Ransomware and Viruses – both pose a significant threat to your security. They can infect your system, remove files, and cost you a whole lot of money.
But, if they do the same thing, then what is the difference? What exactly are they ? Is there a solution for ransomware and viruses? This article will explore each query in detail.
Ransomware and Viruses: What’s the difference?
There is some confusion related to the terms as they are sometimes used interchangeably, but there are few important differences that can be made.
RANSOMWARE
What is ransomware?
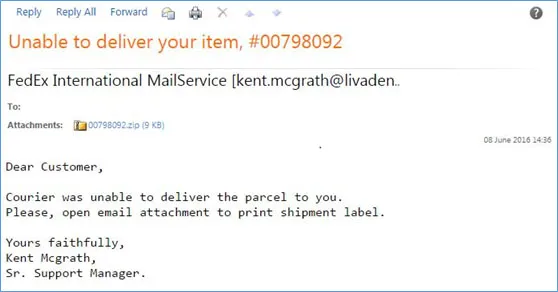
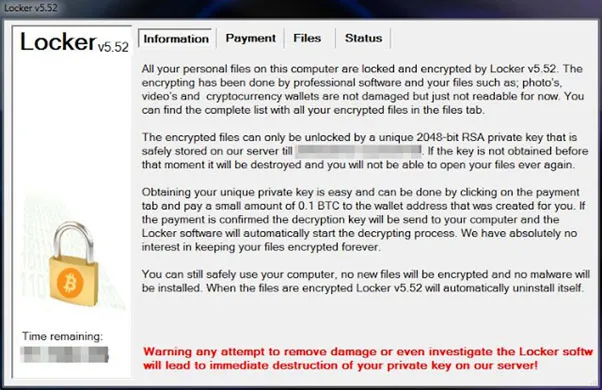
Ransomware is a kind of malicious software that can be embedded in a computer, mobile, or a cloud environment. It is designed to block you from accessing the files in your system until you pay a ransom to its creator.
Hackers can completely lock your system, disable you from accessing the files in it, or threaten to leak the sensitive information on a public platform. The ransom to unlock your device can range from hundreds to thousands of dollars. Ransomware use cryptovirology (the practice of using cryptography to design robust malicious software) to encrypt the system and make it inaccessible.
How does ransomware affect the system?
The most common manner to spread ransomware is through spam messages. You’re tricked into clicking on an infected attachment, a popup advertisement, or an infected link. Once you do that, your device or system is held hostage till you pay the ransom.
In some cases, advertisements appear on your screen every time you click on a web page covering the part that you are trying to view. Now, there many new methods of ransomware attacks like exploitation of vulnerable servers to gain unauthorized access to an organization’s network.
What is the impact of ransomware?
Ransomware exploits its victims to extort money. You will face the choice of either paying the ransom or losing your files. Also, after paying the ransom, there is no guarantee that your locked files will be released, or your system will be free from malware infection.
Also Read: Modern cyber protection – 5 vectors you need to know
Ransomware data and figures
The hackers earn a lot of money through ransomware, that is why this type of cyberattack has grown rapidly in the past few years. According to Cybersecurity Ventures, ransomware resulted in a loss of almost $5 billion in 2017, in terms of the amount paid, the information lost, and the time consumed in recovering from attacks.
In the Q1 of 2018, single ransomware named SamSam collected ransom of $1 million.
According to Forbes Technology Council, every 40 seconds a business falls victim to a ransomware attack.
By 2021, global damage costs in connection with cybercrime will reach to more than $6 trillion annually, and out of the total predicted cyber attacks, ransomware is expected to make up a larger share of total cybercrime by 2021. (according to Cybersecurity Ventures
VIRUSES
What are viruses?
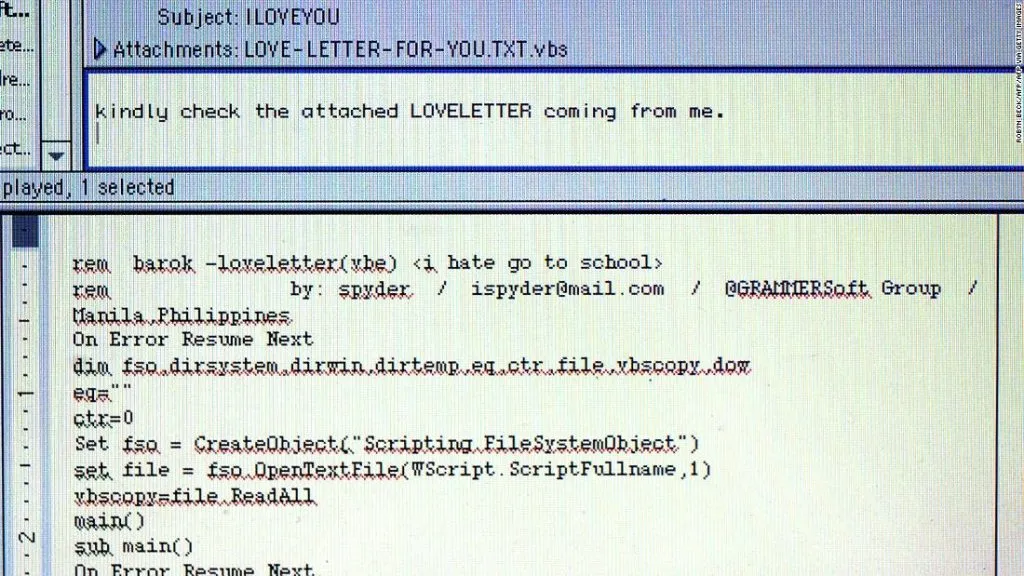
A virus is a particular kind of malware or program that’s designed to enter your device to damage or alter your files and data. It can spread from one device to another. Once it has infected a computer or a device, it can remove files, spread itself via emails, and exploit your hard drive.
Hackers use viruses mainly to steal credentials, corrupt files, capture keyboards, and take control of your system.
How do viruses affect the system?
Viruses operate mainly in two ways. The first type, soon after entering a new computer, starts duplicating. The second type doesn’t play until the trigger starts the malicious code, meaning this type of virus must run first to execute.

The hackers design viruses in such a way that they can easily circumvent antivirus software or other advanced level defenses. They come in the form of:
- Email attachments
- Free software like games
- Torrent files
- Infected USB drives
- Infected websites
Nowadays, hackers use a polymorphic technique to develop viruses to hide their presence. A polymorphic technique uses code that changes itself each time it runs like file names or encryption keys to make the virus unrecognizable to bypass many detection techniques. Such viruses are harmful and destructive in nature.
Also Read: 5 powerful cybersecurity solutions every business needs
What is the impact of viruses?
All viruses are not destructive. However, most of them perform malicious tasks, for example, destroying data on your computer.
Once the virus spreads into your device, it can start executing the actions its creators built it for. For example, scanning the hard drive for banking credentials, getting access to keystrokes for stealing passwords, connecting the computer to the internet, and using it to launch a DDoS attack, a ransomware attack, etc.
Viruses’ data and figures
Viruses are some of the most successful forms of malware out there. There are computer viruses which have caused damages to companies years later they first appeared. For example, an SQL slammer virus, that appeared first 15 years ago, is still causing issues by launching DDoS attacks.
Another 10-yearold virus named Conflicker still ranks among the most common and successful computer viruses. In 2019 itself, the virus infected over 530,000 organizations.
The 2017 WannaCry ransomware cryptoworm infected more than 300,000 devices across the world, with total damages ranging from millions to billions of US dollars.
Learn how Acronis cybersecurity solutions can help you destroy viruses.
RANSOMWARE VERSUS VIRUSES – COMPARISON TABLE
| Ransomware | Viruses |
| Ransomware is an advanced kind of malware that uses cryptovirology to block access to files in the system unless ransom is paid. | Virus is a kind of malware that is capable of duplicating itself that can corrupt the system or destroy the data. |
| Ransomware can spread through phishing emails containing malicious links or attachments. | Viruses can spread through computer programs, data files or the boot sector of the data storage device they get attached to. They appear to be harmless but actually damage the system. |
| Ransomware can present itself in many ways to block data access for money. | They are mostly known to spread themselves once they are run. They don’t necessarily involve a ransom. |
| There are mainly two types of ransomware: CRYPTO and LOCKER. | There are mainly two types of viruses: NONRESIDENT and RESIDENT. |
| The only way to protect your system and critical files is by paying the ransom to the hackers. | The best way to protect your system from viruses is by installing an anti-virus software. |
Wrapping up: protect your critical devices
The best way to protect yourself from ransomware and viruses is to use an advanced anti-malware technology that scans your computer and other devices for malicious files and removes any infected ones to protect your data.