What’s your Secure Remote Work Maturity Level?
Blog: Professional advantage - BPM blog
Australian organisations adapted quickly and impressively to remote working when the COVID-19 pandemic hit. With applications in Microsoft 365 such as Microsoft Teams and SharePoint, mimicking the real office as a ‘virtual version’ has been much easier to achieve.
[RELATED CONTENT: Not-for-Profit, Construction, and Professional Services companies that have made the right decision to move to Microsoft 365. Read their success stories here.]
Employees can now easily collaborate in real-time, communicate anywhere on any device, and have highly functional team meetings online—all crucial for a productive, efficient, and highly mobile digital workplace.
While that is a win for all of us, remote working comes with its share of challenges especially from a security point of view. IT teams are faced with managing a number of increased concerns and some key user risk scenarios which are identified below:
- Phishing scams that may cause business disruption or financial loss.
- Accidental (or intentional) data breach and related reputational damage.
- Use of unprotected personal laptops or mobile devices exposing data and systems to unseen risks.
- Use of ungoverned and risky cloud apps that may cause data loss, data breach, back doors, and more.
At our recent webinar, 80% of the respondents indicated phishing risk and data breach were the top remote work security challenges they are concerned about today.
Many of our client conversations are now focused on data protection and security with companies becoming more conscious and aware of the risks of remote working. A surprising number, however, are lacking the sufficient tools to detect, respond, or recover from a cybersecurity incident in a remote work world. Many organisations are still using traditional security tools only.
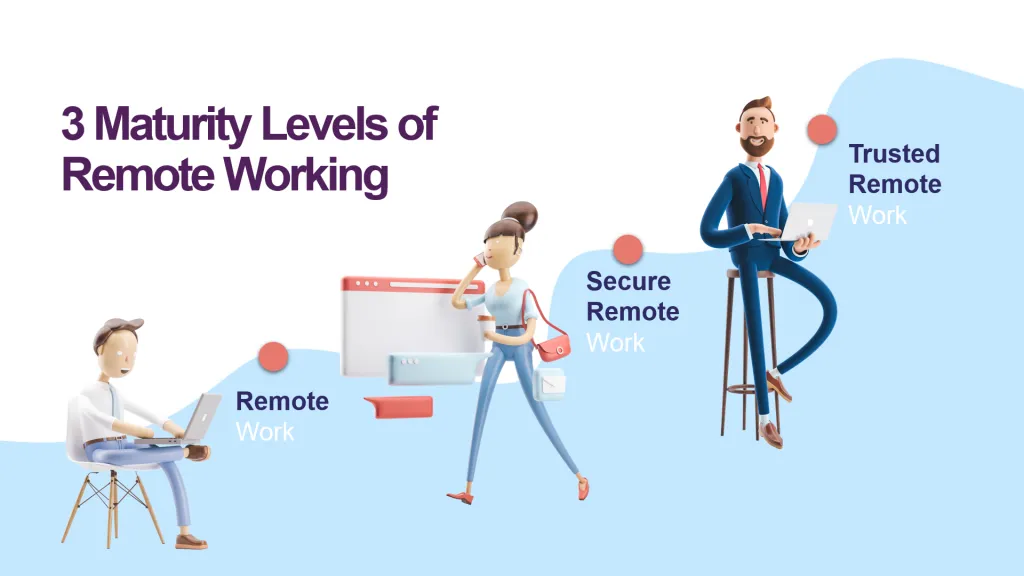
In this blog, we share the three maturity levels for remote working so you can compare your current standing against where your organisation needs to be, and you can take action to mitigate your risks.
Tier 1: Remote Work With Traditional Security
What it looks like?
Most organisations start here. Remote Work where a company uses the traditional security tools and approaches such as an anti-virus, a good firewall, and secure passwords, which are all fundamental baseline security practices. However, with people now using their home networks and their personal devices, there are different risks that come into play. Phishing or malware is harder to detect with these traditional security tools and identity (user log-in credentials) present the keys to the castle. Many organisations today are still under-protected when it comes to securing user identity.
Recommended action
Microsoft 365 offers other tools already available for you to add that extra protection. By turning on both multi-factor authentication (MFA) and data loss prevention (DLP) rules, you can better protect against identity incidents like phishing attacks, as well as aid against accidental or intentional data breach. These are starter options for enhancing your secure remote work maturity, but there is much more to consider.
Tier 2: Modern Secure Remote Work.
What it looks like?
A Modern Secure Remote Work environment goes a step further from the typical security tools. It uses identity protection as its new firewall to guard against even the more advanced threats such as state-based attacks, criminal and syndicate driven threats, and inventive and persistent hackers and malware. It determines the security policies to be applied based on user location, network, and device used. It safeguards the email and web content users access no matter where they are based. And a Modern Secure Remote Work environment also makes security easy by simplifying it for users and support teams.
Recommended action
Enable Defender for Office 365 (Formerly Office 365 ATP) for Safe Links, Safe Attachments, and Anti Spoofing. It’s a quick and simple enhancement, and the visible email attachment scanning and safe links notification when browsing provide user protection, comfort, and reassurance. Microsoft 365 enables a secure Bring Your Own Device (BYOD) service with Intune ensuring users can only access and work with corporate data within company owned applications and governed services (irrespective of if it’s the users own device). Data breach risks are limited with Conditional Access Policies, that control exactly what is accessible for users based on the users device security configurations, secure or unsecured network access, and more. Self-Service Password Reset (SSPR) and Single Sign On (SSO) should be configured leveraging Microsoft Azure Active Directory Premium to reduce risks and protect your employees’ identities, and Self Service Password Reset makes life a lot easier for support teams as well. Users and Support teams alike will thank you.
Tier 3: Trusted Remote Work.
What it looks like?
Trusted Remote Work is when your organisation has the capability, visibility, and confidence to prevent, detect, and respond to all cyber threats without restricting user productivity. You have confidence in your tools, policies, practices, and your compliance that allow you to secure remote work and manage productive sharing of company data with the right partners, customers, and suppliers without fear or risk of data breach and compliance issues.
Getting to a trusted state in remote working means spanning across protection for your devices, places, users, data, and more. It means protecting your data wherever it goes; detecting when a dubious or atypical action is being taken; advanced safeguarding against accidental or deliberate breach no matter where your data and IP traverses; and clear and connected security signals proactively shared and visible to your control centres.
Recommended action
Invest in a robust and connected security system with Microsoft 365 Defender tools and build your trusted Security across:
- Identity.
- Devices.
- Apps.
- Data.
There are some incredibly useful tools available if you explore a little further.
Add Microsoft Defender ATP cloud service delivering you real-time environment vulnerability assessment, graphical ‘threat spread visibility’, and with detailed recommended mitigation actions for both Servers and Workstations (in and out of the office).
Identify your user vulnerabilities using the Microsoft Attack Simulator. Launch a dummy phishing attack to your organisation and see how your users will respond. Ensure you provide the appropriate user education where needed and test again.
Leverage a central insights tool like Microsoft’s Cloud App Security to detect identity risks with ‘impossible travel scenarios’ and risky overseas locations. Be alerted to suspicious user behaviour activities such as ‘mass download’ of data. Audit ungoverned apps that access your resources, and review sharing and data activities that are against company policy. You can watch our short demo here to get a closer look at Microsoft Cloud App Security.
Consider Microsoft’s Azure Information Protection (AIP) to ensure that your data remains confidential, even when it is shared to users outside of your organisation. AIP enables you to label files in file shares, SharePoint, and Teams, with policies applied to the labels that control what data can be accessed and shared, and to enforce that your file is only accessed by the people it is intended for, no matter where the file resides or traverses.
Security is all about identifying your risks and evolving your layers. It is not always possible to achieve “ideal”, but it is always possible to improve. If you’re not sure what the right approach for you is, then engage an expert to assist you. An outsiders view is not only a reassurance for you, but is often a compliance requirement or a request by a board of directors.

Be safe now, not sorry later.
Putting the tools and policies in place to keep your organisation cybersafe is often perceived like life insurance. It is a ‘pre-need utility’ that is misconstrued until something bad happens. In many cases however, the financial loss and reputational damage that go with a data breach is far greater than investing your time and budget in securing your digital workplace.
We encourage you to take a closer look at your current remote work security posture. By detecting your risks, you can better plan how to protect your data against and respond to cyber threats. We can help you assess your risks with our 2-day Remote Work Security Assessment. If you simply need someone to consult with, you may also comment below or reach us at 1800 126 499.
The post What’s your Secure Remote Work Maturity Level? appeared first on Enterprise Software Blog - Professional Advantage.