Difference Between Risk, Threat, and Vulnerability
Cyber security, network management, risk assessment, vulnerability management, etc., all revolve around risks, threats, and vulnerabilities. Even though organizations spend a lot of money on their cyber security systems, a majority of people still do not understand the clear meaning of these terms.
In this blog, we will study the following :
Asset
To understand the difference among risk, threat, and vulnerability, it is first important to learn what is an asset in the world of cyber security. Asset includes people, property, and information. People includes employees and other stakeholders of an organization, property means both tangible and intangible items carrying some value, and information means any kind of useful data such as accounts, records, etc. Every now and then, these assets are exposed to a threat, risk, and vulnerability. We will now dig further into the individual explanations and understand the difference between threat, vulnerability, and risk.
What is a Threat?
Threat is usually referred to as something against which assets are being protected. It is the identified possibility that can be accidental or intentional and damage or permanently destroy an asset. All kinds of social engineering attacks, ransomware, worms, and viruses are considered as possible threats. The intentions behind these attacks can be financial or political. Refer to our detailed article to know more about Cyber Security Threats.
Threats constantly try to exploit the gaps in network security systems, and these threats are an increasing cause of concern for cyber security professionals. Even though prompt real-time threat intelligence reduces the chances of damage from threats, attackers still continue to exploit vulnerabilities in security systems. In May 2017, the WannaCry ransomware flooded millions of Windows systems resulting in a damage of approximately four billion dollars. The attackers exploited a vulnerability in the security system of the Windows systems by Microsoft. Hence, improving the security and IT response time is the only way to identify possible threats and mitigate the damage caused by the attacks.
What is Vulnerability?
Vulnerability is a weak point, flaw, error, or gap in the security environment of an asset. The weakness is exploited by the possible threat to force its way into getting unauthorized access to the system. In the 2017 WannaCry attack, the vulnerability in the Windows systems was exploited by the ransomware attackers to demand ransom from the users in return for the files. Organizations generally have millions of vulnerabilities and hence patching them all is not possible and feasible. With a limited cyber security workforce, only a finite number of vulnerabilities are rectified and patched. The remaining weaknesses leave the systems vulnerable to threats.
If you have not discovered a vulnerability, it might be possible that you may be the next target of an attack. To be precise, it is highly difficult to discover all vulnerabilities in a system. However, not all of them are likely to be exploited. As per Harvard, the risk of a vulnerability being exploited is considered to be low, but the overall cost to fix it later can be very high. Hence, the cyber security structure of an organization should be built considering risk prioritization.
Learn more about Vulnerability from our Cyber Security training course and protect yourself from various cyber-attacks.
What is Risk?
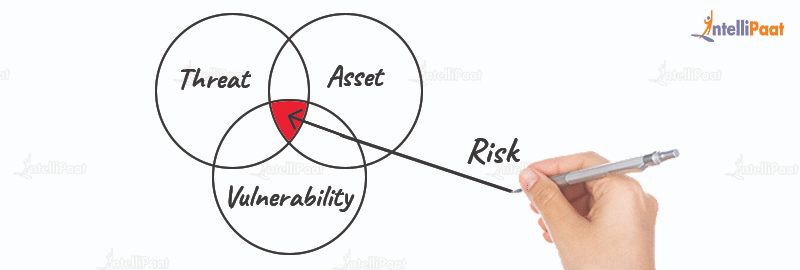
Risk is the probability of loss of asset, exposure to threat, and potential damage from a cyberattack. It is basically the meeting point of threat and vulnerability. The risk of losing intellectual property and sensitive information has been increasing recently. Therefore, organizations are ensuring the best security measures for data protection. Risk management is gaining a lot of importance among cyber security professionals. It includes examining the potential or probability of negative events and the assessment of the damage that might be caused due to a breach or attack.
Risk= Threat * Vulnerability
Some of the key points to be considered while designing risk management strategies are:
1- Risk Prioritization
It is important for organizations to address breaches and risks as per priority and relevance. Many vulnerabilities in the systems might not be prone to exploitations and hence do not pose a higher risk. So, vulnerabilities should be patched as per the risk levels.
2- Risk Tolerance levels
It is recommended for organizations to know and estimate their risk tolerance levels. The risk-bearing capacity should be checked on a regular basis while implementing a risk management framework.
3- Knowledge of Vulnerability
Threats will exist but if there are no vulnerabilities, there are limited or zero chances of risk. Hence, knowing about common vulnerabilities and regular tracking of those is critical to identifying potential risks to assets.
The following formula is used to determine risk while conducting risk analysis :
Asset + Threat + Vulnerability = Risk
Enroll in our Ethical Hacking course online to master various ethical hacking concepts.
Conclusion
So far we talked about the difference in the meanings of risk, threat, and vulnerability. For further clarity, let us take the example of national defense. A country is always under threat, such as a terrorist attack, etc. The gaps in the national security system are the vulnerability and the potential damage to the property, loss of lives of the citizens, etc., is the risk.
Similarly, it is equally important to understand the meaning of these terms in the domain of cyber security. Uncovering vulnerabilities is as important as assessing the risk. Knowing about these terms helps cyber security professionals to effectively utilize vulnerability and risk management tools and techniques. Even though there is more to security, risk, and vulnerability management, yet understanding the difference between risk, threat, and vulnerability is a good start to reduce risk and mitigate the impact of cyberattacks.
The post Difference Between Risk, Threat, and Vulnerability appeared first on Intellipaat Blog.
Blog: Intellipaat - Blog
Leave a Comment
You must be logged in to post a comment.








