Difference Between Active And Passive Attacks
This blog contains:
- What is an Active Attack?
- What is a Passive Attack?
- Difference between Active and Passive Attacks
- Types of Active and Passive Attacks
- Examples of Active and Passive Attacks
- Conclusion
Check out this latest cyber security tutorial and training for free
What is an Active attack?
Attacks in which hackers strive to manipulate or alter the content of communications or information are known as active attacks.
These cyberattacks, against cyber security, jeopardize the system’s integrity and authenticity. These threats can damage systems and tamper information.
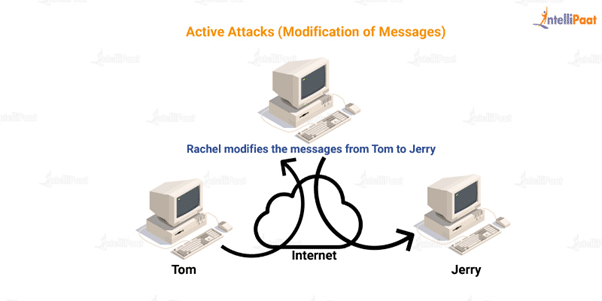
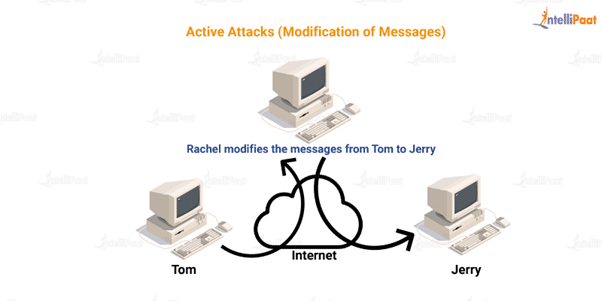
Let me explain it to you with an example.
Imagine Tom and Jerry are friends. Tom is sending a letter to Jerry. So, before the letter reaches Jerry, Rachel takes the letter and alters the message. Now, what Jerry receives is not the information sent by Tom.
Here, the information has been altered by a third party. This is a potential threat because what if the information sent by Tom was sensitive and crucial. If Jerry is not clever enough to identify the alteration in the message, he might proceed with the modified information. This can lead to a lot of problems and is a serious threat to any organization.
So, this is the answer for what is an active attack?
Sometimes, the victims are notified about the attack. This is an advantage because once an attack is identified, it is possible to restore the data as well as the system. So, priority is given to detecting such attacks rather than preventing them.
Active attacks can be reduced by using OTP to authenticate the communication process between two entities.
It is possible to create a random session key that is only effective for one transaction. This makes it more difficult for the attacker to transfer data after the session has expired.
What is a Passive Attack?
It is the type of attack in which a third-party attackermonitors the messages between two entities and replicates the content of those messages with malicious intent.
The objective of these types of attacks is to gather sensitive and confidential data. Neither do these attacks alter the data nor do they destroy the system.
Let me simplify the process. In the prior example, Rachael altered the message between Tom and Jerry. Here, Rachel does not alter the message. Rachel simply observes the content of the message between Tom and Jerry, so that she is aware of the sensitive information that is being conveyed between Tom and Jerry.
In other words, Rachel invaded the privacy of Tom and jerry. Hope this answers the question, what is a passive attack?‘
One of the possible protective measures that can be taken to prevent these types of passive attacks is using encryption methods for sensitive information so that it remains unreadable for outsiders.
Such passive attacks can also be avoided by not using online platforms to share confidential and sensitive information.
Preparing for cyber security job interviews? Have a look at our blog on Cyber Security interview questions and excel in the hiring process.
Difference between Active and Passive Attacks
| Active Attacks | Passive Attacks | |
| Effect on info | The message is disrupted and modified | Message remains unaltered |
| Effect on system | System integrity and accessibility are harmed | Systems and resources are not disrupted |
| Importance is given to | Detection of such attacks | Prevention of such attacks |
| Impact on resource | Resource is manipulated and damaged | No impact on resource |
| How do attacks happen? | Information is gathered through passive attacks to attack the system | Sensitive and confidential information, such as passwords and private chats, is gathered |
| Difficulty | Very difficult to prohibit or prevent such attacks | Comparatively easy to prevent such attacks |
Career Transition
Types of Active and Passive Attacks
Let us take a gander at the different types of active attacks and passive attacks.
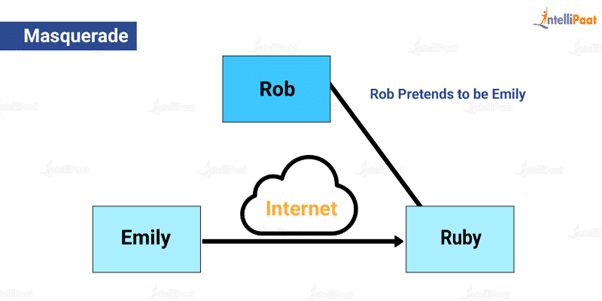
Masquerade
It is a type of attack in which one person acts or pretends like someone else and alters the system and data. This person might delete, corrupt, or alter the information. Hence, it is an active attack. A simple pictorial representation of masquerade attacks is given below.
Repudiation
This attack can be carried out by either the sender or the receiver. The sender or receiver might send or receive a particular message, but they refuse this fact later on. Let us understand it clearly with an example.
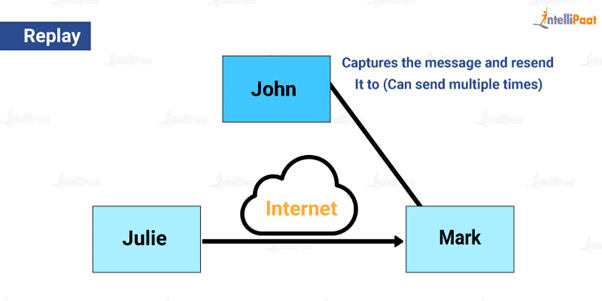
Replay
It is a type of passive attack in which an intruder observes and captures a message or content and uses the same to produce an authorized effect. Let us take an example.
Suppose Julie is a higher authority official sending a message to Mark. John captures Julie’s message or content, and sends it to Mark to convince Mark that John is the authority. Now, in this situation, Mark would interpret John as the official. This is known as replay.
Learn more about this domain from our Cyber Security training curated by industry experts.
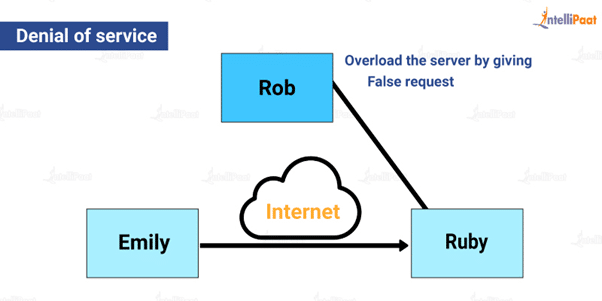
Denial of Service or Fabrication
In this type of attack, the intruder prevents all forms of communication between two entities. All communications addressed to a certain destination can be disabled by an entity. Another type of service denial is when a whole network is disrupted, either by deactivating it or by flooding it with messages to deteriorate performance.
A simple example of this kind of attack is shown in the image below. Emily is sending a message to Ruby. Rob, the cracker, overloads the server by sending false information and requests. This can impact the speed at which Emily’s message is sent to Ruby.
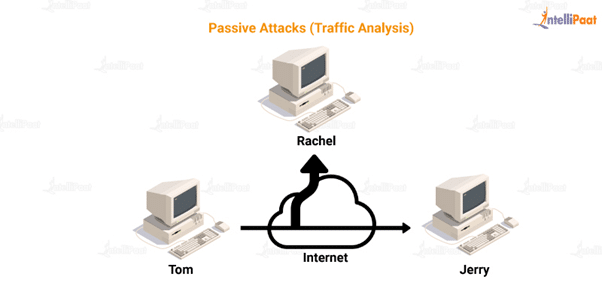
Traffic Analysis
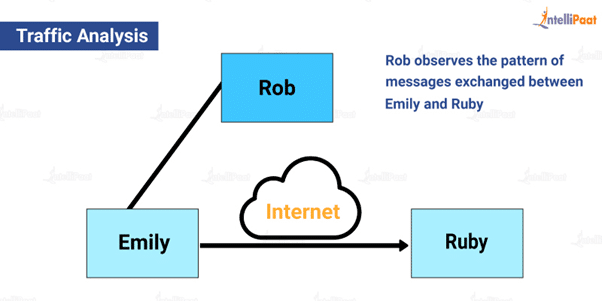
Due to the increased active attacks and passive attacks, the encryption of information has been a recent savior. When information is encrypted, an intruder cannot read the content of the messages. But, the intruder can still observe the frequency, length, and time of the messages. The intruder might exploit this information to predict what kind of conversation and communication is happening. This is known as traffic analysis.
Have a look into our Cyber Security tutorial to learn more about cyber attacks!

Examples of Active and Passive attacks
In this section, let us look at a few popular attacks in the history of cyber security.
Nasa Cyber Attack
James Jonathan, a 15-year-old, was able to hack NASA’s systems and shut them down for 21 days in 1999. During the attack, roughly 1.7 million programs and software were downloaded, costing the space behemoth around $41,000 in repairs.
Ashley Madison Data Breach
Ashley Madison, a notorious website marketed as allowing extramarital relationships, had its user data stolen by a group, called the Impact Team, in July 2015.
The group copied the personal information of the site’s users and warned that they will disclose the users’ names and personally identifiable information. More than 60 terabytes of customer information, including user information, were released by the hackers.
The ironic thing about that attack was that they disclosed the names of users that included many popular government authorities.
The 2014 Cyberattack on Yahoo
When 500 million Yahoo accounts were hacked in 2014, it was one of the largest cyberattacks of the year. Fortunately, only basic information and passwords were reportedly taken and not bank information.
Channel Nine Attack
Channel Nine, an Australian TV channel, was jolted by a cyberattack on March 28, 2021. The attack restricted the channel from airing its Sunday news bulletin and numerous other programs.
CNA Financial Cyber Attack
Surprisingly, CNA Financial, United States’ largest cyber insurance provider, was struck by a well-planned ransomware assault, compelling the enterprise to go out of operation for the next few days.
The hackers who claimed responsibility for the attack employed a malicious program called Phoenix CryptoLocker to encrypt the insurance company’s information. Unfortunately, CNA had to pay a whopping $40 million to recover possession of its protected data.
Despite CNA’s lack of an official response, the attack has undoubtedly taught the insurance company, as well as other corporations, a harsh lesson.
Enroll in our Cyber Security courses and start your career in this hot domain! Be an expert now!
LinkedIn Attack
In June 2021, data belonging to 700 million LinkedIn members was uploaded on a dark web, exposing 90 percent or more of the company’s user base. Data scraping techniques were employed by a hacker known as God User, who exploited the site’s and others’ API before disclosing a first data collection of roughly five billion users.
According to LinkedIn, no sensitive, private personal data was exposed, but the incident was an infringement of the terms and agreement.
Courses you may like
Conclusion
So, we have covered a lot of information about active attacks and passive attacks. From the examples, we can surely jump to the conclusion that such attacks are serious threats to any organization and have the potential to cause a lot of destruction.
Increased attacks demand skillful cyber security experts who can prevent such attacks and restore the system after such attacks.
Do you have any queries? Ask it out right now in our Cyber Security community.
The post Difference Between Active And Passive Attacks appeared first on Intellipaat Blog.
Blog: Intellipaat - Blog
Leave a Comment
You must be logged in to post a comment.