth in the corporate world is in conjunction with Identity and Access Management (IAM) solutions. It can be used to allow users to use an application.
Similarities between SAML and OAuth
Both of these authentication methods enable SSO by eliminating the need for unnecessary usernames and passwords, and they are based on open standards for verifying identities and granting access to protected resources via centralized administration. Simple enrollment and delegated user management benefit IT administrators. The standards may even be mutually advantageous, promoting interoperability. For example, authentication servers can use the OAuth assertion flow to obtain authorization grants from SAML-trusted IdPs.
When Should You Use SAML or OAuth?
SSO is enabled by both SAML and OAuth, which is critical for productive employees. They are not exact substitutes, but rather complementary technologies.
In the Microsoft environment, for example, OAuth handles authorization and SAML handles authentication. At the same time, you could use both to grant access (via SAML) and allow access to a protected resource (via OAuth).
You could also get rid of both of these tools. For example, some websites do not require authentication or authorization.
However, in order to function properly, most businesses that use digital systems require some form of authentication and authorization system. Users must be able to sign in and navigate the company’s systems as part of their daily activities.
Courses you may like
Conclusion
When compared, both SAML and OAuth are mutually beneficial. You can use both protocols concurrently by using SAML to provide application access and OAuth to grant access to a protected resource. With either protocol or a combination of the two, you can use an identity provider or a single sign-on (SSO) service.
Have more questions to ask, feel free to reach out to us on our Cyber Security Community!
The post SAML vs. OAuth: Key Differences Between SAML & OAuth appeared first on Intellipaat Blog.
Blog: Intellipaat - Blog
Leave a Comment
You must be logged in to post a comment.