Fight fraud and data breaches with advanced authentication
Blog: Capgemini CTO Blog
With the number and severity of cyberattacks and cyber-fraud cases on the rise, payments providers need robust customer authentication and identity access management. Today’s solutions leverage advanced techniques including biometrics, geo-location, secure element, and cryptography for end-point authentication.
Financial Services is among the industries most vulnerable to cyberattack and customer fraud as sophisticated hackers increasingly hone their ability to raid stores of customer data.
The WannaCry ransomware attack and Equifax data breach compromised the confidential data of millions of users. Because stolen data can be used to penetrate users’ accounts, advanced techniques – beyond two-factor authentication (2FA) – are now required to prevent strikes by hackers.
Not surprisingly, 81% of hacking-related breaches are the result of weak or stolen passwords, according to Verizon’s 2017 Data Breach Investigations Report. With the adoption of open banking technologies and increasing collaboration among different industry stakeholders, the potential for breaches and fraud may climb.
These days, financial services organizations need solutions that extend identity and access management (IAM) from known parties to unknown third parties. Meanwhile, appropriate controls are necessary to ensure compliance with know your customer, anti-money laundering, and counterterrorism financing requirements, as well as measures that ensure careful management of customer consent and entitlements.
Regulations, such as Europe’s PSD2 which promotes collaboration among stakeholders, have also mandated strong customer authentication (SCA), which requires advanced authentication techniques.
SCA mandates that authentication procedures use two or more of the following elements – knowledge (something the user knows, such as a password), ownership (something the user can demonstrate ownership of, including a mobile device or other item), and inherence (such as a unique biometric identifier). SCA requires authentication codes to vary dynamically based on the payment amount, the transaction payee, and the volume of transactions performed.
Multi-factor authentication (MFA) techniques involving multiple layers of defense are required to prevent account takeover. Globally, the multi-factor authentication services market is predicted to grow at a CAGR of close to 23% from 2017–2021, while the global multi-factor authentication market in the banking and financial sector was valued at $2.4 billion in 2016.
Payment firms are required to implement multi-factor authentication mechanisms with a combination of elements – biometrics, digital identity, secure element, geo-location, interoperable cryptographic keys, and recognition of user behavioral patterns capable of identifying suspicious behavior.
Advanced authentication techniques
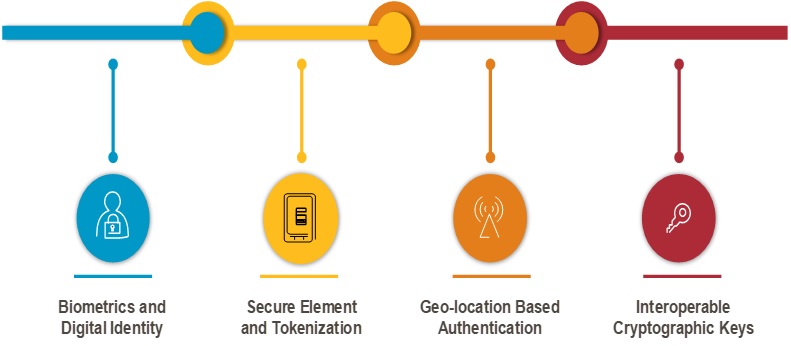
Source: Capgemini Financial Services Analysis 2018
A user’s behavioral patterns (number of keystrokes typed, gait, pressure applied, navigation pattern, and signature) in combination with biometrics can help mitigate data breaches without diminishing user experience.
New authentication technologies such as PIN on glass (POG) are also being explored for customer authentication, together with new patterns of 2FA that use advanced cryptography that can leverage the processing capability of mobile devices to secure payloads of exchange-to-exchange (e2e) transactions.[1]
Technology providers including RSA, Symantec, HID, and VASCO are already providing plug-and-play multifactor authentication and behavior recognition solutions for payment firms.
Central authorities in countries such as Israel have mandated banks to implement MFA, and First International Bank of Israel developed its plan by collaborating with US-based FinTech firm Transmit SP.
Interoperable authentication standards – SWIFTS’ 3SKey, Fast Identity Online (FIDO), and Google Authenticator – can result in tougher as well as safer authentication when linked to an individual’s device. A fit-for-purpose assessment that comprehensively explores each of these advanced authentication techniques should be evaluated continually, however, in light of the potential for severe downside risks.
To learn more about how advanced authentication can help secure your business, connect with me on social media.
[1] Pin on Glass (POG): An emerging payments technology that eliminates the need for bulky and expensive hardware, such as credit card readers. Instead of using a standalone terminal at the point of sale, merchants can use pre-existing smart devices, such as a mobile phone or tablet, to process in-store payments.
Leave a Comment
You must be logged in to post a comment.








