Security in Low-Code Applications: Cybersecurity Features and Best Practices for the Joget Open Source Platform
Blog: Joget Unplugged
Introduction to Security Benefits and Risks in Low-Code Platforms
As digitalization becomes increasingly prevalent, low-code platforms are rapidly gaining adoption across industries. Employing visual techniques to programming, they enable the development and delivery of applications in a fraction of the time required by traditional coding. According to Forrester’s Now Tech: General-Purpose Low-Code Development Platforms, Q1 2021, low-code platforms are “vital to digital business” and “proven in even the most mission-critical use cases”.
However, the proliferation of apps and digital solutions bring with it increased cybersecurity risks like phishing attempts and ransomware attacks. As the SolarWinds hack in 2020 and Microsoft Exchange hack in 2021 demonstrated, the cost of security lapses can be monumental. Security considerations are therefore paramount, so how would they apply to low-code platforms?
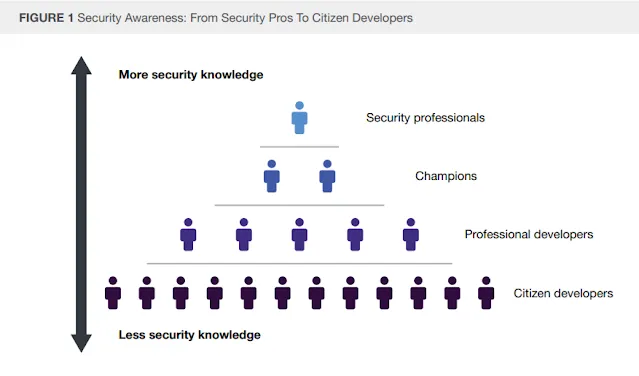 |
| Source: Don’t Ignore Security In Low-Code Development, Forrester Research Inc, 23rd Dec 2020 |
In the Forrester report Don’t Ignore Security In Low-Code Development, several findings were presented:
- Low-code platforms empower business users, called citizen developers, who are likely to be less aware or trained in application security. This increases the number of people with potential access to sensitive data, or to introduce security vulnerabilities.
- However, low-code applications can be more secure compared to those built with traditional coding methods. This is due to the fact that low-code platforms typically provide built-in security controls and can automatically mitigate risks around common security issues like SQL injection or cross-site scripting (XSS). However, additional risks may be introduced with custom code so these need to be managed.
- Low-code platforms provide a multitude of security controls and practices, so organizations must understand and implement policies and processes to address security requirements, both at the platform and application level.
In an article from IDG titled 4 security concerns for low-code and no-code development, several security concerns were highlighted:
- Lack of visibility on what citizen developers are actually developing. This is related to shadow IT, where IT may lose track of applications being built and deployed within the organization.
- No data oversight, in terms of not putting in proper access controls or protecting access to sensitive data. When connecting to data sources, appropriate security controls may not have been put in place to ensure proper sharing of data.
- No auditing of vendor systems, where organizations may not have access to the security audits and compliance that are already in place in the low-code platforms.
- Business logic problems that expose data, when using custom code that does not enforce secure access to sensitive data. Organizations might not apply adequate security training and testing to custom code, which might introduce security risks.
Fundamentally, we can see that low-code platforms provide both security benefits, and risks, to organizations so it is important to understand and implement the appropriate security controls and policies based on the chosen platform.
How to Address Low-Code Security Risks with Joget Cybersecurity Features and Best Practices
As a leading open source low-code platform, Joget recognizes the critical importance of application security and offers many built-in security safeguards and controls.
#1 Platform Security Audits and Compliance
The core Joget platform is fully open source and publicly available for scrutiny. Open source offers much greater transparency compared to fully proprietary solutions, and allows visibility into the source code and inner workings of the platform.
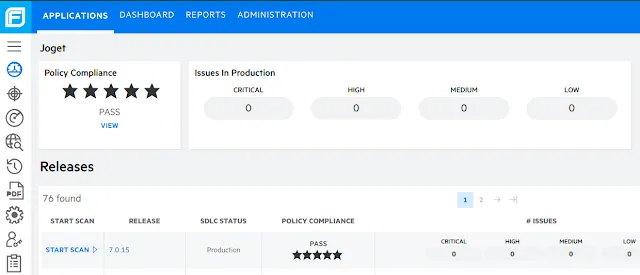
Each commercial version of the Joget platform is continually audited with Micro Focus Fortify On Demand static application security scans (SAST) to ensure a 5-star rating before every release. Micro Focus is a multi-year leader in the Gartner Magic Quadrant for Application Security Testing, and is compliant with many security standards including FISMA, PCI 3.2, DISA STIG 4.3. This helps to ensure that critical security concerns like the OWASP Top 10 are taken care of at the platform level.
Best Practice: Leverage commercially supported platform editions that have undergone security hardening and audit. Ensure that the platform is deployed in a secure environment, because if the underlying IT infrastructure is insecure, then the entire system will be vulnerable.
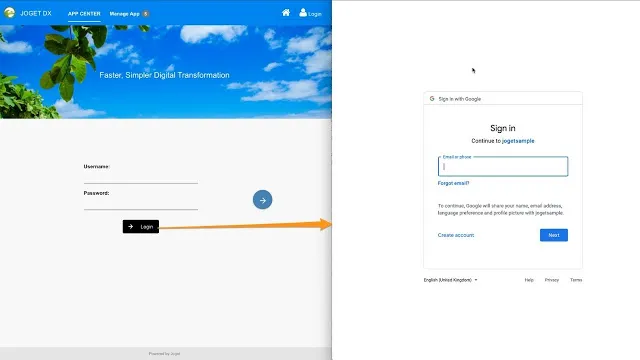
#2 Authentication and Single Sign-On
Joget supports the most popular single sign-on (SSO) authentication standards such as OpenID Connect, SAML, LDAP and Kerberos, as well as custom authentication implementations. By allowing users to access multiple applications by using a single login, SSO simplifies identity management, reduces security risks and helps with regulatory compliance.
For additional authentication security, Joget provides a Security Enhanced Directory Manager that offers more secure credentials management, password storage and policies. Multi-factor authentication (MFA) is also available, with the industry standard Time-based One-Time Password (TOTP) algorithm supported out-of-the-box.
Best Practice: Enable security enhanced directory features, multi-factor authentication (MFA) and/or single sign-on (SSO) in production environments.
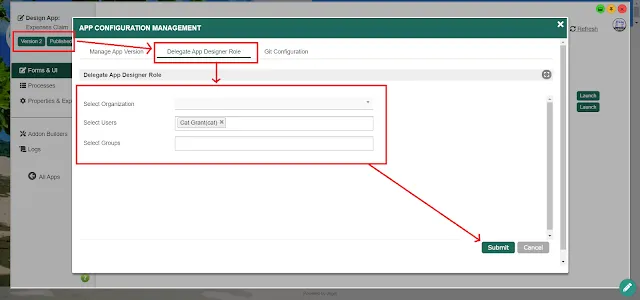
#3 Platform Access Control
To mitigate the problem of shadow IT and lack of visibility, Joget allows organizations to delegate app development to specific users or groups by assigning App Designer roles. By having a centralized platform with delegated citizen developers, IT will be able to not only oversee the development of apps, but also collaboratively develop them.
This approach can be further expanded to disparate departments or business units in the deployment of the Joget platform itself, through multi-tenant support in the Joget Cloud Edition, or by utilizing namespaces and projects in cloud-native Kubernetes environments like Red Hat OpenShift or Google Kubernetes Engine.
Best Practice: For large-scale enterprise environments, centralize the deployment of the platform in a cloud-native or multi-tenant deployment, and utilize app designer delegation for IT visibility and governance.
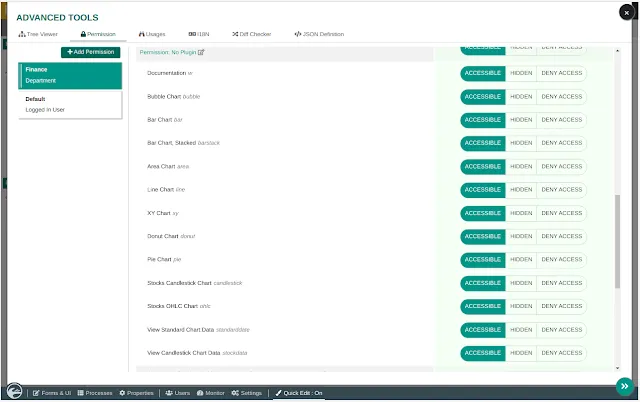
#4 Application Access Control and Audits
For applications built on the Joget platform, there are a multitude of fine-grained role-based access controls (RBAC) available. Depending on requirements, permission controls can be defined to protect the entire app UI (userview), a category, a page, a form or even a form section. For process automation, access controls are mapped to participants in the workflow to ensure appropriate and secure user task assignments.
For security, audit trails are an important record of system activity to help detect potential security violations and flaws. During development, Joget offers Git integration so all application changes are automatically captured and tracked to be audited. At runtime, application audit trails are also automatically captured.
Best Practice: Utilize fine-grained permission and access controls when designing applications and processes. Take advantage of Git integration and audit trails for development and runtime security monitoring.
#5 Secure Code Using Plugins
One of the strengths of the Joget platform is its flexible plugin architecture, where plugins can be developed by professional developers to extend the platform in whichever way desired. By utilizing plugins instead of custom scripting or ad-hoc code, Joget allows security-aware professional developers to develop secure components to be used by citizen developers. These plugins can be developed in-house, or published and installed from the Joget Marketplace.
Best Practice: Where appropriate, use pre-built plugins or engage security-aware professional developers to develop reusable and secure plugins that can be used by citizen developers. The custom plugins should be subjected to security reviews before release.
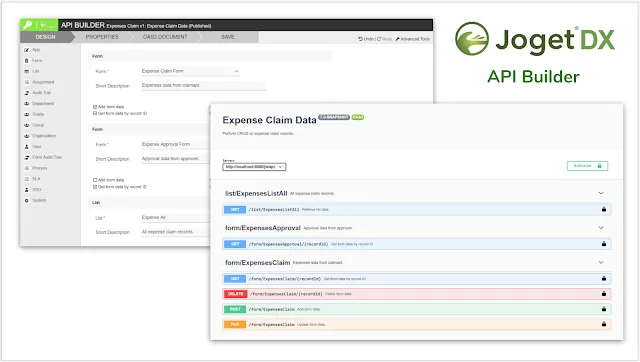
#6 Secure API Endpoints
Application Programming Interfaces (APIs) are an important part of modern application architecture, facilitating the use of microservices and composable business applications to compose solutions from smaller components. Joget provides built-in JSON APIs, as well as a more advanced API Builder that offers a visual drag-and-drop approach to expose application data via OpenAPI (formerly known as Swagger) compliant APIs. Most importantly, these APIs are secure by default, and the API Builder additionally offers simple and extensible customized configuration for secure authentication.
Best Practice: When developing applications as smaller composable components to be composed into larger solutions, make sure to secure the APIs with appropriate access controls.
Conclusion
Modern low-code platforms offer proven advantages for organizations undergoing rapid digital transformation in these uncertain times. The Joget platform specifically offers many security features and controls, and it is essential for an organization to fully harness these features to suit its unique environment.
Get Started
Resources to get started developing low-code apps with Joget:
- Get Started - On-premise, on-demand, public/private cloud, cloud native, and more.
- Joget DX Video Tutorials - Quick overview and build your first app.
- Joget DX Knowledge Base - User and developer reference, samples and other documentation.
- Community Q&A - Ask questions, get answers, and help others.
- Language Translations - Translations for more than 20 languages.
- Joget Academy - Self-paced online learning and certification.
- Joget Marketplace - Download ready made apps, plugins, templates and more.
- Joget Events - Upcoming and past Joget events & webinars.
- Joget Press - Joget press releases.
- Joget Reviews - Joget reviews and customer testimonials.
Follow us for the latest news and updates: