Is your greatest cyber vulnerability a lack of cybersecurity talent?
Blog: Capgemini CTO Blog
Eight principles to bridge the talent gap

Organizations will pay a high price to understand their cyber vulnerabilities. In early 2018, Google paid $105,000 to a researcher who unearthed a security flaw in its Pixel smartphones. This is the highest-ever reward made as part of its Android Security Rewards program. Statistics for 2017 from Bugcrowd show that organizations paid, on average, $1,776 to researchers who identified critical vulnerabilities in their systems.
These reward programs underscore the importance of strong and secure systems in a world where the global average cost of a data breach in 2017 is estimated at $3 million+. There are many ways an organization can try to avoid these costs by putting in place security infrastructure, governance, and policies. However, there is one element that underpins all these approaches—cybersecurity talent.
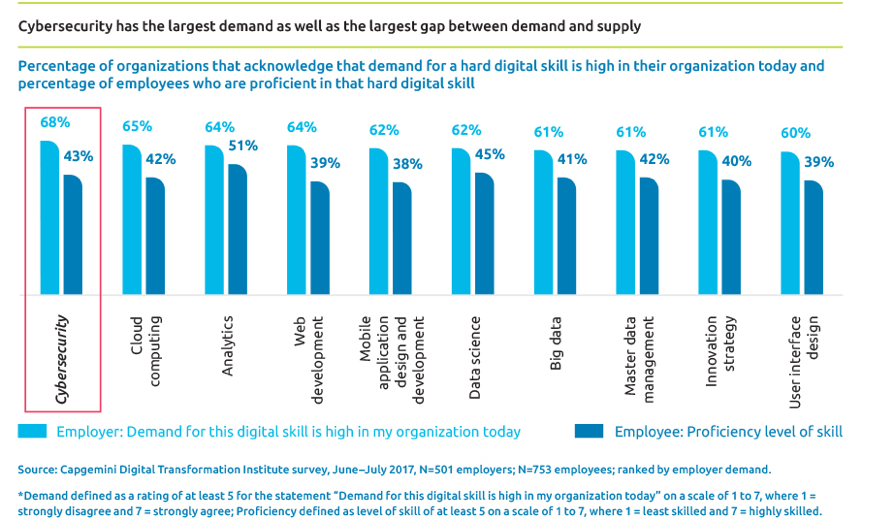
Results from our research with 1,200+ senior executives and employees show that:
- Cybersecurity tops the list of technical skills in high demand
- Cybersecurity has the most pronounced gap between demand and supply: 68% of organizations say they need this skillset, while only 43% of employees say they are proficient in it (see Figure 1).
- Today, 68% of organizations say that their demand for cybersecurity talent is high, and this is expected to rise to 72% in the next two to three years. Moreover, the war for that talent is an intense one. Traditional organizations have to compete for talent with tech firms such as Google and Facebook, who present an attractive proposition for cybersecurity professionals.
Figure 1: There is a 25-percentage point gap between demand and supply for cybersecurity.
 The importance of learning and career development
The importance of learning and career development
To find and retain talent, organizations need to understand what motivates the people they are pursuing, with learning and career development key factors that cybersecurity talent prize:
- Four in five cybersecurity talent like the flexibility to choose their own training calendar and programs.
- From a social media analysis of 8,000+ cybersecurity employees, Learning & Development featured in the top five factors that influence these employees to stay with a company. This same group pointed to “lack of career progression” as the number-one negative factor behind dissatisfaction with their organization.
- It is not just Gen X and Gen Y cybersecurity talent who are keen on learning. More than eight in ten Gen X talent say they are willing to spend time beyond office hours for learning.
Eight principles for attracting and retaining talent
From our research—as well as interviews we conducted with cybersecurity academics, recruitment consultants, and cybersecurity associations like ISACA—we have identified eight recommendations across the two key areas of acquisition and retention.
Acquisition:
1. Think outside the box to find cybersecurity talent
Organizations like Auticon in the UK are employing autistic people as they are analytical and detail-oriented, skills that help in the security field.
2. Hunt in areas where cybersecurity talent spend their time
To engage the millennial audience during recruitment, organizations need to look at career apps, such as Debut, that bring students and large organizations together. Gamification also can create interest and Unilever has seen impressive results from its neuroscience-based hiring.
3. Create a compelling story around the current leadership and team
Our research shows that employees want digitally talented peers. Anchor-hiring (hiring senior executives who can attract more talent) can bring fresh talent into the organization.
4. Turn your gaze inwards, as your next cybersecurity talent might already be working in your company
Organizations should leverage the internal employee base—creating an inventory of existing skillsets and promoting cybersecurity communities.
Retention:
5. Incentivize employees to upgrade their cybersecurity quotient
Organizations need to focus on reskilling and upskilling their employees. AT&T is leading the way with a massive initiative of retraining 100,000 of its workforce with various skills.
6. Promote gender inclusion by changing the perception of the cybersecurity field
Women are under-represented in cybersecurity and this lack of women goes back to STEM program enrollment and even further. Organizations should take up inclusion initiatives targeting female students in college and high school.
7. Ensure Gen Y and Gen Z cybersecurity talent can visualize their career path
A continuous feedback system for employees ensures that people have clarity over their career progression.
8. Automate mundane tasks to free up time to focus on value-adding activities
Automating the routine aspects of security jobs will help free up the employees’ time, allowing them to focus on more critical areas.
These eight principles can help organizations bridge the cybersecurity talent gap. To find out more, access our full research report “Cybersecurity talent—the big gap in cyber protection.”
Notice: JavaScript is required for this content.
Leave a Comment
You must be logged in to post a comment.







