Integrate Oracle Integration with a third party OAuth Protected REST service using the generic REST adapter – Part 2 by Anuj Kaushal
Blog: PaaS Community
In the first part of the series, we provided a brief introduction of oauth and the various security policies available within ICS. We also had a closer look at OAuth Custom Two Legged Flow. In this post, we will look at OAuth Custom Three Legged Flow. The final part in this series provides the sample custom OAuth Security configuration for some of the popular services.
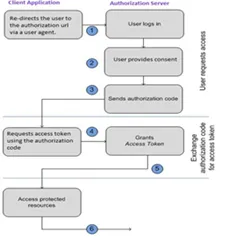
Before we delve into custom 3-legged security policy, it is important to understand the steps performed as part of OAuth Authorization code credentials flow:
Step 1: User specifies the authorization request URI. The user is redirected via the user-agent (browser) to the authorization URI.
Step 2: Resource owner logs in to authenticate and provides consent to the client application to access its resources.
Step 3: The authorization server sends a callback request to the client application and sends the authorization code.
Step 4: The client application extracts the authorization code from the request and uses it to send another request to the authorization server to get an access token. Read the complete article here.
For regular information on Oracle PaaS become a member in the PaaS (Integration & Process) Partner Community please register here.
![]() Blog
Blog ![]() Twitter
Twitter ![]() LinkedIn
LinkedIn ![]() Facebook
Facebook ![]() Wiki
Wiki
Technorati Tags: SOA Community,Oracle SOA,Oracle BPM,OPN,Jürgen Kress