Cybersecurity: An essential condition for the digital transformation of utilities
Blog: Capgemini CTO Blog
Energy operators are accelerating their digital transformation in order to meet the challenges of energy transition, adapt to new consumer uses, and optimize their operations. However, digitalization, together with structural changes in the sector, such as decentralization or the arrival of purely digital players, significantly increases the risk of cyberattacks. Multifarious, these now affect all segments of the energy value chain.
Changes in the sector that are making cyberattacks easier
Despite the means put in place—the creation of the European Union Agency for Network and Information Security (ENISA), the adoption of the Directive on Security of Network and Information Systems (NIS directive), and the strengthening of regulatory frameworks worldwide—the conclusions are alarming: the number and sophistication of cyberattacks are on the rise.
Recent large-scale cyberattacks, such as Wannacry in May 2017, show that all companies are threatened while the probability of identifying and prosecuting hackers remains limited.
Certain strategic sectors, such as the energy sector, have experienced a surge of cyberattacks over the past decade, with a rising trend toward sabotage attempts. Between 2010 and 2015, the number of cyberattacks on Utilities worldwide increased six-fold, placing the sector in second place among the most-targeted companies. According to the Ponemon Institute, in 2015 the energy sector suffered the heaviest financial losses caused by cyberattacks; second only to the financial sector.
These risks are exacerbated by the following trends:
- The generalization of remote asset management and control systems (SCADA), facilitating intermittency management and the decentralization of the means of production, but their complex architecture is difficult to protect end-to-end.
- The rise of IoT, notably, enables home automation, active energy efficiency services, and increased collection of customer data; however, the inability to protect connected objects increases the risk of data theft.
- The rise of the industrial internet is pushing the deployment of connected objects, such as sensors, which can serve as vectors of attack towards a more critical system if they present a security breach within energy infrastructures.
- The increasing use of cloud services and open data, which are available to a wide range of users outside the folds of IT security, can render the services hosted there more vulnerable.
All segments of the sector’s value chain have already been hit by cyberattacks, showing that repercussions can be significant in human, material, and financial terms.
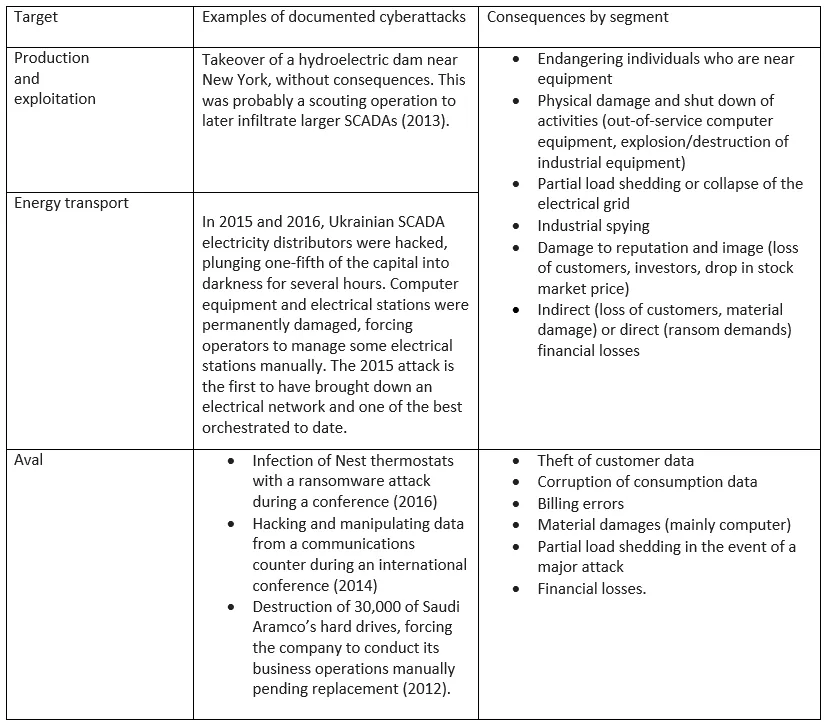
Source: Capgemini, 2018
Finding a middle ground between protection and competitiveness
France’s cybersecurity regulatory system makes the country a leader in this subject. Through decrees developed in close collaboration with Operators of Vital Importance (of which many players in the energy sector are a part), the French State provides a precise framework for companies to evaluate and address their risks. This French specificity also places a national authority—the ANSSI (National Agency for the Security of Information Systems), backed by an arsenal of available measures—at the disposal of the private sector.
While reporting cybersecurity incidents to the ANSSI is, for example obligatory, in France, it remains optional in the US, where incident reporting to competent authorities is voluntary. Moreover, the European Union is trying to replicate the ANSSI model in all Member States.
These measures allow Utilities to pursue their digital transformation strategies without neglecting to protect their assets—but at the cost of a significant increase in the cost and time required to implement digital projects. They particularly hamper innovation in open data or API and limit the possibilities of data recovery.
Operators must thus fully segregate the network upstreaming the information from the communicating meters (Advanced Metering Infrastructure) and SCADA in order to manage electricity distribution. This measure does not allow for the real-time use of the data collected by the counters to balance the network.
In other words, this configuration severely limits evolved smart grids. It also limits the speed and ease of on-site intervention by technicians, who can’t use the data collected by SCADA in real time (on their tablets, smartphone, etc.)
In a context where digital levers help reduce operational costs to improve customer satisfaction and create new services, helping companies digitalize is critical for the French energy industry to remain competitive. The answer will, perhaps, be found in cooperating on a European scale to develop viable solutions.
Reimaging cybersecurity around major structuring principles
Energy players also have an opportunity to change their operating posture to support the emergence of these solutions and adapt to changes in the sector in a way that is adequate to current security requirements. Cybersecurity is still too often treated as just a costly constraint on digital projects and cybersecurity professionals intervene in projects late in the game.
They must in particular:
- Start thinking about cybersecurity as a profitable (financial risk-reducing) activity, and not just a simple expense as is the case now and monitoring its economic impact on projects. This would, in many cases, justify increasing cybersecurity budgets, which are still low, given the stakes.
- Enhance the role of Chief Information Security Officer (CISO) by:
- Involving the CISO in the digital innovation strategy, alongside CDOs and CIOs
- Consulting the CISO from the very start and involving them for the duration of energy projects so they can advocate for innovative security solutions without compromising the value of the project
- Making the CISO part of the success of a project, in addition to the availability of the service.
- Support innovation by provisioning APIs and secure application co-development environments for an open ecosystem comprising universities, SMEs, start-ups, and large groups.
- Internally develop the skills and new positions that bridge the areas of expertise (information security, development of digital services, and industry knowledge). Training employees to have information security reflexes is also an essential part of cybersecurity, because employees are in almost always a vector of attack without being aware of it.
An organizational paradigm shift is needed within Utilities if they are to digitalize their operations at minimum risk and benefit from the levers of competitiveness related to innovation—in particular, the possibility of creating an open ecosystem of players developing digital services. Cybersecurity must no longer be treated as a separate component, a mere corollary of digital projects. It must be an integral part of the organization and its operational modalities.
Written by Pierre Duchesne, Director; Gabrielle Desarnaud, Consultant—Capgemini Consulting