How to Install Kali linux? Installation & Configuration
Although the section below lists the basic system requirements, higher hardware will obviously result in better performance. Ideally, Kali Linux can be used.
Let’s examine this tutorial’s bookmark:
- How to Install Kali Linux
- Installation & Configuration
- Overview of Kali Linux
- Need for Kali Linux
- Installation Steps of Kali Linux
- Wrapping Up
Watch this Tutorial on Kali Linux:
How to Install Kali Linux?
You will first require appropriate computer hardware. Both i386 (x86/32-bit) and amd64 (x86 64/64-bit) processors can run Kali Linux. In most cases, we advise utilizing the amd64 images.
Kali Linux requirements include appropriate computer hardware and other prerequisites for successful installation.
Let’s discuss it further.
Installation & Configuration
In this example, we won’t have any pre-installed operating systems because we’ll be installing Kali Linux in a brand-new guest VM. Throughout the course, we will discuss additional possibilities that might occur.
Installation Prerequisites
- Using the amd64 installer image.
- CD/DVD drive/ USB boot support.
- Single disk to install to.
- Connected to a network(with DHCP & DNS enabled) that has overpower internet access.
System Requirements
What you want to install and your configuration will determine the Kali Linux installation requirements. In terms of system requirements:
- At the very least, you can use as little as 128 MB of RAM (512 MB is suggested) and 2 GB of disc space to install Kali Linux as a fundamental Secure Shell (SSH) server without a desktop.
- On the higher end, you should actually strive for at least 2 GB of RAM and 20 GB of disc space if you choose to install the default Xfce4 desktop and the Kali-Linux-default metapackage.
- At least 8 GB of RAM is advised when utilizing resource-intensive programs like Burp Suite (and even more if it’s a big web app!). or running many programs at once
Overview of Kali Linux
An open-source Linux distribution built on the Debian operating system, Kali Linux (formerly BackTrack Linux), is designed for sophisticated penetration testing and security auditing.
Numerous tools in Kali Linux are geared toward various information security activities, including reverse engineering, computer forensics, penetration testing, and security research. Information security experts and amateurs can use Kali Linux because it is a multi-platform solution that is easily accessible and cost-free.
Around 600 penetration-testing applications (tools) are available in Kali Linux, such as the graphical cyber attack management tool Armitage, the port scanner Nmap, the packet analyzer Wireshark, the password cracker John the Ripper, the automatic SQL injection and database takeover tool sqlmap, the software suite Aircrack-ng for testing wireless LANs, the Burp Suite, the OWASP ZAP web application security scanners, etc.
It was created by Offensive Security employees Mati Aharoni and Devon Kearns through the rewriting of BackTrack, a Linux distribution they had previously used for information security testing and which was based on Knoppix.
The Hindu deity Kali served as the name’s inspiration. The majority of the packages that Kali uses come from the Debian repositories. Kali Linux gained prominence after being mentioned in several areas.
If you are interested please checkout Intellipaat’s Kali Linux Tutorial
Need for Kali Linux
Advanced Penetration Testing and Security Auditing are the main uses of Kali Linux. There are several hundred tools in Kali that are designed for a variety of information security activities, including reverse engineering, computer forensics, and penetration testing.
Most frequently, particular operating systems are associated with particular functions. macOS comes to mind when discussing graphics or content development. Similar to this, any hacking activity or general tinkering with network utilities is associated with Kali Linux, an operating system.
I’ll be giving a general overview of Kali Linux and how ethical hacking may be done with it in this essay. There are several features provided by this technology one should use that are:
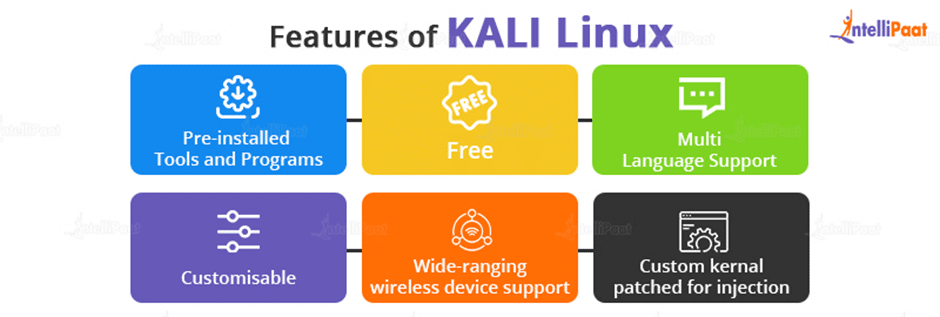
- Kali Linux has always been, and always will be, completely free to use.
- More tools than you can imagine are included in Kali Linux, which has over 600 different tools for security analytics and penetration testing.
- Open-source – Kali adheres to the well-praised open-source approach as a part of the Linux family. You can modify all of the code because their development tree is openly viewable on Git.
- True multilingual support has been included in Kali, despite the fact that penetration tools are typically written in English.
- This enables more users to operate in their native language and find the tools they require for the job.
- Completely customizable – The developers at aggressive security are aware that not every user will like their design philosophy.
- They made it as simple as possible for the more daring user to modify Kali Linux to their preferences, even down to the kernel.
Go through these Kali Linux Interview Question and Answers to excel in your interview.
Kali Linux Installation Steps
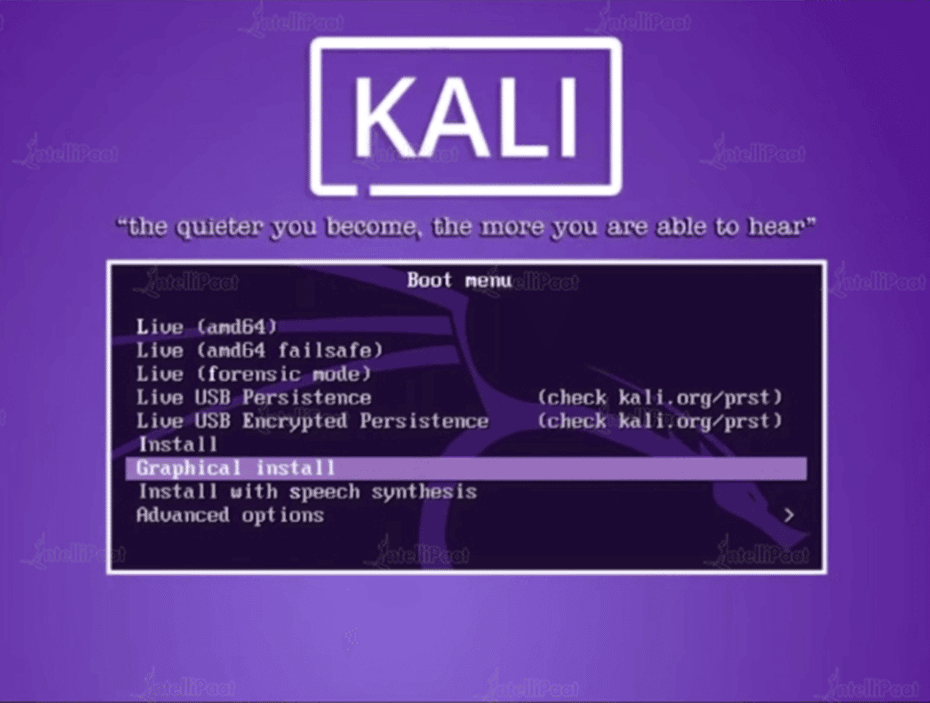
Step 1: Boot Screen
Start the installation by booting the computer from the installation medium of your choice—CD, USB, etc. The Kali Linux boot screen will appear to greet us. Here, we have the option to install in text mode or graphic mode.
Step 2: Language
Select the language of your choice. This will be utilized both during setup and after you begin running Kali Linux.
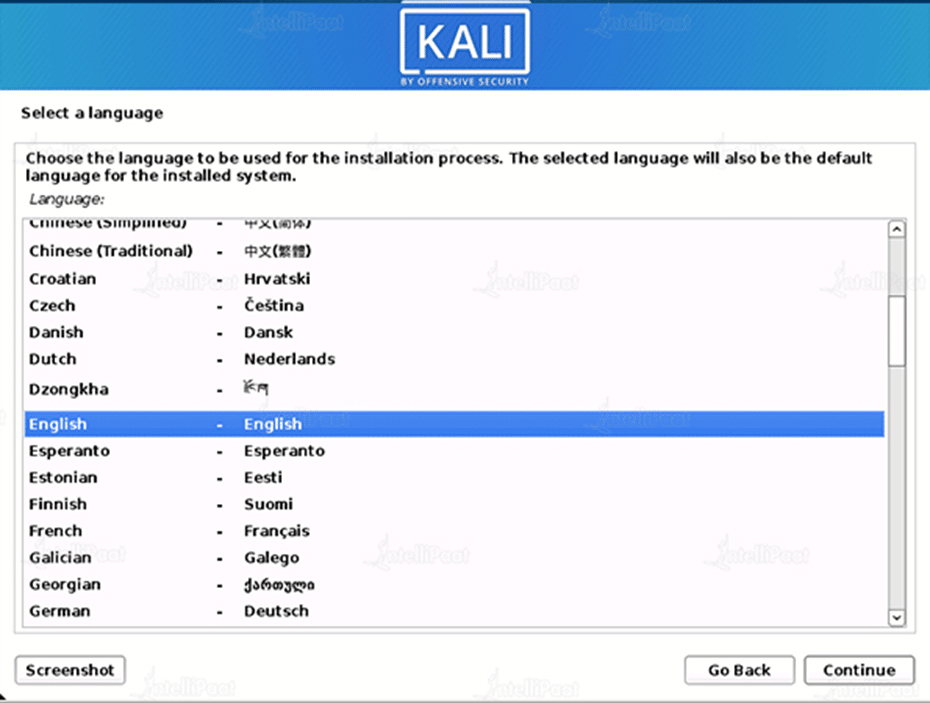
Step 3: Location
Specify your specific location
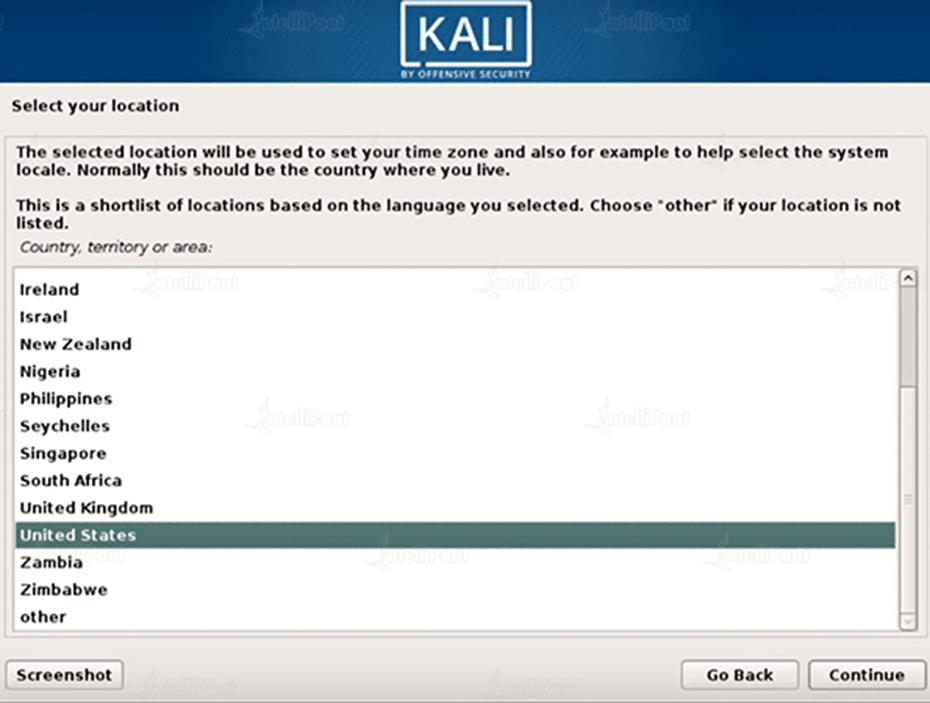
Step 4: Keymap Layout
Select your keyboard layout
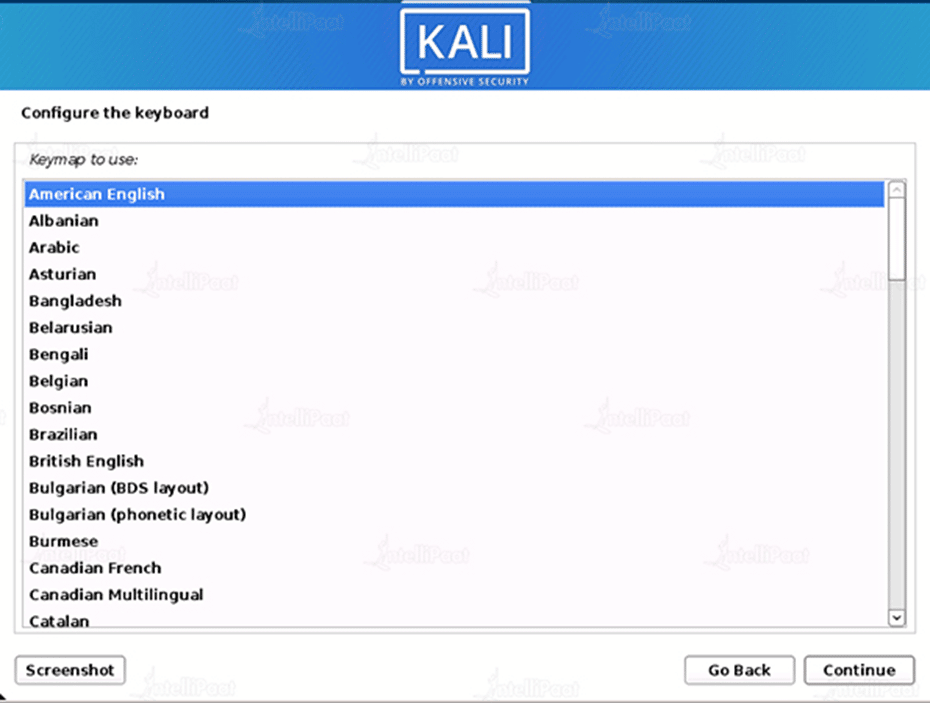
Step 5: Network
The installation will now scan your network interfaces for DHCP servers before asking you to specify a hostname for your machine. As our hostname, we’ve entered kali in the example below.
- After checking for network interfaces, it will prompt you to manually enter the network information if there isn’t a running DHCP service on the network. If your NIC isn’t detected by Kali Linux, you’ll either need to provide the drivers for it when asked or create a customized Kali Linux ISO that already has them in it.
- If more than one NIC is found during setup, you could be asked which one to utilize for the installation.
- You will be prompted for your wireless network details before being asked for a hostname if the selected NIC is 802.11 based.
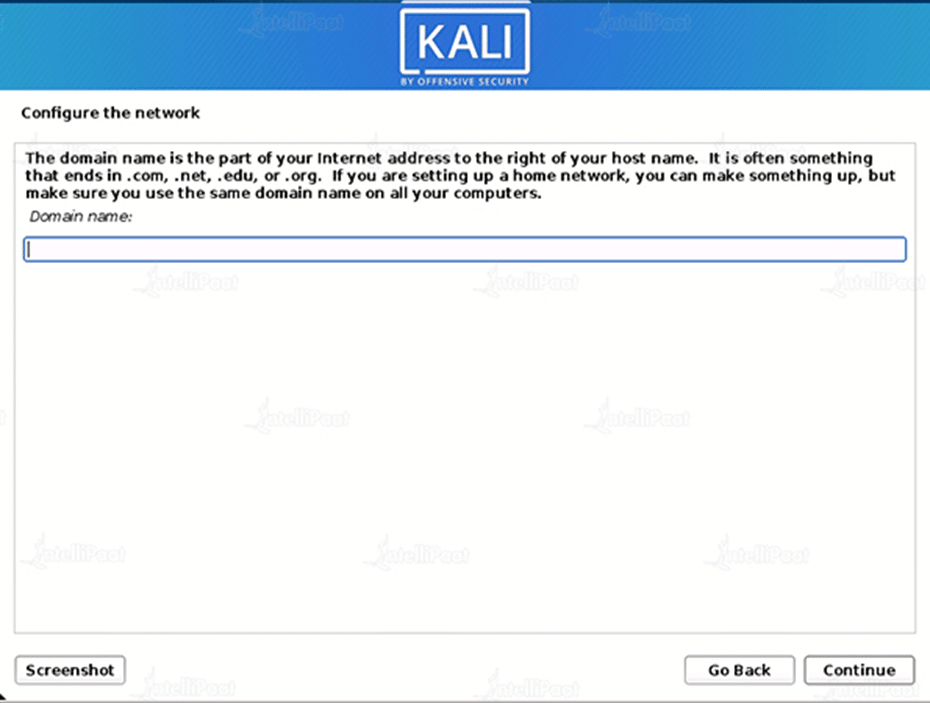
Step 6: Configure the network
Optionally, you can give this system a default domain name (values may be pulled in from DHCP or if there is an existing operating system pre-existing).
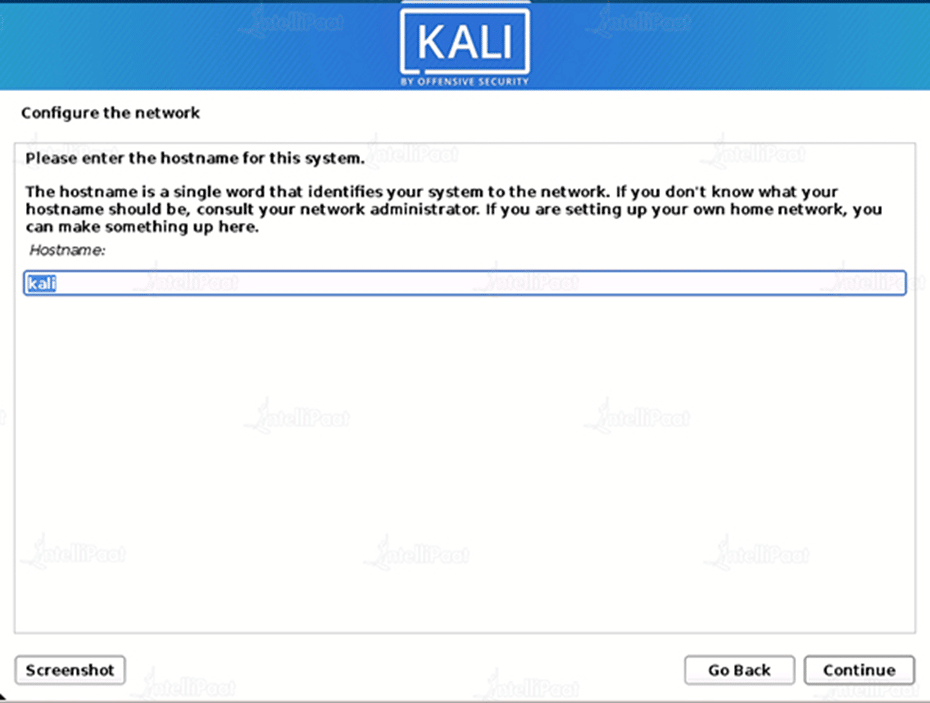
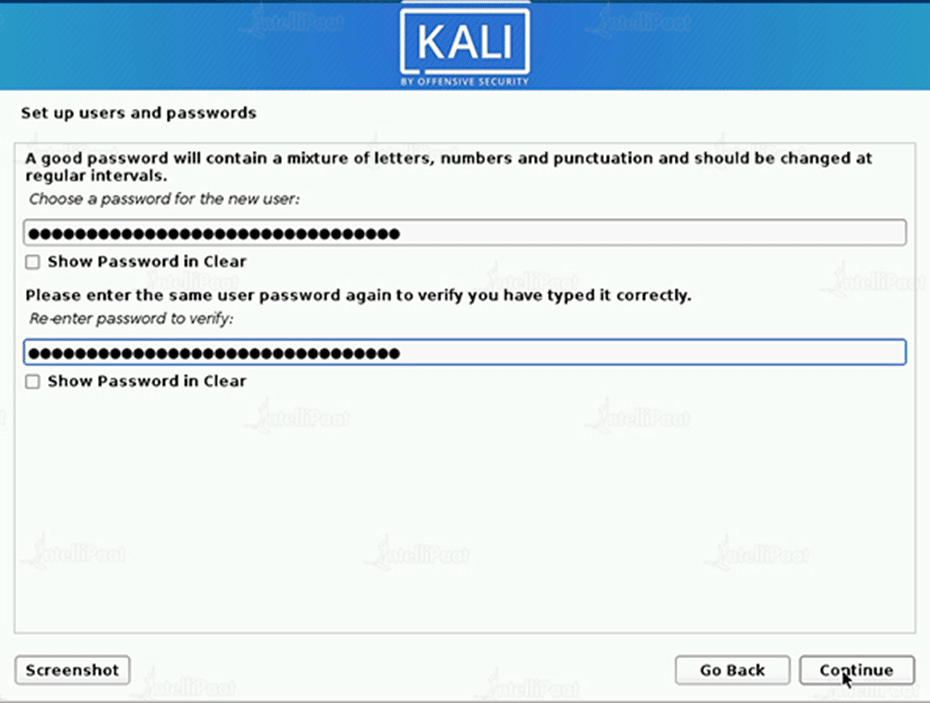
Step 7: User Account
Build the system’s user account next (Full name, username, and a strong password).
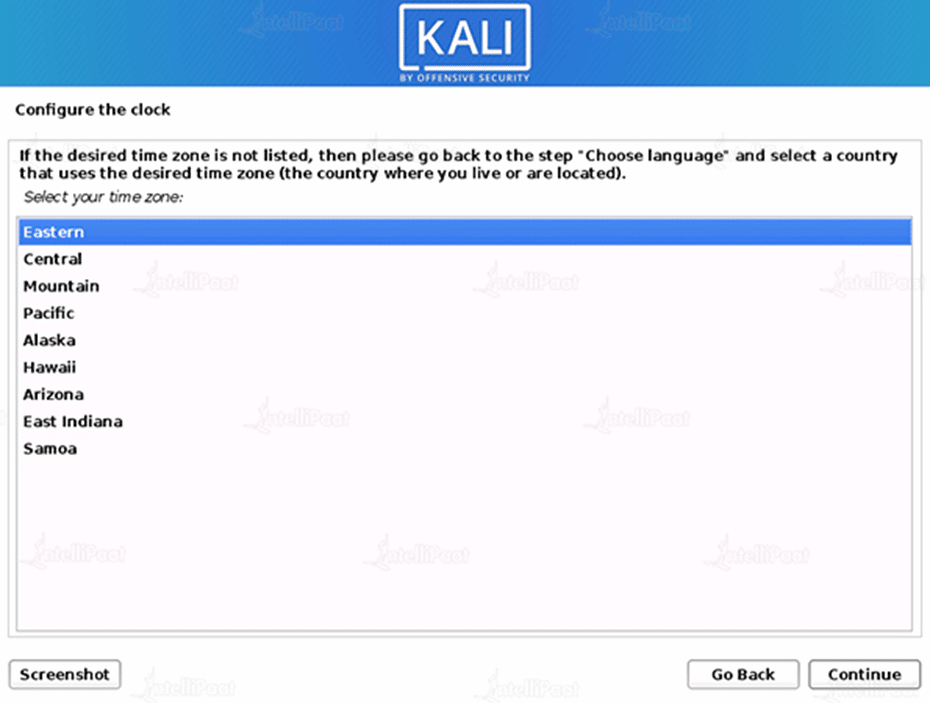
Step 8: Configure the Clock
Select the standard timezone
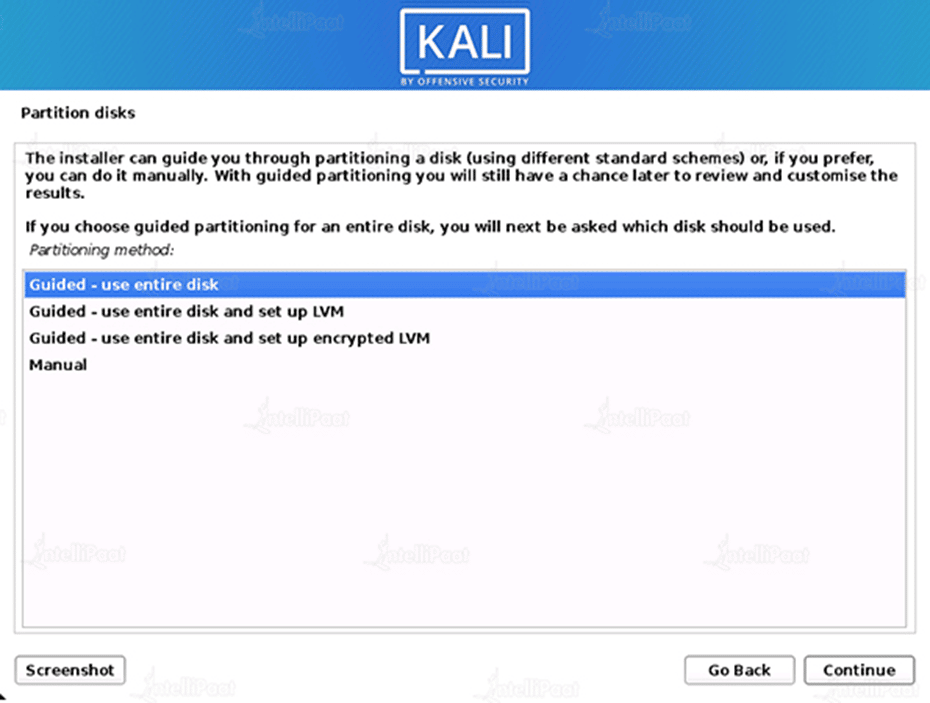
Step 9: Partitioning the Disk
- Now, depending on your setup, the installer will probe your drives and present you with several options.
- We have four choices because we are utilizing a clean disc in our guide. Since this is a single boot installation of Kali Linux, we will choose Guided – the entire drive and are content to wipe the disc since we do not want any other operating systems to be installed.
- If there is already data on the drive, you have an additional choice (Guided – use the maximum continuous vacant space) in addition to the one shown in the example below.
- This is the ideal way to dual-boot into another operating system because it tells the setup not to change any existing data.
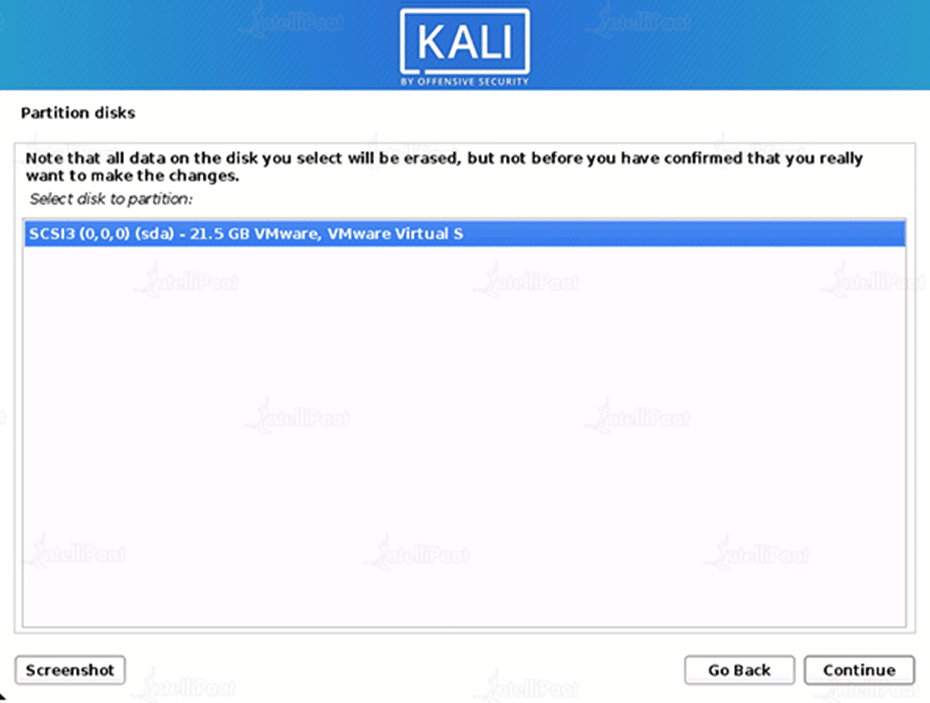
Step 10: Selection of disk to be partitioned.
VMware Virtual S disk to be selected
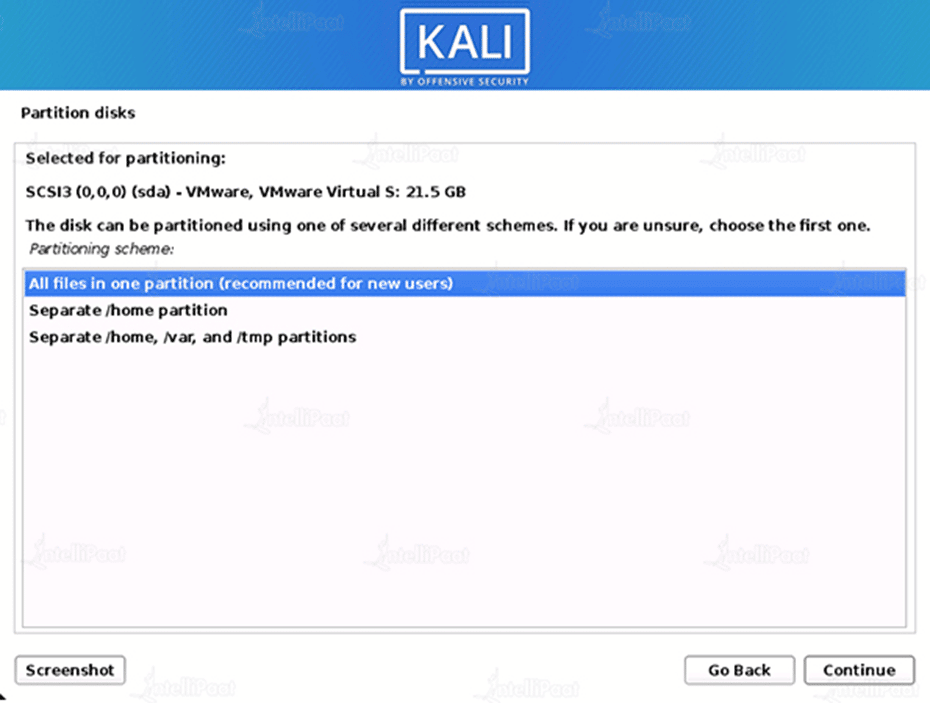
Step 11: All Files In One Partition
You can opt to keep all of your files in a single partition, which is the default, or to have several partitions for one or more of the top-level directories, depending on your needs. “All files in one partition” is what you want if you’re unsure.
Step 12: Partition Disk
The installer will then make permanent modifications to your disc setup, giving you one final opportunity to review it. The installer will begin working after you click Continue, and your installation will soon be almost complete.
Step 13: LVM encryption
Before requesting an LVM password, Kali Linux will begin to carry out a secure wipe of the hard disc if it was enabled in the previous phase. Make sure your password is strong; otherwise, you will need to accept the warning about a weak passphrase.
Step 14: Information on Proxy
You will have to input any necessary proxy information.
Step 15: Metapackages
The next step is to choose which metapackages you want to install. The default choices will install a typical Kali Linux system, so there isn’t anything you need to adjust.
Step 16: Boot Information
Confirmation to install the GRUB boot loader.
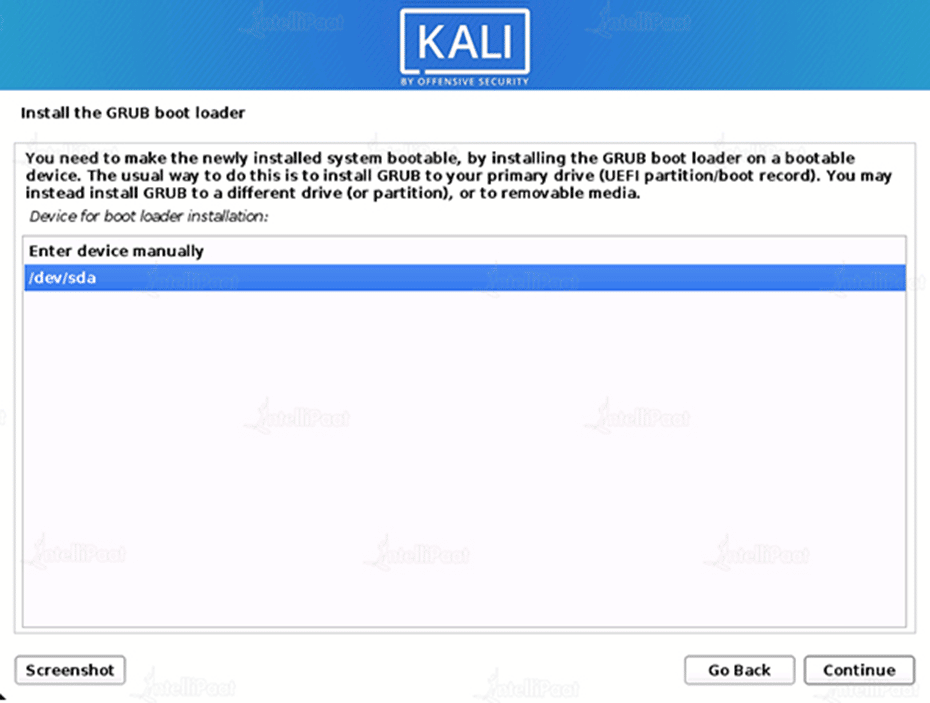
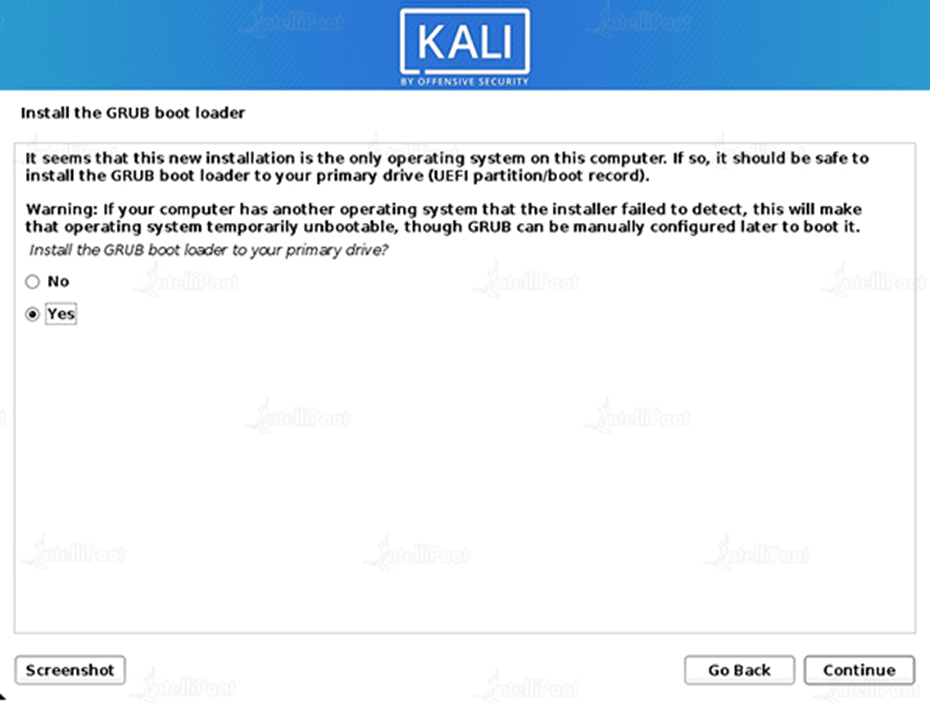
Step 17: Hard Drive Selection
Pick the drive on which to install the GRUB bootloader (it does not by default select any drive).
Check out our Cyber security courses and start your career in this domain!
Step 18: Finishing the Installation
To reboot into your fresh Kali Linux installation, click Continue at the very end.
Wrapping Up
One of the best and most well-liked operating systems for software testing, penetration testing, and hacking is Kali Linux. When it comes to testing, assessing, and auditing software or networks, it is the top option of several IT professionals, cybersecurity specialists, and white hat hackers.
The user interface and tools that Kali Linux offers are incredibly helpful for beginners to quickly grasp ideas like port detection, networking, spoofing, malware detection, and how to safeguard a network or technological infrastructure. I hope this blog helped you to get the insight you need to gain and get into the deep sea of cyber security.
Hope this Kali Linux tutorial helped you in clearing your basics, if you have any doubts, ask them out in our Cyber Security community!
The post How to Install Kali linux? Installation & Configuration appeared first on Intellipaat Blog.
Blog: Intellipaat - Blog
Leave a Comment
You must be logged in to post a comment.