What is a Firewall?
Let’s look further in this blog and review the Firewall, its history, its working of Firewall, Firewall advantages, and disadvantages, and many more exciting insights.
Firewall Definition
Similar to a security guard, a firewall screens and investigates connections to and from your computer or network in accordance with a predetermined set of rules. While every computer has the most fundamental firewall security.
The topics we’ll be covering in this blog are:
- What is Firewall?
- History of Firewall
- Why Firewall is Required?
- Types of Firewall
- How does a Firewall Work?
- Advantages of Firewall
- Limitation of Firewall
- How to use Firewall Protection?
- Conclusion
Check out the Video for the Product Management Course
What is Firewall?
A firewall is a type of security system that keeps track of and manages network traffic in accordance with a set of security guidelines. Typically, firewalls are placed between a trusted network and an untrusted network, which is frequently the Internet. For instance, office networks frequently utilize firewalls to safeguard their networks from threats from the internet.

Firewalls make the decision of whether to permit incoming and outgoing traffic to pass. They may be incorporated into the software, hardware, or both. The practice of constructing barriers between or through the midst of buildings with the goal to contain a fire is where the term “firewall” originally originates. Network firewalls function similarly to stop internet attacks.
In a private network, firewalls operate as gated borders or gateways to control the flow of authorized and unauthorized web activity. The phrase refers to physical barriers that act as barriers against the spread of fire until emergency personnel can put it out. Similar to web traffic management, network security firewalls are often used to stop the spread of online dangers.
Firewalls provide “choke points” to direct web traffic, where it is examined based on a set of predetermined specifications and handled appropriately.
History of Firewall
It is best to think of the development of the firewall as ongoing. This is due to the fact that it has undergone continuous evolution and that numerous ‘creators’ have contributed to its growth and development.
Before it became the product that served as the foundation for all contemporary firewalls, each of its designers expanded on various firewall-related components and versions between the late 1980s and the mid-1990s.
At Digital Equipment Corp (DEC), Mogul, Reid, and Vixie all played important roles in the development of packet-filtering technologies that would later be useful in firewalls. The idea of screening external connections before they connect to computers on an inside network resulted from this.
The early concept of the circuit-level gateway firewall was investigated and created by numerous AT&T Bell Labs employees between the late 1980s and the early 1990s. This was the first firewall that checked connections continuously rather than re-authorizing after every data packet.
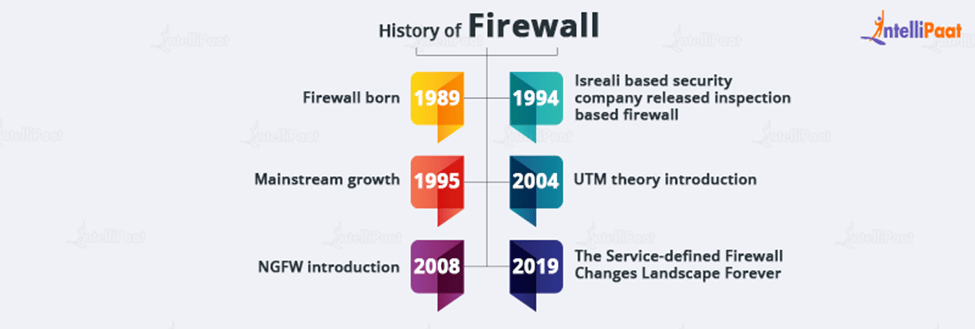
Gil Shwed, the creator of Check Point, and Nir Zuk, a talented engineer, contributed significantly to the creation of Firewall-1, the first widely used, user-friendly firewall software, between 1993 and 1994. Following this was Nir Zuk’s work on an intuitive graphical user interface for 1994’s Firewall-1, which was crucial in the longer-term adoption of firewalls into homes and enterprises.
These innovations played a crucial role in the creation of the firewall product we are familiar with today, and many cyber security solutions make use of each in one way or another.
Why Firewall is Required?
Networking lacking protection is exposed to any traffic attempting to get into your systems. Network traffic, whether harmful or not, should always be monitored.
A wide range of advantageous opportunities become available when connecting personal computers to other IT systems or the internet. Facilitate online and security technology can be sacrificed in exchange for uncomplicated collaboration, sharing of resources, and enhanced creativity. Users run the danger of becoming the victims of malware, online fraud, identity theft, and hacking if they connected their machines to a network or to the internet.
Once a bad actor learns about your network and devices, they can quickly find them, access them, and expose them to ongoing risks. 24/7 internet connectivity increases this risk because your network can be accessed at any time.
The filtering of content is another function of firewalls. For instance, a school can set up a firewall to block individuals from accessing adult content on their network. Similar to this, in certain countries the government maintains a firewall that can bar residents from accessing specific areas of the Internet.
Are you interested? Check out Intellipaat’s Ethical Hacking Training Certification Course and enroll now!
Types of Firewall
- Stateful firewalls
A “stateful” application in computer science is one that stores information from earlier interactions and occurrences. Instead of analyzing every packet, a stateful firewall stores information about open connections and uses this knowledge to evaluate incoming and outgoing traffic.
Stateful firewalls make decisions by heavily relying on context. For instance, if a connection’s outgoing packets require a specific type of response, the firewall will only permit incoming packets on that connection provided they also include the desired response.
- Firewall-as-a-service (FWaaS)
The more recent paradigm for providing firewall capabilities through the cloud is firewall-as-a-service (FWaaS). Another name for this service is “cloud firewall.”
Similar to how conventional firewalls enclose an organization’s internal network, FWaaS creates a virtual wall around cloud platforms, infrastructure, and applications. FWaaS is frequently more effective than traditional firewalls at securing cloud and multi-cloud assets.
- Web application firewalls (WAF)
WAFs, assist protect online applications from dangerous users, whereas conventional firewalls protect private networks from harmful web apps. By filtering and observing HTTP traffic between a web application and the Internet, a WAF aids in the protection of web applications.
It typically guards against attacks like cross-site scripting (XSS), file inclusion, SQL injection, and cross-site forgery, among others.
- Next-generation firewalls (NGFW)
NGFWs are firewalls that combine traditional firewall functionality with a number of extra features to combat threats at various OSI model layers.
NGFWs examine packets significantly more thoroughly than conventional firewalls do. Deep inspection can examine packet payloads and the applications that the packets are accessing, among other things. This enables the firewall to implement filtering rules with greater specificity.
- Proxy-based firewalls
These intermediaries* between clients and servers are proxies. Clients connect to the firewall, which inspects the outgoing packets before establishing a connection with the target (the web server).
The firewall will also intercept a request from the web server trying to send a response to the client, inspect the packets, and then relay the response through a different connection to the client. Effectively preventing a direct connection between the client and server is a proxy-based firewall.
Career Transition
How does a Firewall Work?
A firewall determines which internet traffic is trustworthy enough to pass through it and which traffic is not. But just before diving into more detail, we must first comprehend how a firewall performs to filter among web-based networks.
Firewall rules are designed to safeguard secure connections and the endpoint gadgets that make up those networks. Hosts are electronic devices that can interact with other hosts through some kind of network. They communicate both inbound and outbound between internal networks as well as with external networks.
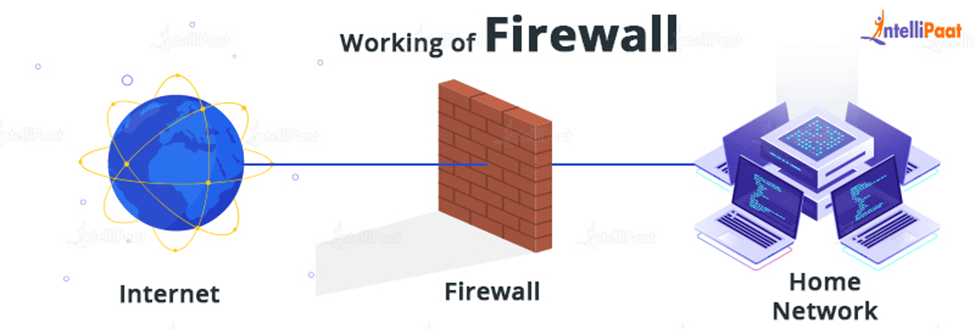
Networks are used by your computers and other endpoint devices to connect to the internet and one another. To ensure privacy and security, the internet is divided into sub-networks, or “subnets.”
Host firewalls can be customized to meet the needs of each computer, unlike network firewalls, which need to be set against a wide range of connections. Network-based firewalls are appropriate for a sweeping control solution because host firewalls are more difficult to adjust. But for a multi-layer security system, using both firewalls concurrently in both locations is excellent.
Go through these Ethical Hacking Interview Questions and Answers to excel in your interview.
Here comes the basic difference between Firewall and Antivirus:
Difference between Firewall and Antivirus
| Firewall | Antivirus |
| A firewall is a protection system that can be either software-only or hardware-based, and it is intended to guard computer networks and systems from destructive breaches. | A system is shielded by antivirus software from domestic attacks like viruses, trojan horses, spyware, and other malware. |
| Due to the fact that it scans all incoming data packets for information that could be dangerous, a firewall is also known as a “packet filter.” | The computer system is scanned for weaknesses by antivirus software, which subsequently makes the required corrections to fortify the system’s defenses against assault. |
| The main responsibility of a firewall is to monitor network traffic and keep out unauthorized users. | An antivirus’s main job is to find, monitor, pinpoint, stop, and eliminate any existential threat to the computer system. |
| A firewall provides network protocol-level security against unauthorized intrusion. | A simple antivirus scan will look for any potentially harmful software, such as Trojan horses, worms, and viruses. |
| The inability of a firewall to stop internal attacks or attacks that elude its network coverage is one of its shortcomings. | The limitation of antivirus software’s inability to examine read-only files is negative. |
Advantages of Firewall
- Computers are protected from viruses, malware, and other destructive codes by firewalls. Additionally, if the computer is protected by a firewall, the user can carry out their office tasks in a secure manner.
- Given that the majority of threats occur through virtual traffic, it is one of the most important benefits of firewalls. Consequently, if you have firewalls installed on your device. If so, it will continue to run in the background and examine all communications.
- Even if you lack technological expertise, you may still install firewalls on your computer. Additionally, no expert assistance is required for deploying the firewalls.
- While online, a user expects total privacy, yet certain unforeseen circumstances may make them uncomfortable with this expectation. As a result, if they employ firewalls in that situation, it will ensure that their high level of privacy is maintained.
- Some hackers get unauthorized access to users’ computers in order to engage in unlawful activity. They continue seeking for devices to break into in order to get private information like credit card numbers.
This Ethical Hacking Tutorial will help you learn Ethical Hacking from scratch.
Limitations of Firewall
- For their customers, firewalls also have a number of drawbacks, with cost being one of them. For businesses, purchasing firewalls can be expensive because they need payment.
- Several websites with viruses or malware are blocked by the firewall. Although this item may benefit its users, it frequently causes issues for huge businesses.
- The security tools that remain active in the background of the computer are firewalls. Additionally, the computer’s performance will be poor because there are several tabs open and the firewall is on.
- You should install the anti-virus software if your machine already has a firewall installed. In order to execute the malware detection test and get rid of all these viruses and malware.
- Despite the fact that nowadays small businesses feel comfortable purchasing firewalls for their computer hardware. However, many large firms require a specialized staff of IT professionals who can handle all firewall maintenance tasks.
Courses you may like
How to Use Firewall Protection?
Make sure your firewall is configured and maintained properly to keep your network and devices secure. Here are some pointers to help you strengthen the security of your firewall:
- Update your firewalls frequently as soon as you can: Your firewall is updated against any recently disclosed weaknesses courtesy of firmware patches.
- Use antivirus protection: To protect your system from viruses and other infections, you need also use antivirus software in addition to firewalls.
- Limit the host and ports that are open; restrict all incoming and outgoing connections to a narrow whitelist of reliable IP addresses.
Conclusion
In this blog, You now know what a firewall is and how it functions as a result of this course. Additionally, you learned about the many kinds of firewalls and how to operate one. Furthermore, we tried to explain the history and the difference between firewall and antivirus. In the modern era, cybersecurity is a booming industry. If you want to learn ethical hacking to defend networks and devices from hackers then you are in the right place.
For more information on Ethical hacking, visit our Ethical Hacking Community
The post What is a Firewall? appeared first on Intellipaat Blog.
Blog: Intellipaat - Blog
Leave a Comment
You must be logged in to post a comment.













