What is White Box Penetration Testing?
White box testing cannot be considered penetration testing in itself. Auditors who perform this testing do not work from the point of view of an attacker. It is more of a thorough security analysis.
- What is Penetration Testing?
- What is White Box Penetration Testing?
- Why White Box Penetration Testing?
- When is White Box Penetration Testing necessary?
- White Box Penetration Testing Techniques
- Benefits of White Box Penetration Testing
- Drawbacks of White Box Penetration Testing
- White Box Penetration Testing Steps
- Conclusion
Anytime a product or application is developed and accessible over a computer network, it needs thorough testing to ensure that it is not prone to malicious hacking. White box penetration testing is crucial when it comes down to testing devices that are involved with critical infrastructure and that store, process, or transmit sensitive information.
Here is an introduction by Intellipaat to the fundamental concepts of Cybersecurity.
What is Penetration Testing?
A penetration test, also known as a pen test, is an attempt to assess the security of an IT infrastructure through simulated attacks that safely try to detect and exploit vulnerabilities in the system. The vulnerabilities may be in the operating system or services or in the form of improper configurations, application flaws, or risky end-user behavior.
The assessments validate the efficacy of defensive measures and systems as well as the adherence of end users to security policies.
Penetration testing is usually performed manually or by using automated technologies to systematically compromise servers, web applications, network devices, endpoints, wireless networks, mobile devices, and other potential points of exposure.
Once a vulnerability is exploited on a system, testers then, sometimes, attempt to use that to launch further exploits at other internal resources. This is achieved by attempting to progressively achieve higher levels of security clearance as well as deeper access to information and electronic assets with the help of privilege escalation.
What is White Box Penetration Testing?
White box penetration testing is when the auditors know the internal composition of the software or system. Contrary to black or grey box testing, white box testing aims to uncover deep details of the system undergoing the test. Reasonably so, it is also known as a clear or transparent box testing.
White box penetration testing grants testers access to the system in question. Through this testing method, they become aware of the application in every aspect, thus giving a clear picture of all possible entry points into the system.
The penetration tester has access to information so that they can mimic the activities of a scheming hacker, which is the actual terrifying threat to a system’s safety. The test imitates the hacker’s actions but with more access to the system’s information.
Sign up for Intellipaat’s Ethical Hacking Course and get a head start in your career.
Why White Box Penetration Testing?
We already know that white box penetration testing involves breaking into an internal system and diagnosing its weaknesses. The question, however, is why is it important?
Cyber safety is oftentimes neglected and not taken as seriously as it should be. Organizations remain under the assumption that the existing security of their applications is sufficient as is until, of course, something goes wrong. Why wait for the damage to happen when it can be prevented in the first place? Invest in better security infrastructure and save on unnecessary expenses in the long run.
Organizations are bound to suffer service outages or data breaches one day or another if their security vulnerabilities are not addressed initially. Identifying these vulnerabilities and proactively making an effort to close these gaps is a forward-thinking strategy when it comes to running a business efficiently.
This testing is crucial for the detection of both internal and external threats in web-based applications before the commencement of production. No matter how daunting a task software security is, every business has to have a QA team whose skills lie in thorough analysis using specific techniques and technology that are exclusive to the organization.
White Box Penetration Testing Examples
The more critical a system or software one is dealing with, the more thorough the testing should be. Deploying bank apps’ security is a perfect example of a system that has to go through white box penetration testing. The primary objective of penetration testing is to test areas to find licit and illicit parts of the app that hold customer information and other storage and processing facets.
Another example of white box penetration testing is confirming the database security of a military or rocket ship. The tester needs to test every feature and facet of the system, one code at a time. No database should have room for vulnerabilities, both externally or internally.
When is White Box Penetration Testing necessary?
Knowing exactly when it is necessary to carry out white box penetration testing is crucial. It is typically executed in the early stages of development before the software or system is launched. Below are a few examples of when white box testing is used.
- During software development: Sometimes, developers themselves do the testing before releasing the finished product. Testing at this stage is better as all changes can be made, as necessary, there and then.
- After software development and before release: Developers, sometimes, prefer to do the test after the development stage but before the product launch.
- After software release: There are a few cases when the software is already in use and the testing has to be carried out to detect internal errors and fix any system defects that may compromise user security.
However, not every situation or network is suitable for white box testing. This is due to the nature of the test itself as it is meant to thoroughly examine every nook and cranny of the system using internal and external information.
White Box Penetration Testing Techniques
One of the main objectives of white box penetration testing is to cover the entire source code as exhaustively as possible. Code coverage is, in fact, a metric that reveals how much of the code has unit tests checking the code’s functionality. Within code coverage, one can verify the level at which an application’s logic is executed and tested by the unit test suite.
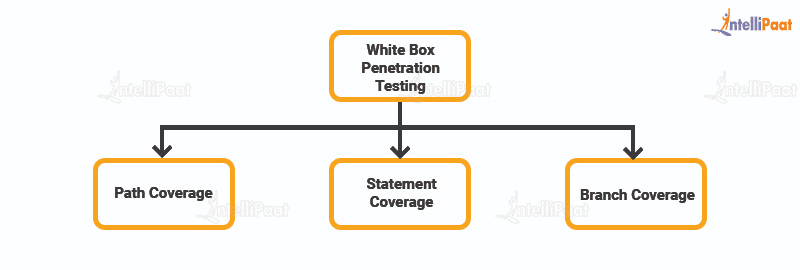
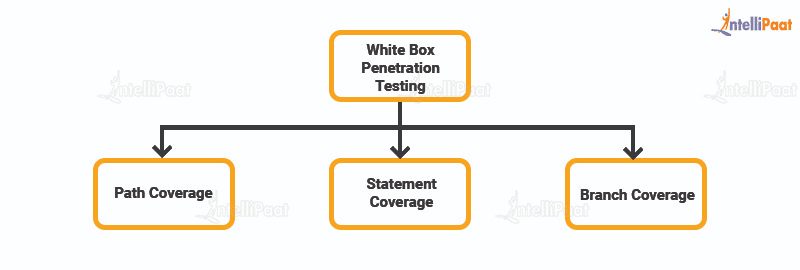
There are three main techniques of white box penetration testing:
- Path coverage
- Statement coverage
- Branch coverage
Path coverage: It focuses on the linearly independent paths through the code. Usually, a control flow diagram of the code is drawn. This methodology is aimed at all paths. It determines if every path has been crossed. Path coverage is a lot more critical than branch coverage. This technique is ideal for testing complicated builds.
Statement coverage: This technique is for checking if all executable statements in the code are tested at least once. It helps to uncover unused or missing statements and branches as well as leftover dead codes.
Branch coverage: This method is to confirm that all branch codes are tested. It maps the code into branches of conditional logic and ensures that all branches are covered by unit tests. One should ascertain that all codes have been launched at least once.
Apart from the three above-mentioned techniques, there are a few other white box testing techniques:
- Decision coverage
- Condition coverage
- Multiple condition coverage
- Finite state machine coverage
- Control flow testing
- Data flow testing
Have a look at our blog on Ethical Hacking Tutorial and learn more on this domain.
Benefits of White Box Penetration Testing
There are many benefits of this testing technique. Some of them are:
- Meticulousness: All that access to information means that the tester can be very thorough and extensive with the analysis.
- Efficiency: As the tester has access to ample information from the start, this testing method saves a lot of time.
- Bug detection: It is highly likely that a tester will discover bugs and errors with this type of testing.
- Clarity: The clear box nature of white box testing makes it possible for the internal system to be tested.
- Modifiability: It is easy for developers to make modifications in the system, especially in web app development. The apps can be secured even during the development phase.
Career Transition
Drawbacks of White Box Penetration Testing
White box penetration testing comes with a few drawbacks. Let us explore the challenges that the QA team experiences when performing this type of testing.
- Having easy access to information might lead the tester in going in an entirely different direction than a hacker would go.
- It can be a slow process if the tester has to cover a large amount of data.
- The thorough and extensive analysis of systems can be a tedious task to execute.
Preparing for Ethical Hacking job interviews? Have a look at our blog on Ethical Hacking Interview Questions and excel your hiring journey!
White Box Penetration Testing Steps
Let us now understand the step-wise process of how this testing is carried out. Below is an illustration of what is included in the testing process.
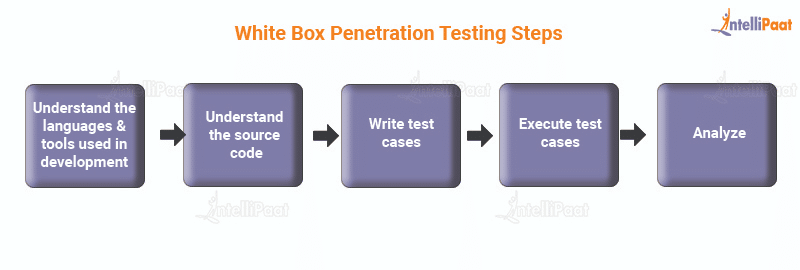
- Selection
The first step is to determine the areas that need to be tested. It is recommended to narrow down the core areas of a system. The more precise the test area is, the better it is. This is because the test is meant to cover every possible scenario that can run code by code.It is more efficient to consider the myriad of possibilities in a smaller area than a larger one as it would not guarantee the same coverage. While it is not impossible to do a large area, a lot of effort, resources, and labor will be involved for the test coverage of the same.
In most cases, it is imperative that every inch of the system be secured. In situations like these, it is not tactical to run the test only when required.
- Identification
- Outlining all the code lines that are likely
- Identifying all possible codes that cover functionality or the aspect of the system that requires testing
- Writing the output of each code in the flow chart
Identification organizes the process and keeps it straightforward. At the same time, it helps to identify the possible codes, permutations, etc.
- Writing Test Cases
It is essential to write test cases for every step. Every test case should include what could go wrong, where testing for vulnerabilities can be carried out, and other similar records. - Execution of Test
This step involves actually putting the plan into action.- Start executing everything laid out in the plan
- Test over and over till you have covered all the outlined systems and no issues are left
White Box Penetration Testing Tools
Some of the most widely used tools are:
- NUnit
- JUnit
- John the Ripper
- Metasploit
- HtmlUnit
- CppUnit
- EclEmma
- Efix
Conclusion
White box penetration testing is a great approach to strengthen software security. It can get complex depending on the application being tested. Testing a small application that performs simple operations is only a matter of a few minutes. Large applications take much longer; we are talking days, weeks, and months.
The testing should be carried out during the software development stage, after it is written, and also after each modification. Though white box testing has its limitations, there is nothing that can take away from all its benefits. However, it is worth mentioning that white box testing alone cannot plug all the loopholes in a system. White box testing is best paired with other types of tests.
For knowledge about white box pen tests, visit Intellipaat’s Cyber Security Community.
The post What is White Box Penetration Testing? appeared first on Intellipaat Blog.
Blog: Intellipaat - Blog
Leave a Comment
You must be logged in to post a comment.