OWASP: Top 10 Security Risks and Vulnerabilities
Let us take a look at what is covered in this blog:
Have a look at this video in which our Cyber Security specialists go over every detail of the SQL injection attacks.
What is OWASP?
OWASP is an association devised for the assurance of the web. OWASP promotes software security, integrity, prioritization, and minimizes risks in applications. Several application security firms and industry specialists provide input to recognize the top, most critical security risks that threaten web applications.
OWASP is a community of developers, technologists, and evangelists improving the security of software through tools and resources. OWASP has 100+ active projects and applications that are submitted weekly.
The projects are open source and are built by a community of volunteers.
OWASP primarily focuses on the back end rather than design issues. OWASP is a nonprofit security organization that conducts security assessments and gives insights into critical security flaws in software.
OWASP Tools
OWASP ZAP is an abbreviation for the Open Web Application Security Project. The Zed Attack Proxy (ZAP) is a simple integrated vulnerability scanning tool for detecting flaws in web-based applications.
What is OWASP Top 10?
The OWASP top 10 is a constantly updated document that outlines web application security concerns, focusing on the 10 most significant issues. OWASP has many different projects under its umbrella, one of which is the Top 10 Projects. The goal of the Top 10 Projects is to raise awareness about application security by identifying some of the most critical risks facing organizations. The OWASP Top 10 vulnerabilities reflect widespread agreement on the most severe web security deficiencies.
Enroll in our Ethical Hacking course now to become a certified ethical hacker now!
The Top 10 OWASP Vulnerabilities in 2021
The OWASP top 10 vulnerabilities are listed below in order of severeness:
Injection
According to OWASP, SQL, OS, and LDAP injection flaws happen when untrusted data is sent to an interpreter as part of a command or query. The attacker’s hostile data can trick the interpreter into executing unintended commands or accessing data without proper authorization.
Injection attacks meddle the fundamental security concept of access control. So, access control states that each role or user should have definite access to certain system functions and data. The injection is not specific to a technology or programming language.
A malicious user can tinker with the search feature in the hope of injecting an input called payload to perform unintended results by the vulnerable system. If successful, the malicious user can trick the application to revert sensitive information.
Injection Vulnerabilities:
- SQL injection
- OS command injection
- Lightweight directory access protocol (LDAP) injection
Preventing Injection Attacks:
- Use a secure interface that does not require the use of an intermediary
- Utilize server-side user authentication that is white-listed
- Special characters should be approached with caution
- To avoid additional disclaimer of documents on the occasion of SQL injection, use the LIMIT command
Broken Authentication
Authentication is a process where a user grants the genuinity of who they are. An attacker can mimic someone and gain access to their data or functionality. Authentication and session involve cookies that provide an easy way for an attacker to try and portray someone else.
As per the OWASP top 10 list, application functionalities linked to authentication and session management are frequently implemented improperly, allowing intruders to compromise passwords, keys, or session tokens or exploit other implementation defects to temporarily or permanently assume other users’ identities.
Broken Authentication:
- Compromised credentials such as username and password
Broken Authentication Vulnerabilities:
- Insecure login forms
- Logout management
- Administration portals
- Session ID in URL
Preventing broken authentication attack:
- Use a modern framework that has been heavily used and tested
- Ensure HTTP only and secure flags on cookies
- Use a combination of independent pen testing and code review, if not sure
- Be mindful of your password hashing algorithm and make it updatable
Have a look at Intellipaat’s Cyber Security courses and sign up today!
Sensitive Data Exposure

Many web applications and APIs do not shield psychic data such as financial, healthcare, and PII. Attackers may steal or modify such clumsily-defended data to conduct credit card fraud, identity theft, or other crimes. Sensitive data may be negotiated without extra protection, such as encryption at rest or in transit, and requires special precautions when exchanged with the browser.
Sensitive Data Exposure Vulnerabilities:
- Credential stuffing
- Password-based attacks
Preventing Sensitive Data Exposure:
- PCI, GDPR, and many more security standards provide guidance for such attacks
- Reduce the scope of the blast radius
- Ensure best security practices
XML External Entities
As per the OWASP top 10 list, XML gives you the ability to define new entities such as turn and foo. Normally, these are simple text replacements that are in-lined in XML declarations, but they refer to external files.
XXE attacks take advantage of the ability to read arbitrary files and URIs to allow a wide range of attack scenarios.
Preventing XXE Attacks:
- Reducing[13] [14] XXE attacks is generally straightforward and requires passing additional flags to your XML parser. Generally speaking, these[15] [16] attacks will be flags for disallowing inline DTDs and removing entities entirely.
Have a look at our blog on Ethical Hacking tutorial and learn more about these vulnerabilities!
Broken Access Control
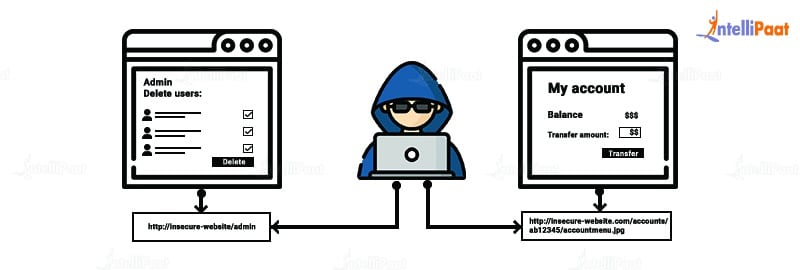
Whenever a hacker exploits access to systems, it is known as breach access control. The attacker can access the computer either as a user or administrator.
As per the OWASP top 10 list, restrictions on what authenticated users are allowed to do are often not enforced. Attackers can exploit these flaws to access unauthorized functionality of data such as access to other users’ accounts, view sensitive files, modify another user’s data, change access rights, etc.
Preventing Broken Access Control Attacks:
- Implement access control; this will lead to user-grown increased complexity
- Manage multiple access profiles and follow the least privileged policy
- Make use of logging and monitoring
- Make sure to have continuous testing of the application launched
Career Transition
Security Misconfiguration
The most prevalent problem in the OWASP top 10 list is security misconfiguration. It is caused by insecure default setup, ad hoc configuration, open cloud storage, incorrect HTTP headers, and verbose error messages revealing sensitive information.
All operating systems, frameworks, libraries, and applications should not only be securely set up but must also be patched or upgraded promptly.
Examples of Security Misconfiguration:
- Open S3 bucket
- Unencrypted database
- Default admin credentials
- Unnecessary ports or services
- Verbose error messages or server version information
Preventing Security Misconfiguration Attacks:
- Hardened system: Use an automated process such as cloud formation
- Patch and update software: Prioritize patches and implement their impact. Subscribe to vendor update
Cross-site Scripting (XSS)
As per the OWASP top 10 list, XSS is a code injection attack that is executed on the client-side of the web application. In this OWASP attack, the attacker injects malicious script through the web browser. The malicious script is executed when the victim visits the web page or web server.
Cross-site scripting is utilized to steal sensitive information such as cookies, session tokens, and other private data.
Preventing cross-site scripting attacks:
- Escape the user input
- Consider all input as a threat
- Data validation
- Sanitize data
Insecure Deserialization
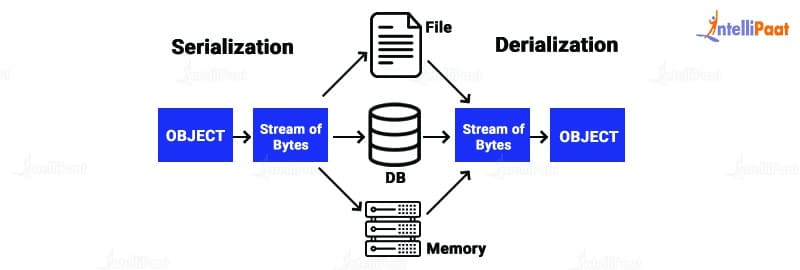
As per OWASP top 10 list, insecure deserialization frequently results in remote code execution. Even though deserialization vulnerabilities do not allow for remote code execution, they can be leveraged to launch attacks such as replay attacks, injection attacks, and privilege escalation attacks.
An unsafe deserialization vulnerability occurs when a program fails to sufficiently secure this procedure. If a deserialization implementation’s default parameters are utilized, an application may have little control over what data is deserialized. In the worst-case scenario, any incoming serialized visual data may be included with no authentication or safeguards.
Preventing Insecure Deserialization Vulnerability:
- Prevent data from tampering while the objects are getting serialized
- Log to detect insecure deserialization
- Code isolation
Courses you may like
Using Components with Known Vulnerabilities
As per the OWASP top 10 list, it is typical for online services to contain components that have known security flaws. The known vulnerability component might be the component itself, the CMS utilized, the webserver, a plugin loaded, or even the library used by one of these libraries.
Libraries, frameworks, and other software modules are nearly always executed with full rights. An attack that takes advantage of a weak component might result in significant data loss or server takeover. Applications that use components with known vulnerabilities may bypass application protections and enable a variety of potential attacks and consequences.
Preventing Using Components with Known Vulnerabilities:
- In the event that patches cannot be addressed, maintain a continuous inventory and monitor the OWASP dependency check.
- Deserialization issues can be detected by using application security tools. Penetration testing can be done to confirm that the issues exist.
Insufficient Logging and Monitoring
As per the OWASP top 10 list, inadequate logging and monitoring is a problem that affects the underlying infrastructure and not only the computer HTTP server. As a result, we would not confine our analysis to web application logging and monitoring.
Another main issue is a large number of logs—practically all new devices produce unique records. As a result, log handling becomes a huge issue. The sheer volume of information gathering becomes too much to successfully monitor and manage. So, all individual logs are collected together and aggregated.
Preventing Insufficient Logging and Monitoring
- Following the testing process, programmers can examine the testing records to detect potential flaws and vulnerabilities. SAST systems can also aid in the detection of unlogged safety issues.
Preparing for an ethical hacking job interview? Have a look at our blog on ethical hacking interview questions and start preparing!
How to secure Web Applications
Application security is business security and protecting your apps from attack is a highly complex and never-ending job.
Most online applications’ security remains deplorable. Every second resource contains a high-risk vulnerability from the OWASP top 10 list. However, it is obvious that the proportion of online apps with significant vulnerabilities is gradually reducing. The following encouraging trend is that corporations are beginning to pay greater attention to the security of their apps, not just public ones, but also those used for internal purposes.
The number of modern web attacks will decrease if identified vulnerabilities are patched as quickly as possible and operations are streamlined as much as feasible.
Conclusion
A malicious user can tinker with the search feature for injecting the input called payload to perform unintended results by the vulnerable system. The known vulnerability component might be the component itself, the CMS utilized, the webserver, a plugin loaded, or even the library used by one of the libraries. The OWASP top 10 vulnerability list will help organizations to secure their web applications in the most efficient way. The OWASP list throws a brief idea and in-line understanding of security vulnerabilities.
The post OWASP: Top 10 Security Risks and Vulnerabilities appeared first on Intellipaat Blog.
Blog: Intellipaat - Blog
Leave a Comment
You must be logged in to post a comment.