A Ransomware Recovery Maturity Model is a Must
Blog: Jim Sinur
Ransomware is one of the biggest cyber security threats in 2023 and seriously threatens businesses of all sizes. Ransomware attacks work by infecting your network and locking down your data and computer systems until a ransom is paid to the hacker. A user or organization's critical data is encrypted, so they cannot access files, databases, or applications. A ransom is then demanded to provide access and keep data resources from downstream data sales. Ransomware is often designed to spread across a network and target database and file servers and can thus quickly paralyze an entire organization.
The overall amount of damages paid for ransomware attacks in 2021 was around $20 billion, with payouts in 2030 estimated to total approximately $231 billion. It is just the tip of the cost iceberg because all organizations will pay significant sums of money to defend in depth against Ransomware. Once struck, the time to recover using traditional methods ALWAYS requires way more time and effort than is ever considered. According to the IST Ransomware Task Force, the average downtime can be 21 days, with full recovery taking an average of 287 days from the initial ransomware incident response. The threats and costs are growing so fast that Ransomware has risen to the number three concern during this critical infrastructure attack era. Gartner says businesses are shoring up their defenses by spending another 11% more in 2023. Therefore a Ransomware Recovery Maturity Model is essential and becoming part of an overall security effort covering and recovering from threats and attacks.
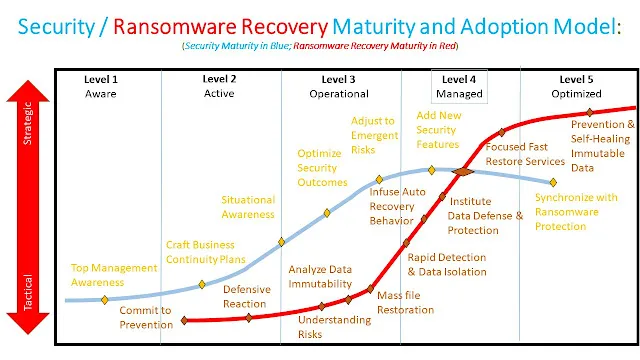
Figure 1 Ransomware Recovery Maturity Model
The Dangers
As cybercrime escalates, the dangers and costs increase dramatically. It may not be apparent, but adversaries are stockpiling your vulnerabilities. Once made public, there can be a feeding frenzy. A growing number of threats from various sources and kinds of attacks should concern businesses. There is now a sophisticated and growing ecosystem of harmful sources, including:
· Corporate Gangs/Mafia
· Developers
· Access Brokers
· Competitive Forums
· Affiliates
· Crypto Brokers/Money Launders
· Dark Public Relations
Today Ransomware is plenty sophisticated, with not only lockdowns of data but the selling of exfiltrated credentials, data, and even direct access to data and systems. The bad actors are stealing from accounts, committing personal extortion, hacking for hire, and selling sensitive customer/lead data. They use various methods and techniques, including:
· Installing Adware
· Crypto mining
· Credential Theft
· Launching Attacks
· Sending Spam Emails
· Creating Proxy Sites
· Resource Renting
Ransomware of the future intends to maximize the haul, optimizing the revenue per event and victim by leveraging advanced automation and intelligent bots that can swarm to opportunities.
Why a Ransomware Recovery Maturity Model?
Ransomware is rising to the point of a ubiquitous threat, morphing to become more lethal by the day. A growing Ransomware Ecosystem makes the perpetrators seem like a regular organization. Bad actors release press releases to put a veneer on top of the gangs, bribers, opportunistic developers, and brokers. These bribers are out to take your money, so laying down strategies and tactics is undoubtedly worth the time and money. If they can't bribe your organization, they will sell your data for profit or even do both. They are trying to maximize their profit per victim. The above model Figure 1 lays out the progressive steps towards reactively or proactively dealing with Ransomware. The model can be used as a standard classification of ransomware protection efforts while evaluating ransomware software and service providers. The model becomes a gauge for protection levels.
It is essential to visualize the efforts that can be taken to head off the inevitable attacks or sneaky events. Ransomware is the fastest-growing vulnerability associated with cybersecurity and deserves its own set of detection techniques, proven faster reactive approaches, and proactive steps for evolving assurances. Organizations need to have a plan to deal with this growing menace. A ransomware maturity model overlaid over a well-accepted and established security model is presented here. While security gets significant attention and investment from top management in most organizations, Ransomware has not. The model phases below outline the necessary maturity steps in dealing with Ransomware.
What are the Standard Maturity Levels?
Aware
Aware is the level where management realizes that Ransomware is an issue that needs action. Security folks recognize that bad actors start small with low risk leading to acceleration and expansion. Bad actors see a compromised victim as a growing bag of money to tap and can't be trusted once the bribe is paid. Sometimes they steal data and credentials to sell later. Later they often crypto-mine and install adware. In case they use an advanced attack to steal money or leverage a campaign to phish trusted partners or customers. Education is the key to awareness even as new nasty twists emerge, but data is the essential source to attack.
Active
There needs to be a commitment to detection and recovery that protects people, processes, and data. Active action puts up some resistance and foils some simple, early attacks. It is taking a defensive reaction of informing your people and notifying constituents to watch out for phishing attacks that open holes in the security perimeter is a vital action here. It means better-communicated policies to mitigate social engineering attacks that entice people to open emails and links, allowing a gateway for further evil actions. Multi-factor authentication is a typical response. It may mean you have to teach users to spot rogue URLs.
Operational
Operational is where there is a concerted effort to put good practices into place that make it hard for ransomware perpetrators to cash into revenue streams. It means focusing on understanding the risky areas of your organization's assets. There needs to be a repeating process for classifying data and processes for the organization's risk level. Risk analysis and prioritization are vital ongoing efforts. Organizations must assume they have already been infected and look for dormant attachments to patches and other code parasites. Key data sources must be clean before backups can be trusted. It means that data changes must be tracked and analyzed. Once cleaned, some mass data restoration procedures must be in place.
Managed
Managed is where the efforts turn to early detection, focus, and isolation. Now batch detection depends on real-time. Intrusions are found early, and affected data is isolated whenever possible to prevent infection spread. Isolation allows for a more focused recovery that optimizes speed to restoration. Even if isolation is not possible, automation of the recovery process should be established. Knowing that a clean backup is available close in synch with current operations allows for automation of mass recovery minimally or focused recovery ideally. It makes data defense and protection a cornerstone of response to Ransomware.
Optimized
It is making this automation smarter and closer to self-healing, the next step in the maturity model. It is done without human intervention except for notification that it has occurred. It means that AI and analytics are used to detect cyberattacks that are in progress, respond to threats intelligently, and eventually enable bots that detect advanced malware. It now becomes "good-bots vs. bad-bots."
Net; Net:
A ransomware maturity model is necessary to determine the level of protection and understand what is being done to avoid paying the bad guys. The maturity model also is used as a guide for the protection from ransomware journey that gives directions and guideposts to show progress and feel like progress is understood in context. Ensure your ransomware technology and service providers subscribe to a maturity model to track progress for better protection. It is an escalating war that needs constant tuning. Organizations can't wait to be attacked, as a ransomware event's probability of getting hit by the day is getting higher. It's not just the crooks as we hear of wars and rumors of wars generating cyber attacks that may include payoffs. Getting ahead of these attacks is crucial by spending more time and effort upfront to defend, detect, and data-proof your organization. Hiring an experienced set of services or buying important software is wise.
Additional Resources:
CIS Controls