ELI5: How Does the Dark Web Work?
Blog: Enterprise Decision Management Blog

In our blog series exploring application fraud, we have discussed the explored the drivers behind the rapid acceleration of identity-based fraud and the considerations that must be balanced in setting a fraud risk appetite. However, one topic we have not yet broached is the convergence of fraud and cybersecurity.
We frequently talk about how PII data from data breaches is for sale on the dark web. But I think people use the term “dark web” without really knowing what it is. I’m hoping to help level set for the non-techies: When we talk about brute force application fraud and bot-net attacks, what are we really talking about?
To that end, this blog post is an interview with security specialist Coy Cardwell, who provides some insights into the world of the dark web.
ELI5 (Explain like I’m 5): What is the dark web? If I wanted to go on the dark web, how would I do that? Are you really anonymous?
The dark web sounds like some comic book buzzword, right?
In my opinion, the terms “dark web” and “deep web” are often used inaccurately. So, for clarity and brevity, I am going to use the phrase DeepDark Web in this discussion. Hang on tight, I don’t have a whiteboard.
At the most basic level, the “dark” part of the Internet is the network infrastructure itself: routers, servers and other equipment connected to and part of the Internet. Much of the physical structure of the Internet was purpose-built, originally, meaning a circuit board was made to do a specific thing and nothing more, like a highway sign. As these components scaled, many have had larger “brains” in the form of onboard computers added; think of the electronic billboards on highways that used to be static signs and are now large video monitors. Components have become more versatile and that means they also become more vulnerable to unintended usage.
Because many Internet components push around email and other data for us humans, these machines have Internet Protocol (IP) addresses — the “phone numbers” for machines that want to talk to the Internet. People don’t use these numbers, they use domain names such as www.fico.com. If you want to go to a website, your device asks the Internet’s phone books what the website IP address is; this technology is called Domain Name Service (DNS).
So, in many ways, the DeepDark Web can be defined as machines that have IP addresses that are not in the public DNS system that most Internet users access. For the most part, low-level machines running the Internet do not have entries in DNS databases because typical Internet users have little reason to browse the information on the firewall that protects www.fico.com. For example, firewall.fico.com will not work, as that address in not linked in the Domain Name Services (DNS). A firewall still exists and it has a valid, working IP address for the Internet, but it has no entry in the phonebook; technically, it is part of the DeepDark Web.
This is probably not the version of the dark web you have heard about or came here to read about. I bet you want to read about all the hacking and the super-secret websites hidden in the crusty corners of the Internet — this is where it gets interesting.
Many of the devices I am writing about that run the Internet without ever being part of the public phonebooks, aka DNS databases, are fully capable of hosting and distributing data and services both benign and malicious. After all, these are the same machines that run the Internet you access every day. Hackers of yesteryear had to understand at a deep level how these machines worked; today much of that knowledge has been codified so a technical neophyte can become a hacker by downloading free and ‘commercially’ made toolkits.
Using these layers of existing technology, bad actors do all sorts of things, but these machines are still accessible by the public Internet and therefore not always reliable to host malicious hidden activities.
Thus, the deep web, in essence a subset of the dark web, came into being.
People have hijacked some components attached to the Internet, and built new components, to create another Web within the Internet, through encrypted networks. Think of it like the plumbing and electricity of your city’s infrastructure; while water and electricity flow through the pipes and power lines, there are other things being transmitted over the same infrastructure, separate from the intended use, like people using old mail-tunnels under cities to move around undetected, or just ride the same subway as everyone else, but with criminal intent.
The DeepDark Web has Internet phonebooks, specially crafted browsers and other software so that bad actors can interact with each other, unseen by typical Internet users. Anonymity, to a degree, is key for these types of bad actors to flourish.
The tools used for traversing and interacting with the DeepDark Web typically enhance the user’s anonymity to a great degree. Ever heard of Tor? (By the way, this link goes to Wikipedia, not the place your IT department will ask questions about across a table). This Onion Router is a project to allow machines to collectively create a network within the Internet built specifically to foil an investigator from finding an end-user’s actual IP address, allowing for more anonymity. However, true anonymity on the Internet is not as easy as it might sound. If a nation-state wants to reveal your identity, it is not impossible.
How do the bad guys actually sell data from breaches on the dark web?
They set up professional websites, just like anyone else in today’s world that wants to sell things! In fact, products and services along with the websites that sell them on the DeepDark Web are often very competently and professionally built and maintained.
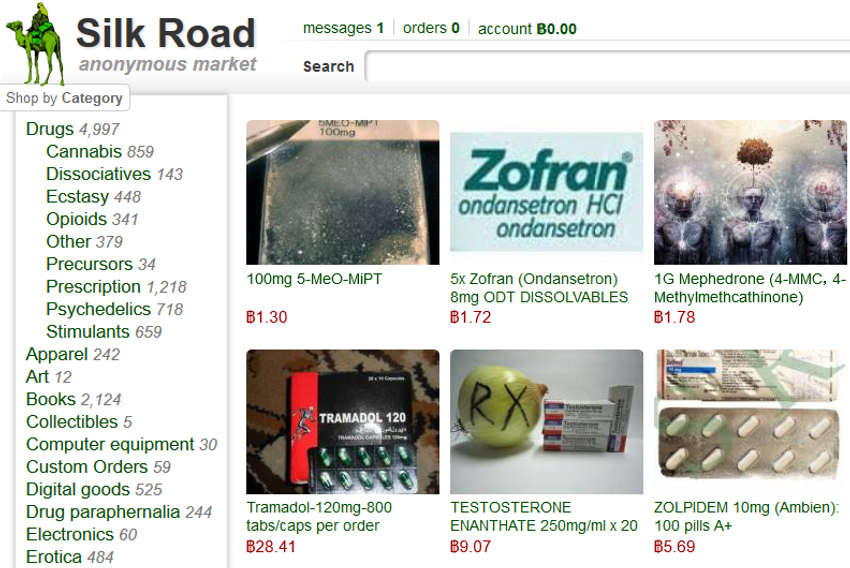
Data is often housed on servers hiding in plain sight, that are connected to the public Internet, allowing the servers and data to be accessed without the end-user ever knowing the real location of the data; obfuscation techniques and encryption technologies help enable (mostly) anonymous access for the servers that house the data and the bad actors buying the data.
In many ways, it is very similar to using a corporate VPN. Once connected, your traffic might go to a number of destinations, but the real IP address endpoints and routes become obfuscated to an outside eye.
So, once connected, a savvy DeepDark Web user can browse for all sorts of things, from credit card data to illicit drugs. Much of the DeepDark Web has been invite-only for a long time, but sellers want to make money and criminal organizations have expanded their advertising. Public internet web searches can lead you to Internet groups that, in turn, can lead you to the DeepDark Web. It is not hard, but I don’t recommend it. At all.
In a similar vein, what is a “bot-net attack”? What does it have to do with application fraud?
Bot-nets are collection of devices that have been hijacked by a bad actor. These may be PCs, wireless routers, mobile phones or internet-connected televisions and cameras; if it has an IP address and it can stream out data, someone is trying to hack it.
Using some form of technique to control the devices captured – there are many such technologies – the bad actor instructs the devices to do something to a website or service, en masse. The idea of the bot-net attack is to overload the website or service and make it vulnerable by sending it so many requests it becomes unstable.
There are many possible outcomes to a bot-net attack, including the feared DDoS attack (Distributed Denial of Service). The most basic outcome is that the components that make up the website or service being attacked simply break and no longer perform any of their intended functions, rendering the website or service inoperable.
However, in a coordinated application fraud bot-attack, bad actors are submitting applications en masse to do things such as opening a bank account or establishing a line of credit. This type of targeted attack is typically done by very sophisticated actors, attempting a very specific outcome – making money.
Whose job is it to stop brute force application attacks?
The job of security falls to everyone involved. Questions of this nature are often geared toward finding who to blame when things go wrong. People want to blame the CISO or perhaps the security engineer who installed or didn’t patch the product that got hacked. In my opinion, the only ones to blame are the bad guys, unless the people involved have been negligent. Security, Fraud, Line of Business, and IT have to get everything right, every single time, but a hacker just has to get it right once; don’t blame the victims.
What can I do to protect my organization from a brute force application fraud attack?
The only way to approach effective security is to build layers of defense. In security, there is no single technology or technique to rule them all. Security is built out at each layer of the process of handling data, each part of the security process playing a role to ensure data and component integrity.
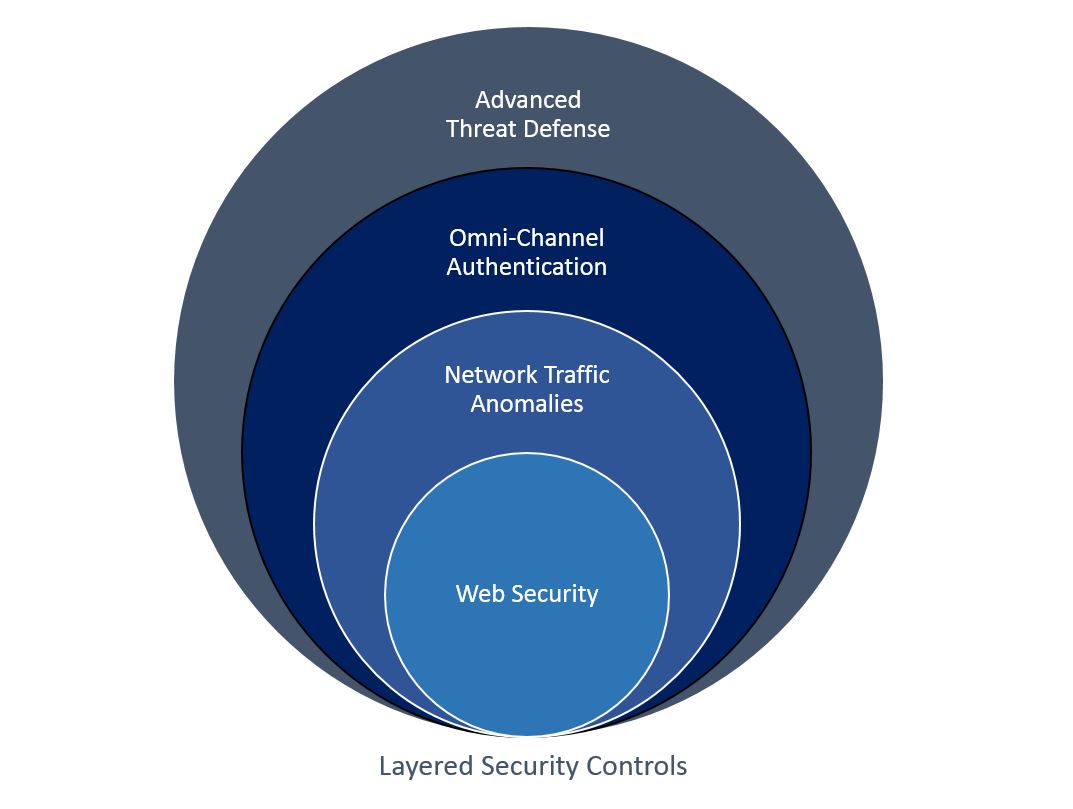
Underlying security/software controls, built-in as part of the routers and firewalls, control the first level of defense and attempt to ensure only properly formatted data traffic is transported. There are software packages for Internet components that help with application-based attacks by teaching the machines what proper application traffic should look like.
However, if the traffic looks legitimate, it will go through to the application and during a real-life brute force attack, the traffic could be manipulated to look legitimate, especially when encrypted and harder to monitor. For instance, if a component watches for traffic from specific IP addresses, the ones it knows are approved, and one of the IPs is behaving badly, the traffic can just be ignored pretty easily until fixed. In a real-life fraud application attack the network traffic could come from many places and look legitimate.
Just before data enters a system to begin actual workflow through business processes, another layer of security is invoked in complex applications, generically referred to as data validation. This validation can take many forms, from controls to dropping all requests past the number the application is known to be able to handle, to forcing authentication to detect account hijacking, to full decrypted data inspection with models to prequalify application requests.
When the services being provided are open to the entire Internet, security is a larger problem, while with only a few valid clients for the services, it becomes easier. If there is legitimate traffic from all over the world, the routers treat it like just a really busy day, and try to get that traffic through. This leaves only the service itself — such as a credit card application system — to fend off bad traffic. No amount of network-level traffic security will be able to determine if the content —names, addresses, other PII — is valid for the services in question to process.
At FICO, our Application Fraud Solution uses machine learning advanced analytical models and sophisticated fuzzy matching and entity resolution technology to fend off all sorts of brute force application attacks. It uses simple rules that ensure data integrity – does the input data contain valid, printable characters, or system commands? It also looks at KPI information that can indicate fraudulent activity – is this identity stolen or has it been used hundreds of times? And it uses machine learning security to prevent attacks through rapidly detecting patterns — this is part of the FICO pedigree.
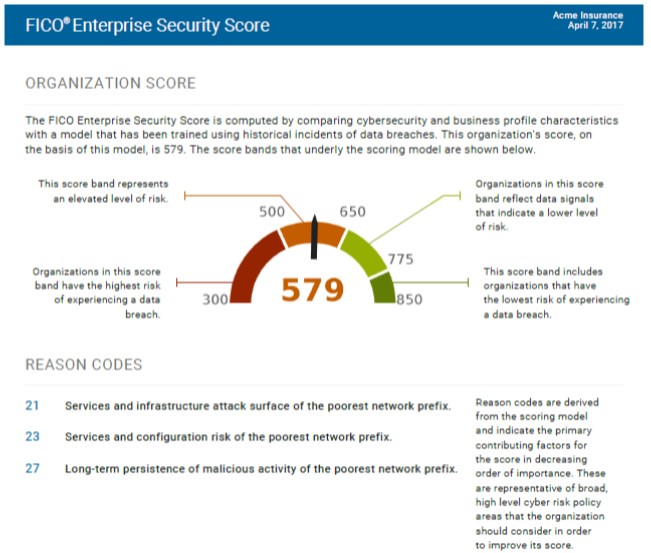
Also, with the advent of the FICO Enterprise Security Score (ESS), security can be enhanced on an entirely new level, in a predictive fashion. Now it’s possible to get alerts when your network or assets are looking vulnerable to third parties.
 Thanks for sharing all this information, Coy. Before we end, and perhaps I’m showing my cynical side as a counter-fraud expert, but tell me: Who are you, and why should we listen to you?
Thanks for sharing all this information, Coy. Before we end, and perhaps I’m showing my cynical side as a counter-fraud expert, but tell me: Who are you, and why should we listen to you?
I hold a CISSP certification, I have held a CISM certification, and I have personally lost sleep to protect the networks I ran with sensitive information access. The organizations I have worked for have entrusted me for years with the security of their data, both directly and indirectly, from the hardware to training executives on what not to click.
These days, I am on the team responsible for getting the word out on the Enterprise Security Score. For me, security is a lifelong passion, not just a job. By age 19, I was installing and repairing alarm residential systems. Using Open Source tools, the information super-highway, and training from SANS, I have built security systems to protect 200+ interconnections between clients and vendors, adding layers of protection to approximately one billion consumer records, including both personally identifying and personal health information (PII and PHI), and enabled law enforcement to be more effective.
I have participated in the live defense of networks with active hackers, I have cleaned up and educated in the aftermath of breaches, and I have helped fight the bad-guys. You may say I am a life-long security geek. My motto is trust, but verify!
The post ELI5: How Does the Dark Web Work? appeared first on FICO.
Leave a Comment
You must be logged in to post a comment.







