Difference between Phishing and Pharming
We will first discuss what is phishing and pharming with examples and then, go on to explore the differences between the two. Later, we will also discuss ways that one can prevent such cyber thefts from happening
- What Is Pharming?
- What is Phishing?
- Examples of Phishing and Pharming
- Phishing and Pharming Techniques
- What is the difference between phishing and pharming?
- How to avoid phishing and pharming?
- Conclusion
Cybercriminals are constantly evolving and improving their skills to compete with the advanced and updated security systems as well as the latest technology and platforms. While both phishing and pharming work differently, both trick users into keying in their sensitive information. To know more about phishing and pharming techniques, continue to read below.
Learn more about the cyber security threats that are prevalent today.
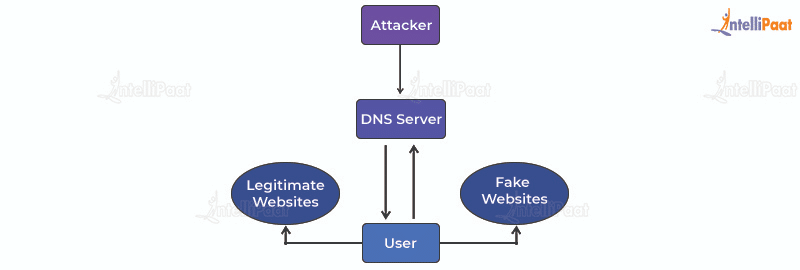
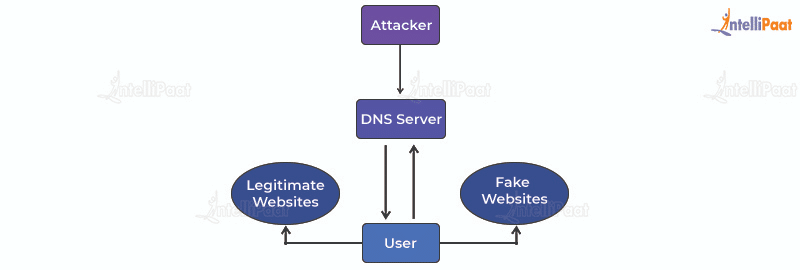
What is Pharming?
Pharming is an advanced technique and a practice of scamming that is used to steal users’ credentials by attempting to make users enter the website. Simply put, it misdirects users to a fake website that appears to be safe and tricks them into giving out their personal information, which can be later exploited.
In pharming, a malicious code is installed on a victim’s computer system or the server misdirects the victim to a fraud website without their knowledge. These fraudulent websites look like legitimate ones.
The main objective of pharming is to steal personal and sensitive information like login details, personal data, and financial information. Sometimes, even clicking an authentic link can lead a user to the pharming site if the domain name or the DNS of the website has been hijacked by the hacker.
Pharming attacks are dangerous and a hidden threat because the user is never aware if a website is hijacked before handing over their personal information.
Users who access the website are asked to fill out their username, password, and other credentials on the pop-up window. This is how pharming operates and successfully gains access to sensitive information.
What is Phishing?
Phishing attacks are a form of social engineering that con users to reveal their confidential and personal information. In this form of attack, hackers send a spoofed email that looks like it’s coming from a legitimate source name to the victim. The victims are then tricked into clicking on the malicious attachment or link in the email. This allows the hackers to steal personal information from the user.
In most cases, phishing utilizes software or security vulnerabilities to install malicious software in the device of the target user.
A phishing attack is not necessarily restricted to emails. It can also occur via text messages, also known as smishing and voice messages aka vishing to deceive their targets and gain access to information by acting as a legitimate source.
Phishing attacks are very common and have been accounted for a large number of data breaches in the past.
Examples of Phishing and Pharming
Some of the examples below illustrate common phishing scam attempts:
- A banking fraud where the hackers act as bank employees to get access to someone’s bank information.
- A spoofed email ostensibly from a legitimate-looking source, which is mass-distributed to as many users as possible.
- An email that claims that the password is about to expire with additional instructions that lead the users to go to a legitimate-looking link to renew their password within 24 hours.
Some of the examples of pharming are:
- When a user is led to a fraudulent site instead, they open their browser and enter the web address of a bank for the purpose of online banking.
- When a bank is affected because the DNS of a user’s routers are changed and they are not aware.
Phishing and Pharming Techniques
Let’s take a brief look at how phishing and pharming are carried out with different techniques.
Phishing Attack
There are various types of phishing attacks that take place. These are:
- Spear Phishing – This type of phishing attack targets organizations or an individual for gaining unauthorized access. Spear phishing is not initiated by any random hacker, but by those who want information that will lead to financial gain or other critical pieces of information. Because spear phishing occurs from a trusted source, this type of attack is much more successful in operating an online attack on users.
- Clone Phishing – Clone phishing involves copying email messages that are usually sent from a trusted source. The hackers, in this case, alter the information on the email by inserting a link within the content that will redirect the user to a malicious or fake website. The attack spreads to anyone who is on the contact list of the victim who clicked on the attachment.
- Catphishing – This social engineering attack toys with the emotions of the target and exploits them for financial gain and information. These types of attacks are initiated through dating sites
- Voice Phishing – Voice phishing or vishing makes use of modern caller id spoofing in order to trick the victim into thinking that the call is from a legitimate source like a call from a bank that the user has an account with. To make it difficult for legal authorities to trace or monitor them, they use IVR. Vishing can be used to steal credit card information or other confidential information of a user and can cause great damage to the victim.
- SMS Phishing – SMS phishing is used to make the target victim reveal their account information. This type of attack uses text messages to steal the personal information of someone by attempting to redirect them to a fake website that looks like a legitimate website.
As smartphones and devices are widely used, cybercriminals see this as an opportunity to perform vishing as they don’t have to put in the effort to break firewalls and access the system to steal information.
Some of the symptoms of phishing are:
- The user may receive a request to share personal details like bank login credentials and other confidential information.
- If a user is redirected to a website when they click on the link that was received via email
- If a user is redirected to a website and receives a request for information related to credit cards or banking details.
Enroll in a Cyber Security course to become a professional in this domain.
Pharming Attack
Pharming can occur in two ways—One is by exploiting a vulnerability in the DNS server software and the second way is by changing the hosts file on a target’s computer. Hackers redirect their targets to a fake version of a website and con them to steal login credentials.
Let’s take a look at the working of a pharming attack:
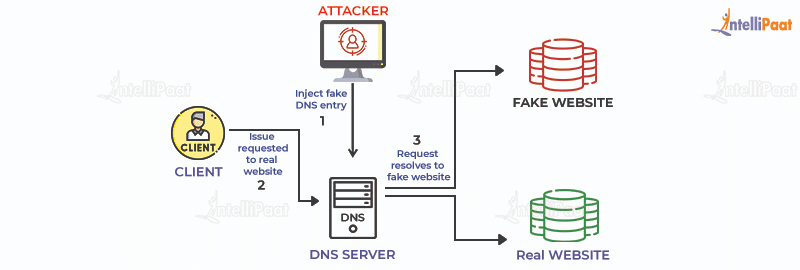
Symptoms of pharming attacks:
- Whenever a user visits a fraudulent website, malware gets installed on the computer and it corrupts the information
- Whenever a user visits any URL using any browser, the browser contacts the DNS server and requests the IP address for the desired domain thus changing the DNS server
If pharming attack happens on-
1. Client-Side
- Attack is targeted on the local hosts’ file
- Attack is targeted on the home router
- Attack is targeted on the browser proxy configuration
2. Server-Side
- Poisoning of the cache DNS server occurs to insert fraud entries
- There are transparencies on the proxy server between the user and the internet
- Manipulating resolution entries for a website by exploiting the intruder
Learn the difference between risk, threat, and vulnerability.
What is the difference between phishing and pharming?
Now that we have covered how phishing and pharming work, let us explore the difference between phishing and pharming. While phishing and pharming are both kinds of cyber-attacks there is some difference between them.
To understand the differences, we need to first understand the DNS. In a pharming scam, the hackers misuse the DNS system to be used as the key weapon. While phishing is attempted using legitimate-looking websites that are actually spoofed, pharming happens at the server level of the DNS.
Unlike phishing, pharming does not make use of baits, such as fake links in order to trick users. Pharming instead involves negotiating on the DNS server and then redirecting the user to a website that is stimulated even if the user has input the correct website address. So in case, the hacker has been capable of launching a successful DNS attack, it alters the fundamental flow of the web traffic towards the target’s website.
Career Transition
Phishing uses different techniques like smishing, vishing, fax phishing, etc. Pharming uses DNS hijacking, DNS cache poisoning, DNS spoofing, etc.
Pharming is trickier to pull off than phishing because it involves manipulation at the DNS level, which is also difficult for the victims to identify.
| Parameters | Phishing | Pharming |
| Definition | The attacker tries to gain access to sensitive information of users by means of illegal electronic communication | More advanced technique to get users credentials by leading users into a fraud website |
| Objective | To scam people one at a time using email or instant messaging | To redirect traffic from one website to an identical-looking one to steal information |
| Category | E-mail fraud | Similar in nature to e-mail phishing |
| Process | The attacker tricks the victims into giving out personal information by email, fax, or message | Personal and private information is obtained through domain spoofing, DNS cache poisoning, DNS hijacking, etc. |
| Difficulty Level and Detection | Relatively easier to initiate and identify | More difficult to accomplish and identify |
| Technique | A fraudulent email contains a link to a website seeking personal details from users | The DNS server is poisoned and users are redirected to a different website |
| Medium | Email, fax, and instant messaging | Local hosts file, websites, home router, DNS server, etc. |
How to avoid phishing and pharming?
Regardless of what the difference may be between phishing and pharming, they are serious threats to cyber security. To stay secure from these attacks it is important to check the HTTPS in the URLs and the emails in case they are suspicious.
It is also important that one have cyber security awareness so they are aware of potential threats. Avoiding clicking on suspicious links will also prevent one from being exposed to cybercrimes.
Here is how you can protect yourself from phishing and pharming attacks:
Preventive measures against phishing attacks:
- Do not open suspicious email attachments
- Avoid opening suspicious links
- Do not give out sensitive information like personal or banking information via email or messages
- Always use an antivirus
Preventive measures against pharming attacks:
- Always use a trusted and verified Internet Service Provider (ISP)
- Use a VPN service that has reputable DNS servers
- Always enable two-factor authentication on sites when you have the option to do so
- Avoid suspicious websites
- Make sure to change the default password on your consumer-grade routers and wireless access points
- Always be careful when opening links or attachments from unknown or suspicious sources
- Using security software is crucial
- Make sure that your web connections (the web address should have HTTPS) are secure-
Learn from our Top Cyber security interview questions and crack any interview.
Conclusion
We hope this blog help to make the pharming vs phishing differences clear. Phishing tops the list of social engineering art that lures the victims to submit their sensitive information on the phished website that they get misdirected to, whereas, pharming is more complex and difficult to pull off and cannot be easily detected. If you’re wondering – “How is pharming similar to phishing?” Both of these forms of data theft lead to devastating consequences and cause significant damage.
The post Difference between Phishing and Pharming appeared first on Intellipaat Blog.
Blog: Intellipaat - Blog
Leave a Comment
You must be logged in to post a comment.