Kali Linux Tutorial – A Complete Beginners Guide
Kali Linux is an open-source operating system that is available almost everywhere around us. It’s one of the top 5 most popular OS that can be installed on laptops, computers, servers, micro-computers like Raspberry Pi, Android devices, and more.
Linux is used by many companies like IBM, Oracle, Redhat, Google, Amazon, Facebook, and Samsung as it’s the most secure and highly customizable. This means you can easily deploy it on various platforms and manage them efficiently.
This Kali Linux tutorial for beginners covers the basic concepts of Linux operating systems, how to use Kali linux, and the best Kali Linux tools list is used to perform penetration testing, system scanning, and other operations related to cybersecurity. We will also discuss some basic Kali Linux commands that you should be aware of.
- A brief history of Kali Linux
- What is Kali Linux?
- Who uses Kali Linux?
- Prerequisites
- Methods of Installing Kali Linux
- How to Install Kali Linux in VirtualBox
- Basic commands in Kali Linux
- Important Tools available in Kali Linux
- Conclusion
A Brief History of Kali Linux
Invented by Mati Aharoni and Devon Kearns, Kali Linux was released in March 2013 with the base OS Debian Wheezy. However, the story dates back to 2004 when a project named Whoppix, a live penetration testing CD stood upon Knoppix.
Followed by that, different versions of the OS were released while changing its name from Whoppix to WHAX v3, Backtrack v1, BackTrack Pwnsauce, and BackTrack Revolution with the base OS changed to Ubuntu.
Finally, with enough experience and knowledge gained in the journey, Debian stable was used as the engine and Kali Linux was released in the year 2013.
New versions of Linux with additional features were released until Kali Linux became a rolling OS and moved to Debian testing in January 2016.
Since then, developers and Cyber Security professionals are continuously adding new features to the OS, making it more advanced.
Check out the video on Kali Linux for beginners:
What is Kali Linux?
Also known as BackTrack Linux, it’s a Debian-based security distribution in Linux especially designed to perform ethical hacking operations such as penetration testing, computer forensics, advanced scanning, reverse engineering, and security auditing. It features hundreds of pre-installed tools that make it the best choice for ethical hackers and tech enthusiasts who want to perform security testing.
Linux is a multi-platform solution for both cybersecurity professionals and tech enthusiasts that provide all the necessary tools required to automate the tasks that would otherwise be very difficult to perform manually.
For example, while performing penetration testing or hacking, you might have to apply different combinations with thousands of values to penetrate the system. These tasks cannot be performed manually, instead, you require some tools to automate the tasks. Such tools not only save your time and effort but also produce the desired results by collecting accurate results.
There are two major components of Kali Linux:
- Kernel: Kernel is the core of an operating system that manages all the operations related to the hardware. It acts as a communication bridge between hardware and the user who wants to utilize the CPU and I/O devices from specific tasks.
- Shell: Shell on the other hand is an environment or interface that executes various programs based on the inputs provided by the user who wants to utilize the operating system services.
Check out the Linux interview questions if you’re preparing for a job interview or just want to learn more about it.
Who Uses Kali Linux?
Following are the professionals who utilize Kali Linux to perform various operations and describe the best use of Kali Linux:
- Network Administrators: Network administrators use Linux to detect and eradicate rogue access points, audit their network, maintain security. And simulate attacks on their network to find potential vulnerabilities.
- Security Administrators: These professionals are responsible for protecting valuable information and institutional data from unauthorized visitors. A security administrator uses Linux tools for testing the environment and discovers vulnerabilities that might pose a threat to the data in the future.
- Network Architect: They use Linux to find the hidden flaws in the architecture and design a secure network environment. Also, they use it to test the environment and see if there is any misconfiguration that has been overlooked in the network infrastructure.
- Pen Testers: Pentesters are the cybersecurity experts whom an organization hires to review their infrastructure and find the vulnerabilities or flaws within the network. A Pentester uses Linux to perform penetration testing, and audit the environment for which he is hired to review.
- Forensic Engineer: Forensic engineers leverage Linux’s ‘forensic mode’ to discover the missing data and recover it safely back to the system. They also design data backup strategies for the organization so that the data can be safely recovered in case a cyberattack happens.
- CISO: The chief information security officers utilize Kali Linux resources to audit the environment both internally and externally to discover rouge configurations and applications that have been released in the system and might compromise it.
- Black Hat Hackers: These are the bad guys you see in the movies trying to hack into a facility or breaking the government security and control over the infrastructure. They generally use Kali Linux to discover the vulnerabilities and infiltrate them into the system. Linux features various applications for social engineering that can be used to hack an individual or entire organization.
- White Hat Hackers: Opposite to black hat hackers, these are the good guys using the same tools and expertise to discover any vulnerabilities and prevent or stop the attack in the early stages.
- Computer Enthusiasts: It’s a generic term given for the people like you and me, who’s interested in hacking, penetration testing, and learning new technologies. Computer enthusiasts or hobbyists use Linux to learn more about networking, cybersecurity, vulnerabilities, operating systems, and information security.
Now that you’ve understood what Kali Linux is, and for what it’s used by people from different professions, let’s install the operating system and learn the Kali Linux basic commands.
Prerequisites
Anyone with the knowledge of computer fundamentals can start learning Kali Linux. For installation, your system must fulfill the following requirements:
- Minimum 2GB of RAM(the more the better)
- 20GB free disk space(32GB recommended)
- A dual-core or more CPU
- A working system with Windows 7 or above (this is when you’re installing Linux on a VirtualBox or Vmware).
Career Transition
Methods of Installing Kali Linux
There are mainly four methods to install or how to use the Kali Linux operating system on your device:
- Directly on a Laptop/PC: If you’re already familiar with the operating system, installing Linux on your spare PC or laptop will be the best way. It will also help you perform access point testing and other operations. You can easily download the ISO image from the Kali Linux website and install it.
- Through Virtualization: Virtualization refers to the process of simulating a virtual hardware system that provides the ability to run multiple operating systems or applications on a single computer/server. This enables you to utilize the available resources more efficiently.
Now, Linux provides pre-configured OS images that support most known virtual machines like Hyper-V, Oracle, Citrix, VMware, VirtualBox, etc. Running Linux on a virtual machine is the best way of using it if you want to clear Kali Linux basics or just want to explore the Kali Linux commands.
- Dual Boot(for both Windows and Mac): Dual boot means running two operating systems on a single machine without using a third software or application like VMware or VirtualBox. You can create a boot disc in a USB flash drive and use Kali Linux as a secondary operating system. It will ask you to select one operating system whenever you power ON on your computer/laptop.
- Windows 10(App): This is the latest method for using two different operating systems on a single computer. Kali Linux can now run on Windows 10 as an application through the command-line interface. However, the application is still in beta mode and is best for beginners.
Now, let’s move on to the next part and install Kali Linux using VirtualBox. The process of how to install Kali Linux on VMware is almost the same as VirtualBox. So, we’ll not be showing the process for both.
Take our Ethical Hacking Course to learn how to protect your networks, test different systems, and start a career as a White hat hacker.
How to Install Kali Linux in VirtualBox
Below is the guide to install and learn Kali Linux step-by-step using a VirtualBox:
- Go to the official VirtualBox website and click on the Download VirtualBox button.
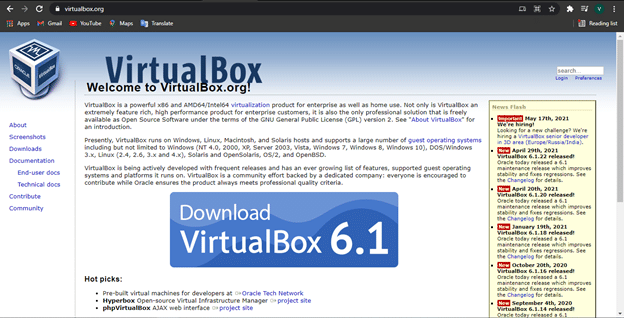
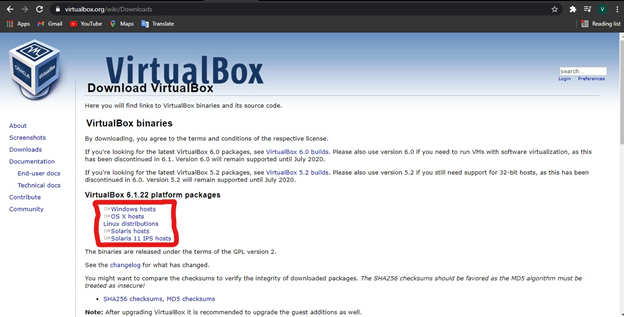
- Download the VirtualBox setup file from the resulting webpage based on your operating system.
- Open the setup file, the steps, and click on the Install button. The software will be installed on your computer and a desktop icon will be created.
- Now, the best thing about this method is that everything is freely available. You just have to download and install the software on your computer without getting any license or agreement.
- Go to the Linux website and click on the download button. Scroll down the resulting webpage to the section mentioned below.

- Select your system type(32 bit/64 bit) and download the customized image of Kali Linux for your VirtualBox.
- Now, open the VirtualBox application and click on the Import icon.
- Browse the location of the Linux image you’ve downloaded and open it.
- You will see all the settings of your Kali Linux such as the name, RAM, CPU, storage controller, and the base folder. So, click on Import and then Agree to accept the software agreements.
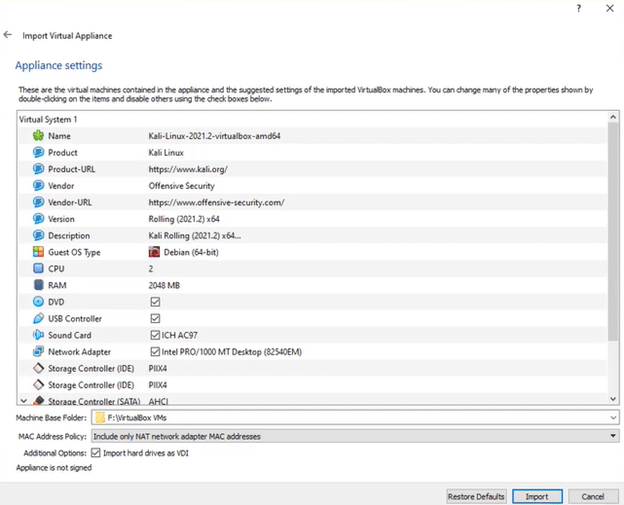
- The VirtualBox will start importing Kali Linux on your virtual machine. The process may take a few minutes. A screen like this will appear after the image has been imported successfully.
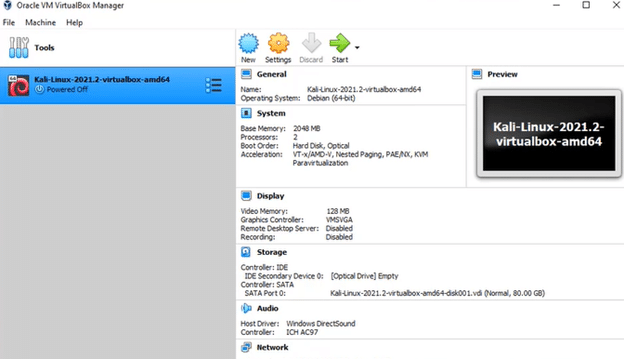
- Now, click on Settings and change the number of resources you want your Kali Linux virtual machine to use. For example, you can change the Base Memory size, the number of processors, display, audio, and other resources.
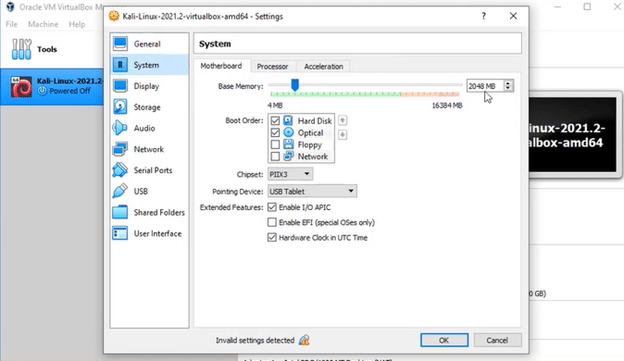
- Also, disable the USB controller as it will give you an error when starting the operating system.
- After all the settings are done, click on the Start button.
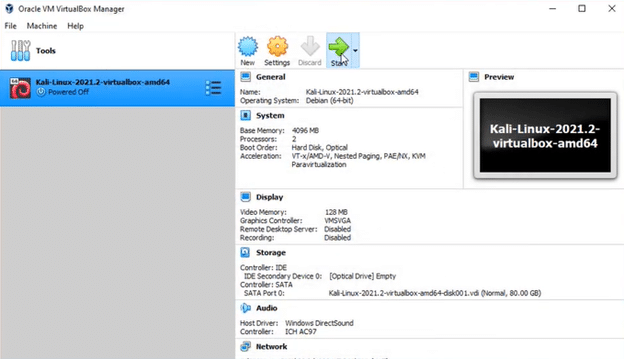
- Enter ‘kali’ in both username and password fields and click on the Login button.

- A few seconds later the operating systems will be started and you’ll see the HomeScreen of Kali Linux.
Basic Commands in Kali Linux
Before you start working on advanced tools and frameworks, we recommend you first get familiar with some Linux basic commands. Following are the basic commands in Kali Linux that makes your work much easier:
- Date command
The date command is used to display and often set the date and time of your system. However, you should have the administrator right to change the date and time.
Syntax:
$ date
Output:
Wed Jul 7 15:15:30 UTC 2021
- Cal command
The Cal command in Linux is used to display the calendar. For an advanced version of the calendar, you need to add the ‘ncal’ package using the following command:
sudo apt install ncal
Syntax:
cal
Output:
July 2021
Su Mo Tu We Th Fr Sa
1 2 3
4 5 6 7 8 9 10
11 12 13 14 15 16 17
18 19 20 21 22 23 24
25 26 27 28 29 30 31
- pwd command
The print Working Directory or pwd command prints the name of the working directory.
Syntax:
pwd
Output:
/home/cg/root/7719309
- ls command
The ls command is one of the most useful commands in Linux that displays all the content of the directories and files. It will also show you the content that would otherwise be hidden. Remember, the command has ‘L’ not ‘I’. Also, the output will be different for different systems.
Syntax:
ls -al
Output:
drwx------ 1 root root 14 Jul 7 15:15 . drwxr-xr-x 1 root root 172 Jul 7 15:15 .. drwxr-x--- 1 root root 6 Jul 7 15:15 .config
- cd command
The command allows you to change the directory or go back from the current directory.
Syntax:
cd root/Desktop
cd..
The above command will not have any output, rather your terminal will simply jump on or come out of a particular directory.
- mkdir command
This command is used to create a new directory from the command line in a specific location.
Syntax:
mkdir /root/Desktop/yeahhub
Again, there is no such output on the terminal, however, you can check the result by opening the directory.
Although these commands are very useful while using and working on different files through the terminal, there are many more Kali Linux basic commands like cat, cp, mv, rm, uname, uptime, users, less, more, sort, vi, free, etc. You can check what operations these commands are for by simply typing in the terminal.
Have a look at our blog on Ethical Hacking tutorial to learn more about this domain!
Now moving ahead in this Kali Linux tutorial, let’s go through some of the important tools that Linux features for penetration testing and other purposes.
Courses you may like
Important Tools Available in Kali Linux
Following are some of the important tools that Kali Linux provides to perform penetration testing, access points, and hacking:
Nmap
The first step in penetration testing or hacking is gathering as much information as possible about your target. This includes information about routers, connected devices, null access points, networks, and firewalls. Also known as digital reconnaissance, it helps you find the vulnerabilities in the system while keeping your identity hidden.
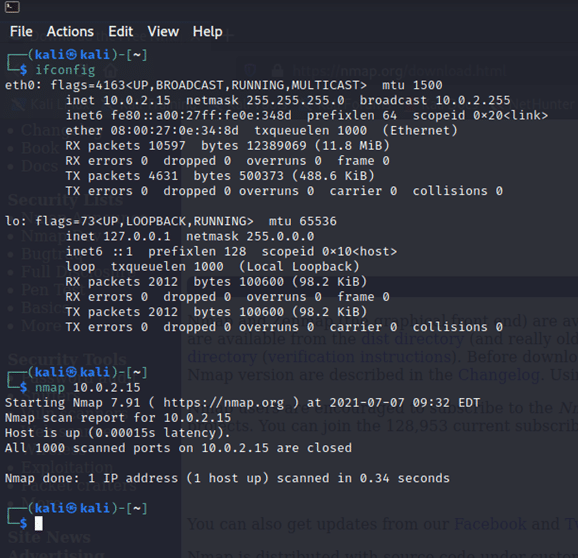
The best tool for digital reconnaissance in Kali Linux is Nmap. It’s an open-source network scanner that can perform all types of scans to help the user find ports, fingerprint the network, and discover hosts on the network. Nmap gives you the result by sending the packets to the host and analyzing them. Follow the steps below to perform the reconnaissance and scan open ports:
- Open the command prompt and type in:
Sud apt-get install nmap
- After the installation, type ifconfig on the command prompt. This will show all the hosts connected to your device. Then type:
Nmap [hostname or IP address] This command will display all the details captured by the host discovery.
Metasploit
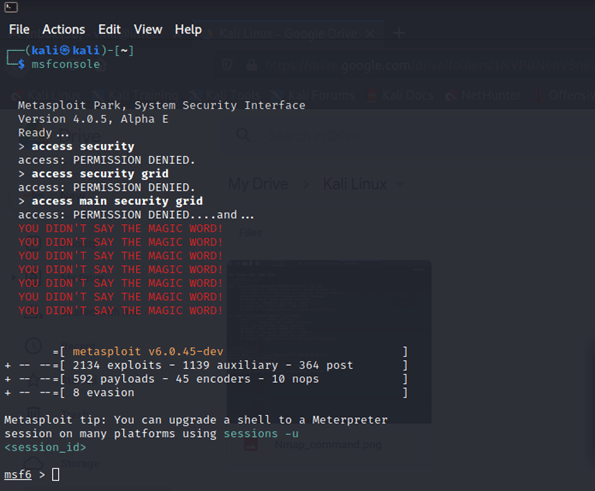
Metasploit is a penetration testing framework that comes pre-installed with Kali Linux and is an open-source tool. It’s mainly used for port forwarding and exploiting any vulnerabilities in a local network.
It also comes with a GUI package named ‘armitage’ which makes it more feasible and convenient to use. To use Metasploit, you just have to type ‘msfconsole’ in the command prompt and the Metasploit framework will be activated.
Check out our Cyber security courses and start your career in this domain!
Netcat
Netcat is yet another open-source tool that comes pre-installed in Kali Linux. This networking tool is used for network debugging, port scanning, port, listening, port redirection, and network daemon testing. It is sometimes also called the master of all networking tools as it can do operations related to UNIX domain sockets, TCP, UP, remote connections, and much more.
You can install/update Netcat through the command prompt in case your version is an older one:
sudo apt install netcat
To use Netcat, type in ‘netcat’ or ‘nc’ in the command line and hit enter. You can type these two different commands to do port listening:
nc -1 -p 1234
Terminal 1 for listening
nc 127.0.0.1 1234
Terminal 2 for requesting. The host is by default the localhost and 1234 is the port number. Terminal 2 will start listening to terminal 1 and whatever is written in terminal 1, will reflect terminal 2. You can also run Netcat online by adding the extension to the Chrome browser.
John the Ripper
John the Ripper is yet another tool that is famous for cracking passwords using brute force, custom wordlist, dictionary, and other attacks. It can even crack the passwords and hashes for the compressed, zipped, and licked files on a computer.
Just like the above tools, John the Ripper comes pre-installed with Kali Linux and is super easy to use. To get started, type in ‘john’ in the terminal and John will show you the magic.
This isn’t it, there are hundreds of tools in Kali Linux that can be used to perform advanced scanning, penetration testing, spoofing, password cracking, and even hacking a device.
Some of the famous tools readily used by hackers and cybersecurity experts include Burp suite, aircrack-ng, SQLmap, Autopsy, Wireshark, Sseveralocial Engineering Toolkit(SET), Lynis, WPScan, Hydra, maltego, Nessus, Snort, Nikto, King Phisher, Yersinia, and more.

Conclusion
Kali Linux is one of the best and most popular operating systems used for software testing, penetration, and hacking. It’s the number one choice of various IT professionals, cybersecurity experts, and white hat hackers when it comes to testing, evaluating, and auditing software or networks.
The interface and utilities Kali Linux provides are very helpful for the newbies to easily understand the concepts like port detection, networking, spoofing, malware detection, and learn how to secure a technological infrastructure or a network.
Hope this Kali Linux tutorial helped you in clearing your basics, if you have any doubts, ask them out in our Cyber Security community!
The post Kali Linux Tutorial – A Complete Beginners Guide appeared first on Intellipaat Blog.
Blog: Intellipaat - Blog
Leave a Comment
You must be logged in to post a comment.













