What Data Do I Need to Fight Application Fraud?
Blog: Enterprise Decision Management Blog

In previous blogs, we’ve defined application fraud, explored the role of hackers and cyber terrorists in perpetrating fraud, and the reflected on the importance of establishing a fraud risk appetite. A key takeaway from all of these posts is that to strengthen defenses across the enterprise, we must improve synergies between data, technology and analytics. When it comes to application fraud, our framework must seamlessly bridge intelligence across the customer lifecycle to enable smarter decisioning.
That brings me to the topic that comes up in every application fraud conversation: data. While the value of data may seem self-evident — particularly with the global investments in digital transformation strategies leading to faster, more faceless decisions — one question inevitably surfaces: What kind of data do I actually need?
Data from Inside and Outside
It’s raining data left and right, and reaping the benefits of this data downpour requires understanding what information you already have at your fingertips and where there are gaps.
Financial institutions often underplay the usefulness of their own data assets, or, in some cases are unaware of powerful data assets that reside within other functions of their own organization, including Compliance, Risk and even Marketing.
Vendors also play a critical role in the data landscape, providing innovative solutions that are derived from cross-industry experiences (not just your institution) and with roadmaps that evolve over time to meet changing market needs. With the digitization boom, the number of relevant data assets continues to rapidly expand, with examples include device profiling, email reputation, biometrics – whether behavioral or physical – and more.
These technologies are subject to breach as well, however. For example, in China, we’ve seen fraudsters already exploit “selfie with your driver’s license” controls that leverage facial recognition (comparing the selfie to the driver’s license photo) and optical character recognition (reading the driver’s license information to compare to the supplied application data). To that end, a new level of physical biometrics is being explored that includes movement analysis in video sources. We anticipate that leveraging this type of personal data will spark an interesting privacy and regulatory debate in the years to come.
Your Data Checklist
What are the key data elements you should be considering in your application fraud detection ecosystem? The following list designed to help you inventory:
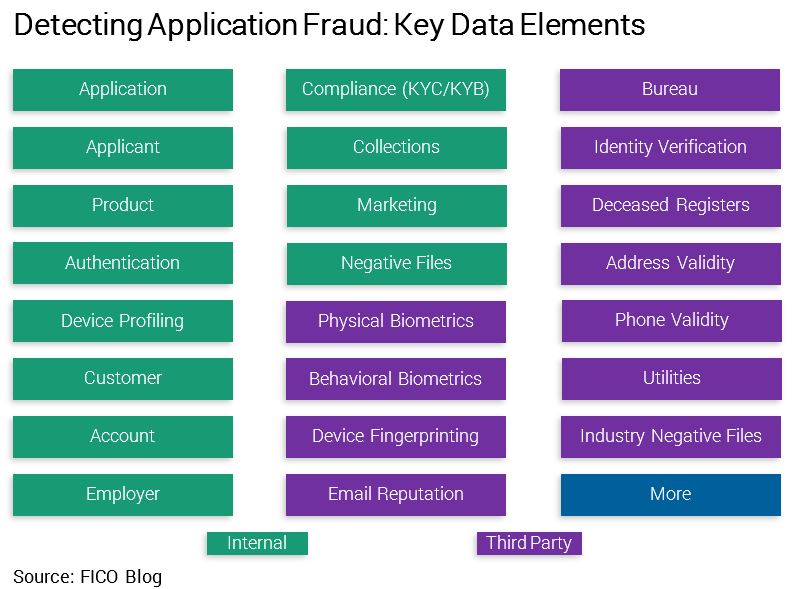
One important factor to bear in mind is that no matter how smart this data is, the utility will be limited if any data source is used in isolation. Rather than evaluating data via point-in-process solutions — e.g., the applicant’s physical biometrics passed checks, now how about their email reputation — an integrated decision across all of your data elements provides the optimal ROI to create an informed decision.
Consult Your Data Strategy
Before you run out to buy data missing from your list, consider this: You have to balance the value the data adds with the investment in integration efforts adding this data will require. We recommend that prioritizing your data gaps to align with your overall data strategy is critical.
A realistic and robust data strategy requires understanding risk at the channel, product and regional level to help assess not only the viability of data, but also prioritize where there are anticipated or existing vulnerabilities.
The following graphic provides several questions that can guide you in defining your data strategy.
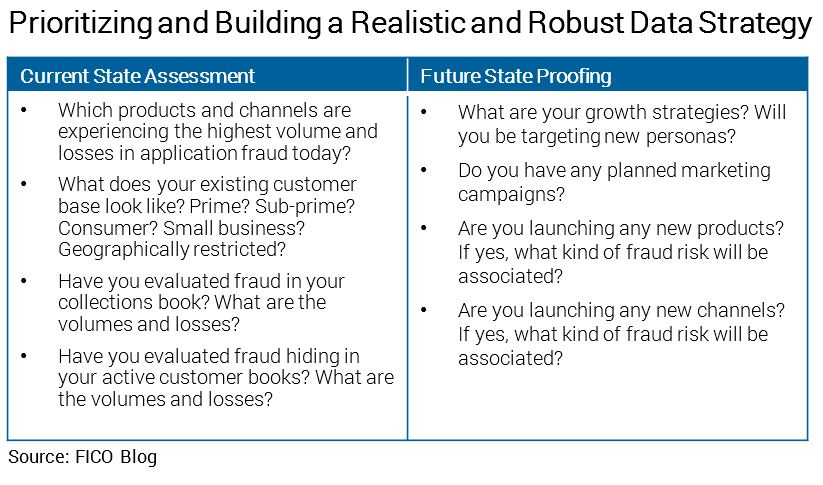
With application fraud on a meteoric rise, financial institutions must take full advantage of the vast amounts of the data available to them. Agility is key to ensure fraud controls are faster and smarter than the bad guys. Implementing a unified data hub that brings together key information from all data sources is critical. Accessed via a single holistic point, centralized data assets can galvanize powerful machine learning analytics.
In fact, machine learning is a topic for one of my upcoming blogs. So stay tuned.
The post What Data Do I Need to Fight Application Fraud? appeared first on FICO.
Leave a Comment
You must be logged in to post a comment.







