What is a Network Security Key?
The following topics are covered in this blog:
- What is a Network Security Key?
- Why is a Network Security Key Needed?
- How to Find Your Network Security Key?
- What are the Threats Prevented by Network Security Keys?
- Advantages of Using Network Security Keys
- Types of Network Security Keys
- Creating a Strong Password
- Are Passwords and Network Security Key the Same?
- Conclusion
What is a Network Security Key?
Network Security keys are the codes that allow access to authorized users into the network systems. These codes can be in the form of alphabetical and numerical passwords or passphrases. The various types of network security keys can be biometric entry codes and passwords or digital signatures etc. The sole motive of network security keys is to prevent unauthorized access and accessibility to a wireless network or device. Network Security keys help in establishing a secure connection between the authorized user and the network or routers etc. Network security keys are a very important part in day-to-day operations such as financial transactions, online business, and personal banking, OTPs, online portals, corporate account logins, etc. Security keys have made our lives easier and secure too.
Check out our Cyber Security tutorial to learn more
Now, below we will explore why businesses and other users need network security keys.
Why is a Network Security Key Needed?
- Network Security keys provide a secure atmosphere to carry out important activities such as financial transactions and more.
- Network Security keys protect the entire network system from unauthorized and forced access.
- Network Security keys help to keep the data safe.
- Network security key prevents foreign viruses or other cyber threats from entering and affecting the system and the entire network of systems.
- A network security key ensures that only authorized and permitted users enter the network or the system.
- Network security keys take care of the authentication and authorization control given to the network resources. In this way, the data is kept secure from internal resources as well to maintain the usability and integrity of the data.
Get our Cyber Security course in collaboration with IIT Guwahati and get certified.
How to Find Your Network Security Key ?
Sometimes, you may notice that your computer requires you to feed in your network security key. Most of the time, we do not know where to find the key. It is the router that contains a sticker with the details of the wireless network and its security key password. This security key password is the network security key. However, not every router will have the sticker on it with these details.In such situations, you can follow the following points, provided your computer is connected to the network:
Finding the Network Security Key
In case of latest versions of Windows like the Windows 10, the following steps need to be followed to find your network security key:
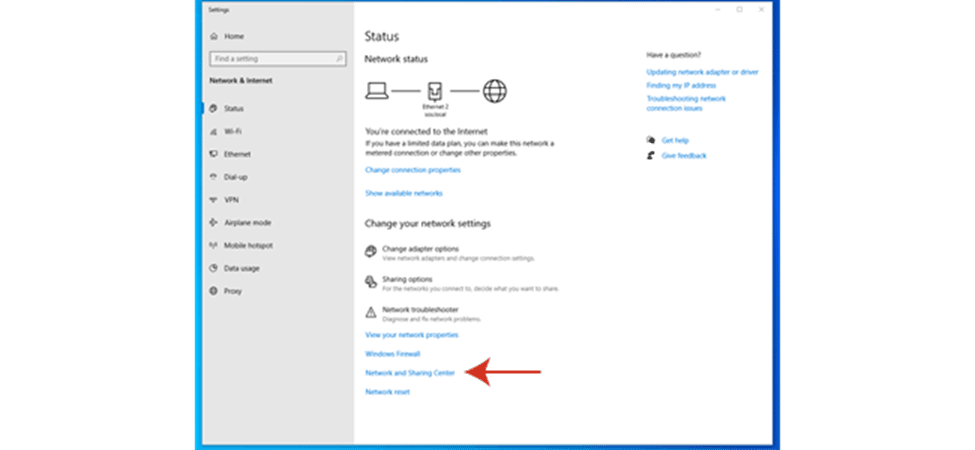
- Right clicking on the ‘Start’ menu and select “Network Connections”
- Now click on the ‘Network and Sharing Center’ option. The following window box appears.
- Enter the name of the Wi-Fi network.
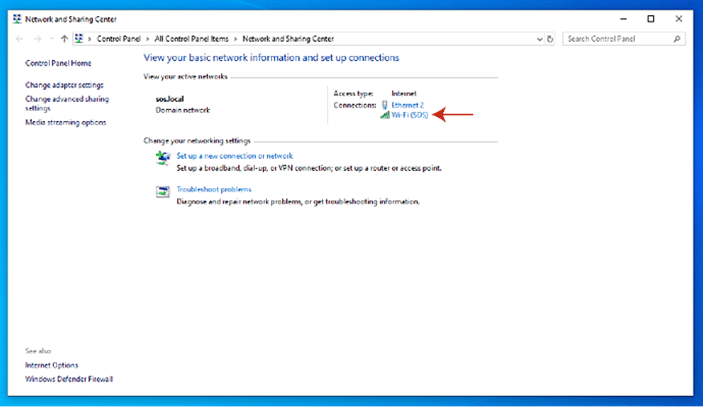
- Now you will notice a “Wireless Properties” option. Click on it and next click on the Security tab.
- Locate the “Show Characters” checkbox and access your network security key.
Now, the above steps were for Windows systems. Let us next understand how to find the network security key on a Mac System:
- Go to the top right side of the screen and click on the “Search” icon.
- In the search bar, enter “Keychain Access”
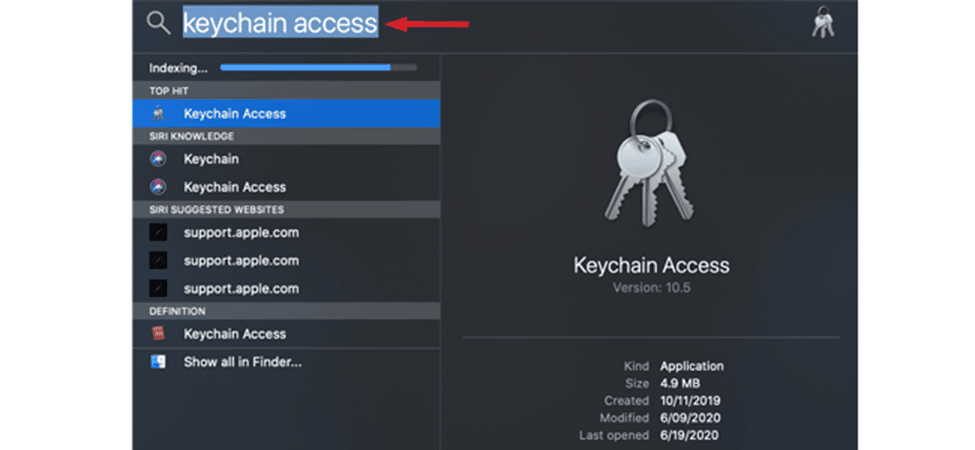
- Once you have entered the “Keychain Access”, a dialog box will appear on your screen.
- Double Click on the name of your Wi-Fi network that appears on the dialog box
- Now, select the “Show Password” checkbox
- Finally, the network security key will be revealed once you enter your Mac password.
Preparing for cyber security job interviews? Check out our blog on Cyber security interview questions now and excel your next job interview!
What are the Threats Prevented by Network Security Keys?
As already mentioned above, network security keys help in keeping the entire network and data stored safe from unauthorized access. Let us now understand, what are the different cyber threats that can be prevented by using network security keys:
Close-range Wi-Fi connectivity
It is common to see neighbors unauthorizedly connecting to each other’s Wi-Fi networks. This becomes possible in cases when the Wi-Fi networks are unprotected or have a weak security password. Many times, it might be possible that the neighbor can access and misuse the information available in your network systems. Your wireless network might also be potentially attacked by the neighbor. Also, the chances of preventing this become less as it is not possible to keep track of who has logged in to your Wi-Fi network. Hence, network security keys prove to be beneficial in these circumstances.
Targeted Network Attacks
Targeted network attacks are also known as ‘Wardriving’. It simply means shortlisting the most weak-security Wi-Fi networks available in close range, targeting them, and attacking the network systems. Wardriving is done with the sole motive of attacking the target’s network system and compromising the information and data available on other users’ systems connected to the same network.
Evil Twin Attack
Evil Twin Attacks refer to those attacks where the hacker poses as a legit network to dupe users into trusting and logging in to the network system. For example- A hacker can pose as the Wi-Fi network of a shopping mall, wherein the shoppers entering the mall would take it as the shopping mall’s Wi-Fi network and log into the same. These users can now become prone to cyber-attacks and may end up compromising their data.
Get our Ethical Hacking course now to become a certified ethical hacker.
Career Transition
Advantages of Using Network Security Keys
Using network security keys offers several benefits to its users. We have discussed some of the important ones below:
Prevention of Hacker entry
Many users enable Firewalls, Anti-viruses, etc. for system security. But, any cyber security system is incomplete without a Network Security key in place. It offers a best-in-class encryption facility to keep out hackers and deny unauthorized entry to unintended users.
Online Data protection
In this era of digitalization, the protection of online data is very crucial. But the chances of broken or disrupted connections are always there. Attackers can take advantage of the sudden connection disruptions and get unauthorized access to the network system. However, if there is a network security key associated with the network, hackers or attackers will not be able to utilize the disrupted or broken connections. It is thus always advisable to put network security keys into regular usage.
Layered Security
Network security keys act as an extra layer of security for your network and the connected systems associated with the same. A majority of cyber threats are wiped off at the entry-level of the network. If your network is high security, your systems along with the stored data will be secured enough.
Check out our Cyber Security tutorial to learn more about Cyber Security from scratch.
Types of Network Security Keys
There are different types of network security keys based on various categories. But the main broad types of network security keys are as follows:
- WPA (Wi-Fi Protected Access)
- WEP (Wired Equivalent Privacy)
- WPA2 (Wi-Fi Protected Access 2)
WPA (Wi-Fi Protected Access)
Encryption and authentication are the two key functions of the WPA network security key. WPA network security key allows encryption of the user’s information and data. WPA also helps in ensuring extra security by checking if the network security key has been modified. It also helps the network owner to decide which users to allow entry by verifying the users. WPAs are also user-friendly as they can work with almost all types of wireless network adaptors.
WEP (Wired Equivalent Privacy)
Wi-Fi-enabled devices work on a set or a single password. This password or passcode is known as the WEP. The main objective of WEPs is to ensure that the wireless network has a security level matching that of a wired network. However, WEPs have been discontinued since 2004 but are still preferred by many users due to their compatibility with older network adaptors. Post introduction of WPA, WEPs were surrendered as they are the least secured amongst all network key types and are vulnerable to cyber-attacks.
WPA2 (Wi-Fi Protected Access 2)
WPA 2 is by far the most secure among all network security key types. There have hardly been any vulnerabilities detected in WPA 2 in cases of personal Wi-Fi and home-level users. Little or fewer vulnerabilities may still exist at an enterprise level.
Creating a Strong Password
Having a network security key enabled is a good security practice. But it is also important to have a strong network security key that is hard to crack by hackers. The following points need to be kept in mind to keep a strong password:
- A longer password is harder to crack as it takes more time and is difficult to guess. The minimum recommended character length is 12 characters
- Usually, a combination of numerics, alphabets, and special characters is an ideal password.
- The next thing that needs to be kept in mind is to never repeat the same password.
- It is also recommended not to use an easy-to-guess password. For example- ‘Tom@123’ or ‘123456’.
Courses you may like
Are Passwords and Network Security Key the same?
This is one of the most common doubts when it comes to network security keys. In general, both are the different terminologies assigned to the same thing. But network security keys are usually used in network routers or modems etc. It is a more network-oriented password. On the other hand, passwords are used in mobile devices, account logins, etc. However, the majority of Wi-Fi networks also ask for passwords. So basically, the terms ‘password’ and ‘network security key’ are used simultaneously and their usage depends on the maker of the device and its kind.
Conclusion
We hope by now you have a good understanding of what the ‘Network Security Key’ is and why it is important. This blog is also an initiative to urge more and more people to use network security keys and leverage their benefits. This small daily habit can help you prevent many cyber-attacks at their very inception. In this blog, we also learned about what are the characteristics of a perfect network security key. Cyber attacks are getting sophisticated and so should our efforts to fight them. We hope this blog might be of some use to our readers in safeguarding their systems and networks.
Checkout our Ethical Hacking tutorial to learn more about ethical hacking.
The post What is a Network Security Key? appeared first on Intellipaat Blog.
Blog: Intellipaat - Blog
Leave a Comment
You must be logged in to post a comment.