What is Carding?
- What is Carding?
- Carding Forums
- Carding Attack Process
- Avoiding Card-cracking Bots
- Card Fraud Detection
- Conclusion
With everything becoming cashless, credit card frauds are bound to happen. Therefore, it is extremely crucial to learn how not to fall prey to carding and theft.
Watch this video by Intellipaat on credit card fraud detection.
What is Carding?
Carding is also known as credit card stuffing or card verification. It is a web security threat in which attackers attempt to authorize stolen credit card credentials and use them to charge prepaid cards or gift cards. These cards are then sold or used to make purchases of goods, which can then be sold for cash.
People who are involved in Carding are called carders. Carding is performed with the help of bots and hacking software, which is capable of performing automated operations over the internet. The objective is to identify card numbers or details that can be used to perform purchases.
The United States is a high target for carding credit and debit cards. This is because the United States has a large market for cards that contain magnetic strips or chips and signature technology, unlike the more secure chip and PIN technology.
Carding Example
An example of carding was when hackers built a malicious bot named GiftGhostBot. The purpose of this bot was to hack the balances of gift cards. Around 1,000 e-commerce websites became victims of this carding attack. The advanced, persistent bot checks millions of gift card numbers automatically to identify the ones with balances. This bot is still attacking websites.
The validated gift card numbers are used to make purchases. This card cracking or token cracking attack is, typically, untraceable once the balance is stolen.
Carding Forums
A carding forum, basically, is an illegal site where stolen credit card details are shared. The forum also encourages discussions on techniques that can be used to obtain credit card information, validating it, and using it for illegal activities.
These forums are hubs for criminal groups and individuals who purchase credit card information in bulk and sell it on the dark web. These forums are hidden with Tor routing, and payments are made in cryptocurrency to avoid detection. The carder remains anonymous.
Carding forums can also be used to share the results of carding. For example, selling successfully stolen credit cards to other criminals.
Carding Attack Process
A carding attack process typically involves the following steps:
- Carders obtain stolen credit card numbers from criminal marketplaces, compromised websites, or payment channels.
- Carders then deploy bots to make small purchases on several sites. In every attempt, a card number is tested against a merchant’s payment processes to determine the validity of card details.
- The validation process is attempted thousands of times until it yields results.
- The acquired card numbers that are successfully validated are then organized into a list and used for other criminal activities or sold to organized criminal outfits.
- Carding is undetectable by card owners until it is too late and their money is stolen.
Get your Cyber Security certification from Intellipaat. Enroll today and learn from experts!
Key Points
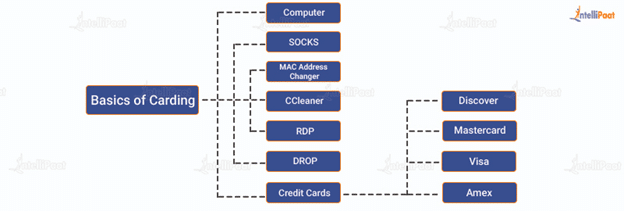
The following components are involved in the carding process:
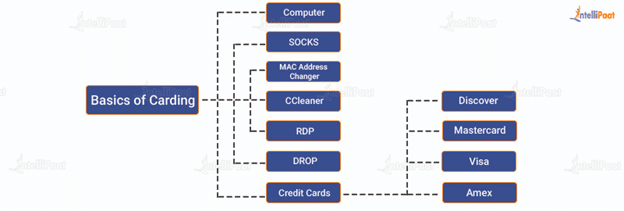
- Computer: Carding involves a computer system. Some also use a mobile device, but it is less secure and can prove to be risky. Carders use others’ PCs for executing this attack.
- SOCKS: SOCKS stands for SOCKet Secure. It is an internet protocol that enables client and server traffic to pass through a proxy server. This hides the real IP and the proxy IP gets reflected. This helps a carder to use a credit card owner’s location during the process. SOCKS are available for the carders to buy.
- MAC Address Changer: MAC is the unique address of every network interface card (NIC.) A MAC address changer allows one to instantly change the MAC of NIC; it is used for anonymity.
- CCleaner: CCleaner is useful for cleaning browsing history, cookies, temp. files, etc. Ignoring this step can prove to be risky for a carder.
- RDP: Remote desktop protocol or RDP enables computers within the same network to connect. Carders misuse this protocol to connect to computers of the geolocation of the person whose credit card is targeted. This process helps carders to stay anonymous.
- DROP: DROP is an address that is used by a carder as the shipping address during the carding process. The address has to match with the region of the credit card. Sometimes, carders use drop services with an extra shipping cost.
- Credit Cards: Discover, Mastercard, Visa, and Amex are four of the major credit card networks. Credit cards contain the following information:
- Name
- Credit card number
- Expiry date
- CVV2 code
- Address
- Phone number, sometimes not include)
Carding using Mobile Phones
Mobile phones are used only by more experienced and professional carders as it can be quite risky. Carding with mobile devices requires rooted Android mobiles. A few applications such as CCleaner, proxy apps, IMEI changer, Photo and Android ID changer, etc., are used during the carding process.
Preparing for a job interview? Have a look at our blog on Cyber Security interview questions and start preparing now!
Career Transition
Avoiding Card-cracking Bots
Here is how one can safeguard payment sites against malicious bots:
- Device fingerprinting: Device fingerprinting identifies the browser and device parameters that remain constant between sessions, i.e., if the same entity is trying to connect repeatedly, you will be able to know. This technology creates a unique device, browser, and cookie identifier. In case there are multiple logins, it will immediately raise the suspicion that these are fraud attempts.
- Browser validation: Some malicious bots are capable of pretending to be using a browser and they avoid being detected by cycling through user agents. Browser validation verifies that a browser is real with expected JavaScript agent and normal browser operations. It ensures that the browser is being used by a human and not a bot.
- Machine learning behavior analysis: Real users visiting a payment website exhibit typical behavior patterns. Bots do not follow this pattern. Behavioral analysis technology analyzes user behavior and detects any anomalies. This can prevent cracking attempts.
- Reputation analysis: Having a database of known predictable, technical, and behavioral bot patterns or originating IPs can help to identify bad bots.
- Progressive challenges: When a system detects a suspicious bot, there are progressive mechanisms in place for testing users to confirm if they are a bot or human. It uses the least intrusive method first, reducing the disruption for real users.
Here are a few progressive challenges:
- Captcha: Most disruptive to real users
- JavaScript challenge: Slightly slows down the user experience
- Cookie challenge: Goes unnoticed to real users
Additional Security Measures
Aside from the above techniques, one can also take the following measures to strengthen the security perimeter against cracking bots:
- Multifactor authentication: Most e-commerce sites require login usernames and passwords as well as keep tabs on the device used for login. While this does not entirely prevent cracking, it sets up a challenge for carders and renders it impossible or highly difficult for them to take over existing accounts.
- API security: E-commerce sites using credit card APIs are often vulnerable to attacks such as rerouting of data or JavaScript injection. For protection, these sites can make use of a combination of transport layer security (TLS) encryption and strong authentication mechanisms such as OAuth and OpenID.
Card Fraud Detection
Here are several types of payments that payment websites are able to detect as attempts by carding bots:
- Unusual order sizes
- High shopping cart abandonment rates
- A significantly high number of failed payments
- Abnormal usage, too high or too low, of the payment step
- Increased chargebacks
- Multiple failed payment authorizations from the same session, user, user agent, IP address, device ID, or fingerprint
Courses you may like
Conclusion
This blog is intended to spread awareness about carding, which is a current problem everywhere. In no way, is it a guide to encourage such illicit activities. There are multiple solutions available nowadays that can provide protection against carding.
Get all your questions answered by tech experts in our Cyber Security Community.
The post What is Carding? appeared first on Intellipaat Blog.
Blog: Intellipaat - Blog
Leave a Comment
You must be logged in to post a comment.