What is SSL Handshake(Secure Socket Layer)?
SSL: Secure Socket Layer
SSL, or Secure Sockets Layer, is an encryption-based Internet security solution. Netscape developed it in 1995 to assure privacy, authentication, and data integrity during Internet interactions. TLS encryption today is the successor of SSL.
The URL of a website that employs SSL/TLS begins with “HTTPS” rather than “HTTP.”
The topics to be discussed in the blog are:
Overview
- What is meant by SSL?
- Why SSL handshake was also known as the TLS handshake?
- The differences between SSL and TLS
- How does SSL Work?
- The procedure for SSL handshakes
- What is the level of security provided by an SSL/TLS handshake?
- SSL Protocols
- SSL Certification and Types
- Advantages and Disadvantages of SSL
- Conclusion
Interested in cyber security? This youtube video is just made for you! Learn from basic to advance.
What is meant by SSL?
An SSL handshake connects two devices, such as your browser and the server that hosts the website you want to visit.
The two devices determine the following during a SSL:
- Which security version will both parties use?
- What kind of encryption will be used to protect the data?
- How are both parties authenticated?
The use of the name “SSL” in the SSL handshake is deceptive. The secure sockets layer (SSL) technology is ancient and hardly used nowadays. Most devices currently use transport layer security (TLS).
Although “TLS handshake” is more accurate, nowadays the term in buzz is “SSL handshake”.
Why SSL handshake was also known as the TLS handshake?
If you open a webpage in your browser, you may believe that the connection occurred both instantly and spontaneously. In practice, the two devices must reach an agreement on how to communicate and share data. An SSL handshake is used for this negotiation.
The SSL handshake is also known as the TLS handshake because:
Netscape invented the SSL protocol in 1995. Unfortunately, it had a number of security flaws. The industry changed to the TLS protocol in the early 2000s in the hopes of boosting security. The handshake method stays the same, despite the nomenclature change.
A communication session begins with an SSL handshake. The two parties acknowledge each other, agree on how to protect the information, validate each other’s security measures, and establish session parameters.
Exploring the field of Cyber-Security, what’s better than getting an overview just a click away, do check out our Cyber-Security Tutorial!
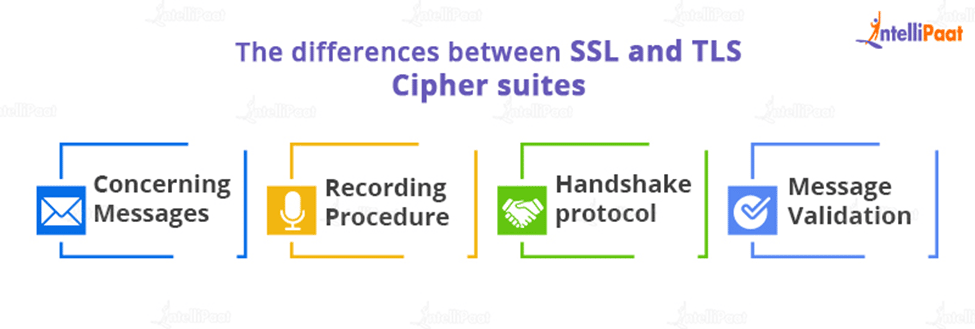
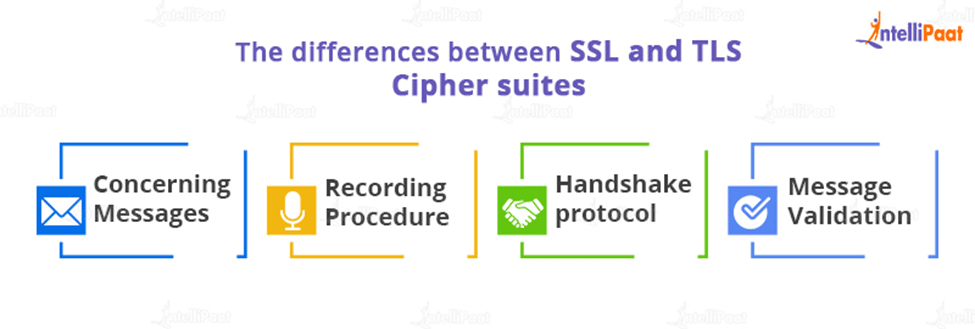
The differences between SSL and TLS
However, the differences between SSL and TLS are minor. Only a technical expert will be able to tell the difference. Among the significant differences are:
- Cipher suites
The Fortezza cipher suite is supported by the SSL protocol. TLS does not offer any support. TLS offers a better standardization process, which makes it easier to create new cipher suites like RC4, Triple DES, AES, IDEA, and so forth.
- Concerning Messages
SSL displays the warning message “No certificate.” The TLS protocol substitutes various other alert messages for the alert message.
- Recording Procedure
SSL uses Message Authentication Code (MAC) after each encrypted communication, but TLS uses HMAC — a hash-based message authentication code — after each message encryption.
- The handshake protocol
In SSL, the master secret and pad are also factored into the hash calculation. Hashes are calculated over the handshake message in TLS.
- Message Validation
TLS relies on HMAC Hash-based Message Authentication Code, whereas SSL message authentication combines key information and application data on the fly.
These are the key differences between an SSL and TLS certificate. As previously said, understanding the distinctions necessitates a trained eye.
Want to become a professional in the domain of Cyber Security, then Cyber Security Course is a perfect place to check.
Career Transition
How does SSL Work?
- SSL encrypts data as it travels across the internet, ensuring a high level of anonymity. Anyone attempting to intercept this data will only see a jumbled mess of characters that are extremely hard to decipher.
- SSL starts a handshake authentication process between two communicating devices to ensure that both are who they say they are.
- SSL also digitally certifies data, ensuring that it has not been tampered with before reaching its intended receiver.
- SSL has gone through several iterations, each one more secure than the previous. In 1999, SSL was upgraded to TLS.
The procedure for SSL handshakes
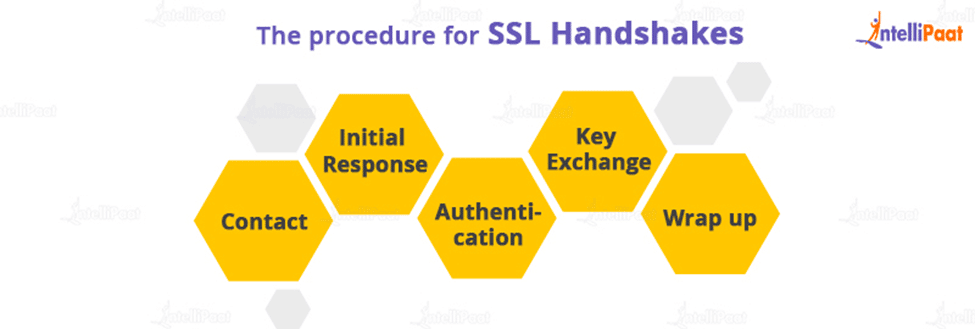
A SSL handshake generally consists of the following steps:
- Contact: A “client hello” is sent the server via the browser. The message contains critical information such as the client’s SSL version, encryption settings (more on that later), and session-specific information.
- Initial Response: As the first response, the server sends back security verification (through certificates), the server’s encryption settings, and session-specific data.
- Authentication: The browser validates the security certificate to confirm that it communicated with the correct authority.
- Key Exchange: The server and the browser exchange the keys, confirming their exchange with security.
- Wrap up: Both the parties, that is the browser and server will confirm that the exchange has taken place and the work is now complete.
Want to crack an interview and get placed, then Top 50 Cyber Security Interview Questions is the perfect fit for you.
What is the level of security provided by an SSL/TLS handshake?
A reference to key exchange can be seen throughout the SSL handshake phases. This approach uses encryption and comes in two varieties.
Encryption is classified into two types:
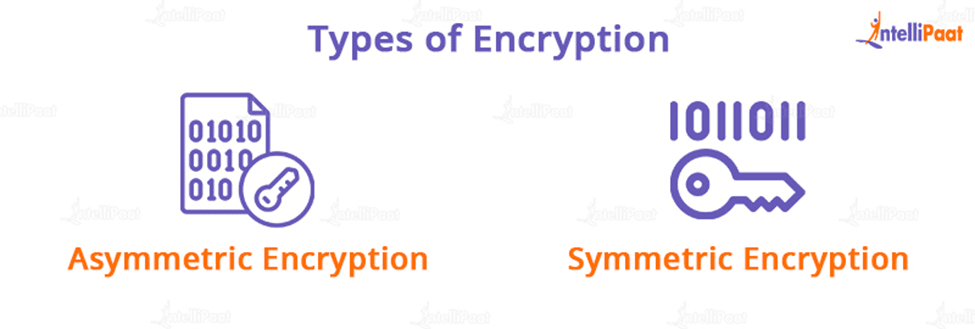
- Asymmetric encryption: A public key is used for description, which is easily available via the server’s security certificate. A private key is used for decryption.
- Symmetric encryption: Following asymmetric encryption, the two parties agree on a shared key. This single session key allows for a secure connection while also decreasing server load.
The two sides also agree on a “cipher suite,” which is a set of rules that governs what type of authentication is necessary, how data is encrypted, and other features.
These safeguards should protect data in transit. Attacks, though, remain a possibility. For example, the BREACH exploit allows hackers to modify data while it is in transit. Hackers can also take control of the system and launch a man-in-the-middle attack. The problem begins with encrypted data stolen by attackers.
SSL Protocols
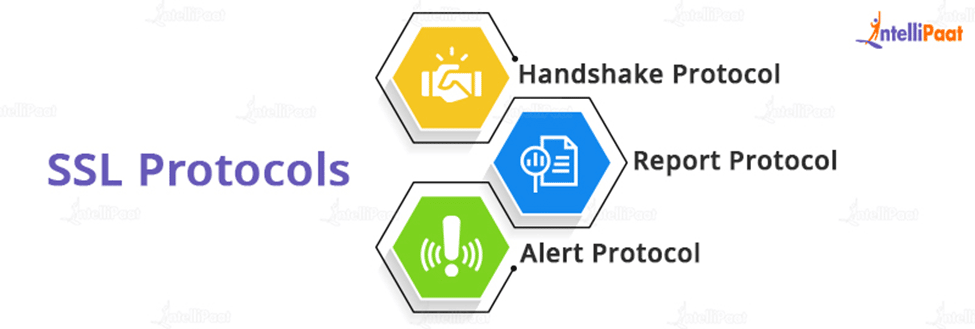
SSL’s functionality is based on three protocols.
- Handshake Protocol:
It is the first SSL subprotocol that a client and server will employ to communicate over an SSL-enabled connection. Handshake Protocol is made up of a sequence of three-field messages transmitted between client and server.
Type: This one-byte parameter specifies one of the ten message types.
Length: The message length in bytes is defined by this three-byte parameter.
Content: This one or more byte field defines the message’s parameters. The parameters are controlled by the message type.
- Report Protocol:
After the successful Handshake between client and server, the SSL Record Protocol enters the scene. In other words, once clients and servers have properly authenticated each other and determined the algorithms to employ for safe exchange, we can enter the SSL record protocol.
After the successful Handshake between client and server, the SSL Record Protocol enters the scene. In other words, once clients and servers have properly authenticated each other and determined the algorithms to employ for safe exchange, we can enter the SSL record protocol.
- Alert Protocol:
When a client or server error occurs, the detecting party notifies the other party. If the error is fatal, both parties immediately terminate the SSL connection, which means that transmission is terminated on both the client and server ends. Before terminating the connection, both parties remove the session identifiers, secrets, and keys associated with it. If the issue is minor, the connection will not be terminated; instead, the parties will rectify the error and continue with the procedure. The alert message is composed of two bytes, the first of which specifies the sort of fault. If the error value is 1, it is a warning, and if it is 2, it is fatal. The second byte represents an actual fault.
SSL Certification and Types:
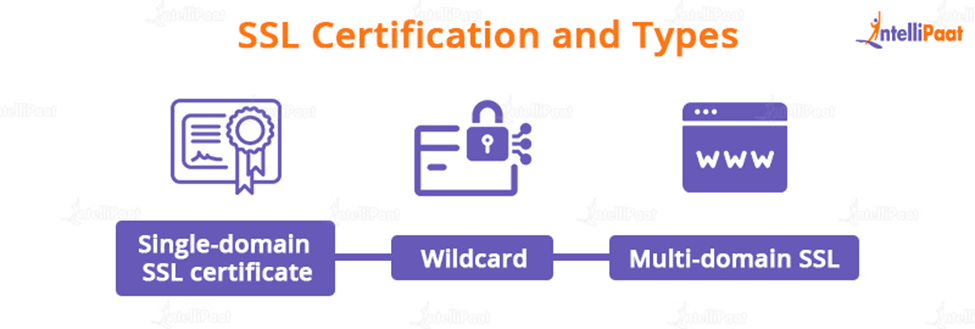
SSL certificates are classified into numerous categories. A single certificate can apply to one or more websites, depending on the type:
- Single-domain SSL certificate is only valid for one domain (a “domain” is the name of a website, like www.intellipaat.com)
- Wildcard: A wildcard SSL certificate, like a single domain certificate also applies to only one domain. However, it does include the domain’s subdomains. For example, a wildcard certificate may cover www.intellipaat.com, and intellipaat.com/blog/ whereas a single-domain certificate may only cover the first.
- Multi-domain SSL: As the name implies, multi-domain SSL certificates can be used on multiple unrelated domains.
SSL certificates are also available with various levels of certification. A validation level, like a background check, varies based on the extent of the investigation.
SSL certificates are also available with various levels of certification. A validation level, like a background check, varies based on the depth of the check.

- Domain Validation: The most fundamental and least expensive sort of validation. All a firm has to do is demonstrate domain ownership.
- Organizational Validation: is a more hands-on process in which the CA directly contacts the individual or corporation obtaining the certificate. These certificates are more trustworthy to users.
- Extended Validation: Before issuing an SSL certificate, an organization must do a thorough background investigation.
Advantages and Disadvantages of SSL
Advantages of using SSL
Google has confirmed that having an SSL will help your website rank higher in search results. The Google algorithm has been adjusted to assist websites with SSL certificates; as a result, the great majority of top results for almost any phrase will have an SSL certificate.
Disadvantages of using SSL
The expense of obtaining and setting an SSL is the biggest downside. A low-cost SSL can cost as little as £30 per year, whereas a high-cost SSL can cost as much as £2,000 per year. The problem is that when it comes to these certificates, quality is quite important because the cheapest ones are extremely poor and untrustworthy. This may cause extra confusion about where to obtain the SSL.
Courses you may like
Conclusion
SSL (Secure Sockets Layer) is a lifesaver for any website that accepts online payments or has a login page. Gaining the trust of visitors and consumers boosts a company’s Return on Investment (ROI). Several SSL attacks have targeted SSL execution issues, but the POODLE (Padding Oracle On Downgraded Legacy Encryption) attack targets a known flaw in the SSL 3.0 protocol itself, taking advantage of the way it ignores padding bytes when running in cipher block chaining (CBC) mode.
Have doubts, drop your queries at: SSL Community page!
The post What is SSL Handshake(Secure Socket Layer)? appeared first on Intellipaat Blog.
Blog: Intellipaat - Blog
Leave a Comment
You must be logged in to post a comment.