PSD2 Strong Customer Authentication – 3 Reasons to Include SMS
Blog: Enterprise Decision Management Blog

Over the past few weeks, I’ve seen several articles and seen and heard many comments that are positively crowing about the demise of SMS as a factor for PSD2 Strong Customer Authentication. While the issues suffered by Metro Bank clearly show there are legitimate concerns, it would be wrong to announce the passing of SMS as an authentication tool for PSD2. Here are 3 reasons why it still needs to be part of your SCA strategy
1 It Is a Permissible Authentication Method for PSD2
The European Banking Authority (EBA) have not ruled out the use of SMS as an authentication method. They rightly call out that payment service providers must adopt measures to mitigate the risk of unauthorised parties using the elements of Strong Customer Authentication categorized as possession. As point 3 will show, it is feasible to mitigate the risk inherent in using SMS.
The UK’s FCA arguably went one step further, issuing a policy statement on the final PSD2 Regulatory Technical Standard under the revised PSD2, on 18th December 2018 (PS18/24). In this they state: “A one-time password sent via SMS may be used to validate possession of the SIM card associated with a customer’s mobile phone number.
Another anti-SMS argument I have seen is that dynamic linking required by PSD2 cannot easily happen. Dynamic linking means that customers must be able to make the connection between the authentication they are carrying out and the transaction they wish to complete.
Some argue that this cannot be done safely with SMS unless the transaction information is encrypted and included in the SMS message. To do this, consumers would have to undertake the cumbersome task of unencrypting the transaction information before they could complete the SCA.
This is a misconception. The link between transaction and authentication can also be made within the app or secure website the customer is using. As is currently common practice, the interplay between app or website and SMS message is clearly established and meets the PSD2 standards for dynamic linking.
2. Customers Prefer It
We recently commissioned a survey across four European countries that looked at consumer preferences around authentication methods. We asked respondents which method they would prefer if they are making an online payment and their bank needs to make an additional security check. In general, the survey results show that to satisfy customer experience, PSPs should offer a range of authentication methods.
However, looking at a league table of authentication methods, a passcode sent to a mobile phone by text message was the clear ‘winner’ in every country surveyed.
Percentage by surveyed country where customers prefer authentication with a passcode sent to their mobile:

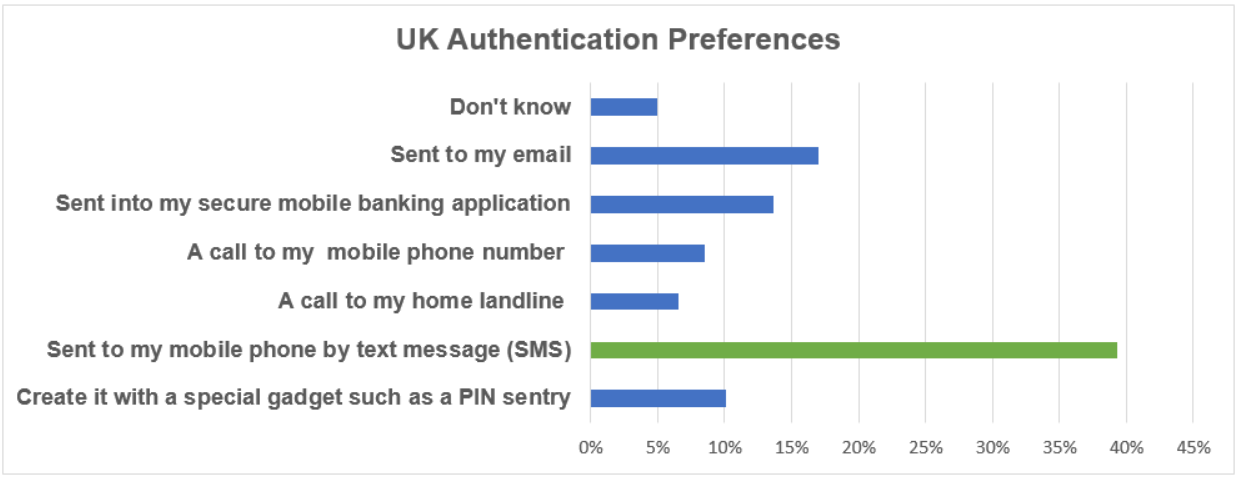
3. You Can Mitigate its Weaknesses
There are security weaknesses in the use of SMS as an authentication method, primarily a matter of the telephony signalling protocol (SS7). SS7 allows network providers to transfer data between themselves and is widely used for legitimate purposes. Unfortunately, the age and necessary open nature of the protocol means that it is vulnerable to use by fraudsters posing as a network provider through a legitimate MNO. They can then divert calls and messages to a mobile phone of their choice.
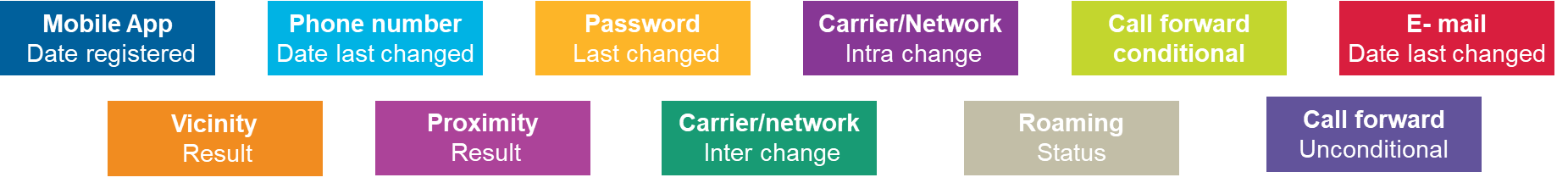
This means that presuming an SMS has been delivered to your legitimate customer is a mistake. However, it is possible to accurately prevent an SMS being intercepted and ensure it has gone to its intended recipient by performing a risk analysis on associated data. By assessing data from the mobile, the network provider and the behaviour of the customer, you can identify, in real time, cases that are suspicious and divert those transactions to other authentication methods.
Factors used to check for suspicious behaviour prior to issuing an authentication communication include:
Ultimately, we need diversity and choice in the methods used for PSD2 SCA, and it is difficult to see how that can happen if SMS is excluded as an authentication factor. While there are alternative authentication methods that many would argue are more secure, they do not offer the advantages that SMS has in terms of ubiquity with PSPs and acceptance by consumers.
How FICO Helps
FICO provides an open Strong Customer Authentication platform that uses AI and machine learning to deliver the best authentication options for each customer journey. FICO Customer Communications for Strong Customer Authentication uses data from all available solutions including those based on network data, biometrics, device intelligence and client data to make robust decisions about the authentication needed and to execute it.
For more information:
- Read about our solution for Strong Customer Authentication
- Read our white paper ‘Why Minimal Compliance Will Cost PSPs More’
The post PSD2 Strong Customer Authentication – 3 Reasons to Include SMS appeared first on FICO.
Leave a Comment
You must be logged in to post a comment.








