Safer remote access with VPN
Blog: AuraQuantic Blog
The COVID 19 pandemic has forced us to take
refuge in our homes and work remotely. As a result, we have left the security
of our corporate intranet, and now use the Internet to access our local network
and obtain the information we need to carry out our daily duties. In other
words, our data is more exposed than it has ever been before, therefore we
should consider making access more secure by means of a VPN.
What is a VPN?
A VPN (Virtual Private Network) is a
networking technology that allows you to set up a secure link to your local
network (LAN) over a public network such as the Internet.
In essence, what it does is hide our IP
address and route our Internet connections through an encrypted VPN tunnel.
Initially, local networks depended
exclusively on cable, and in most cases, we could only connect to them from a
terminal located in the office.
This is probably the most effective
solution from a data security point of view, but it is completely ineffective
in terms of production.
Soon, companies realized that they needed
to cross-reference their data between their offices in order to operate with
complete certainty and started to contract dedicated lines. Unfortunately,
these lines were very expensive and thus the Internet became the most viable
option.

Sending data over the Internet was and still
is the most logical and consistent option. The evolution of other technologies
such as WIFI, and especially technology related to mobility has transformed
communication and changed our way of life.
Today, it is not only possible to connect
to other offices, but we can also continue working on the go, from our home, or
even from our favourite cafeteria. However,
it is also true that our data has never been as exposed as it is now.
How a VPN works
With a VPN, we connect to the Internet service
through our ISP (Internet Service Provider), and from there we are directed to
our VPN server, which takes us to the requested page. This is what we call a tunnel.
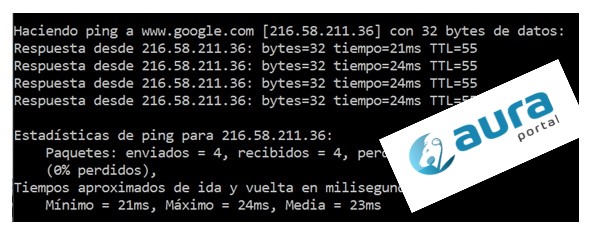
For example, if I want to access Google’s
website and I don’t use a VPN, I enter the website’s address in the browser’s
search bar and the browser contacts the router to look for the website’s IP
address in the DNS server provided by our Internet Service Provider.
Sorry to disappoint, but on the Internet
the addresses that matter are more like 216.58.211.36 than www.google.com, however using a name is not
only easier to remember, but also more
reliable as the numerical address could change for many reasons, without
changing the name of the website. If you want to try, type “ping Google.com”
into your MS-DOS console.
A DNS (Domain Name Server) is a server that converts human readable domain names into Internet Protocol (IP) addresses.
Returning to the subject, I should tell you that a router is the intermediate point between the Internet and the local network. Its main function is to request the data on the Internet and distribute among the network devices (computers, laptops, tablets, etc.). To do this, once the IP address of the requested page has been found, it will be transferred to the browser, which will in turn contact the web server that hosts the page, and finally transfer the data needed to view it.
The problem is that for communication
between devices to be possible, both the router and the browser must provide
data such as our IP address, the operating system we use, the type of device
from which we used to send the request, etc.
But wouldn’t this happen anyway if I used a VPN?
For the exchange of data to access a
website, we provide data that lets the user to know our public IP, the page we
want to visit, what operating system we use, browser, physical location, etc.
The big difference, however, is that with a
VPN, it is the VPN server that makes the request for the page. Therefore, the
data that is going to be collected will correspond to the VPN and not ours.

In addition, when we use a VPN our data is
encrypted so that not even our ISP will be able to know what we are looking
for.
We can make a comparison between data
traffic on the Internet and the money that is transported between banks. The
VPN client is the first bank, the VPN server is the second bank and the VPN
encryption is the security truck that transports the money between the
locations.
Why we need a VPN
From a company’s point of view, a VPN
connection can be used to allow employees from other offices to access the
organization’s private network, or to work remotely, minimizing the exposure of
your data.

There are many situations that put our
password at risk of being captured. All of us, without exception, have
connected to a public WIFI connection at some point. This connection can be a
decoy to connect to a hacker’s computer.
In this case, if our connection is not
encrypted, we will do the hacker’s job for him.
VPN and encryption
Encryption is not unique to VPN but in
general, whenever these connections are used, they are accompanied by an
encryption, so it is quite recommendable to use a VPN if you are going to
connect to a public WIFI access point.
The most common encryptions offered by the
different VPN providers are OpenVPN, SoftEther, IKEv2, L2TP/IPSec, PPTP and
SSTP (SSL).
Multiple authentication tools
There are already many services that offer
two-factor verification to increase the security of user account access. Some
platforms also allow you to configure the authentication mechanism and choose
whether you want to receive the access code by mail or directly on your mobile.
Integration with Active Directory
It is also very common for some VPN
solutions to use SSL cryptography and allow access via Active Directory login.
In this case, a certificate is created.
This certificate can be for individual or collective use. When access is
required, the administrator can assign a certificate to a group of people, so
if any of these users no longer need access, they can simply remove this user from
the group, without having to revoke the certificate.
The post Safer remote access with VPN appeared first on AuraQuantic.
Leave a Comment
You must be logged in to post a comment.








